Method for taking fingerprint information as key
A fingerprint information and key technology, which is applied in the field of Internet security and data security, can solve the problems of product security risks and ignorance of the key, and achieve the effect of increasing the security of the key and the security of the generation process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0008] Further description will be given below in conjunction with the embodiments and accompanying drawings.
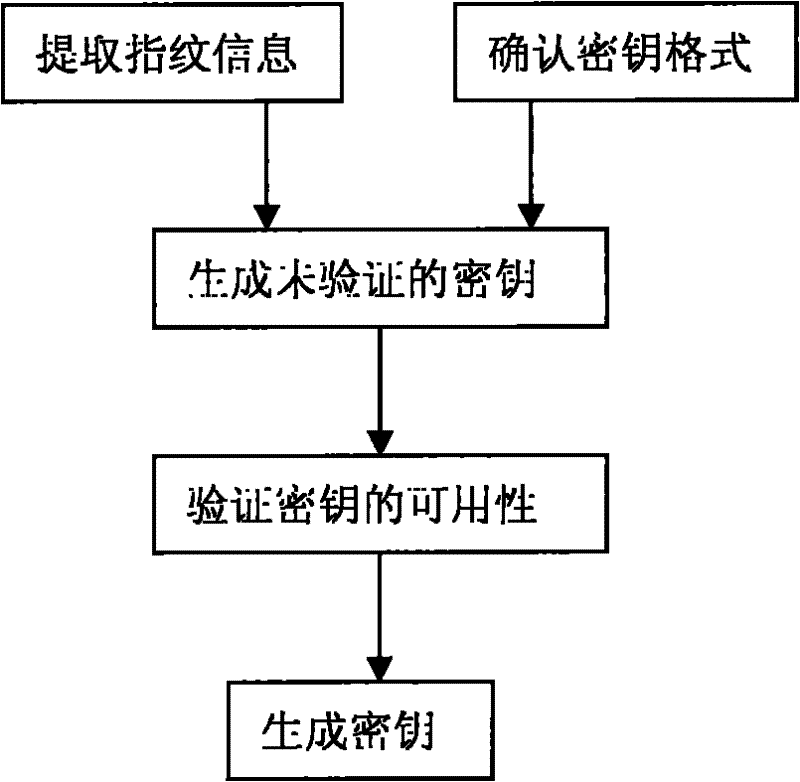
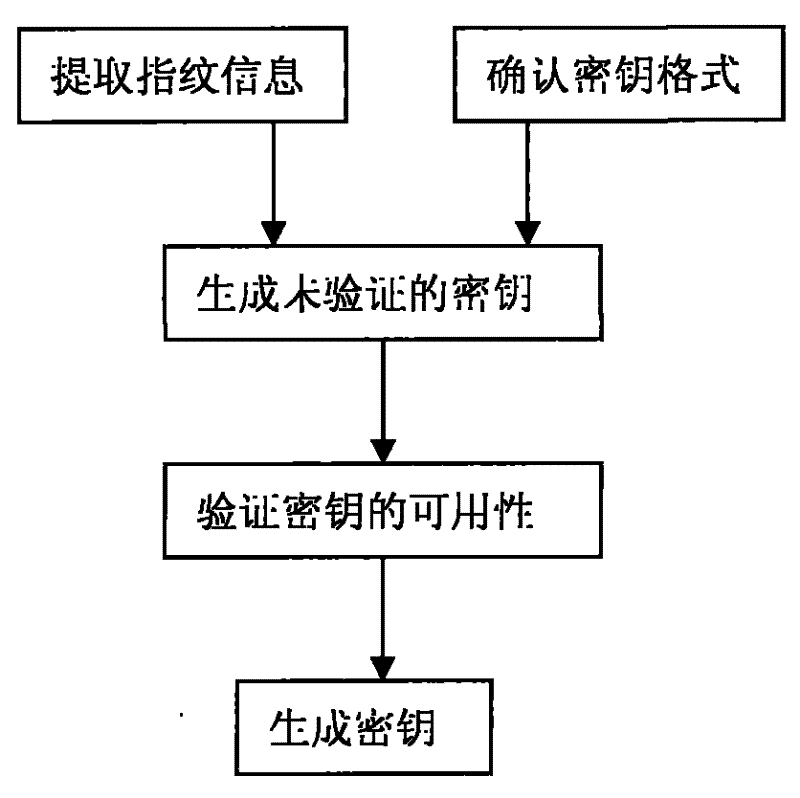
[0009] As shown in Figure 1, the present invention comprises the following steps:
[0010] (1) Extract fingerprint information: collect the user's fingerprint information on-site through the fingerprint collection device, or extract the fingerprint feature part from the file containing the user's fingerprint information.
[0011] (2) Confirm the key format: confirm the structure of the key according to the encryption and decryption algorithm used by the user.
[0012] (3) Generating an unauthenticated key: Generate an unauthenticated key from the fingerprint data extracted in step 1 according to the key format confirmed in step 2.
[0013] (4) Verification key: Apply the key generated in step 3 to the user algorithm for verification to ensure its availability. .
[0014] (5) Generate key: the key verified in step 4 is the fingerprint key, which can be used later. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com