End-to-end session key consultation method and system for supporting lawful interception
A session key and key negotiation technology, applied in the Internet field, can solve the problems of increasing the possibility of man-in-the-middle attacks, reducing the efficiency of key negotiation, and confusion of data encryption and decryption.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0118] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
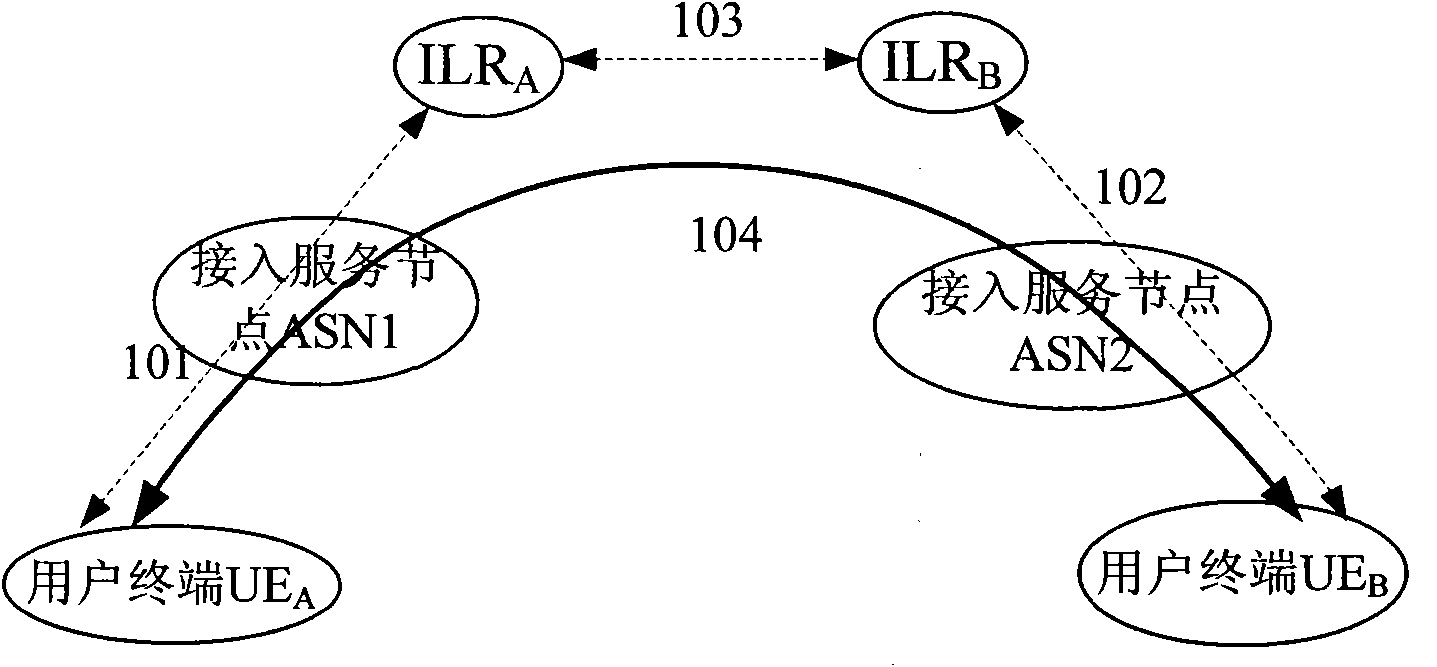
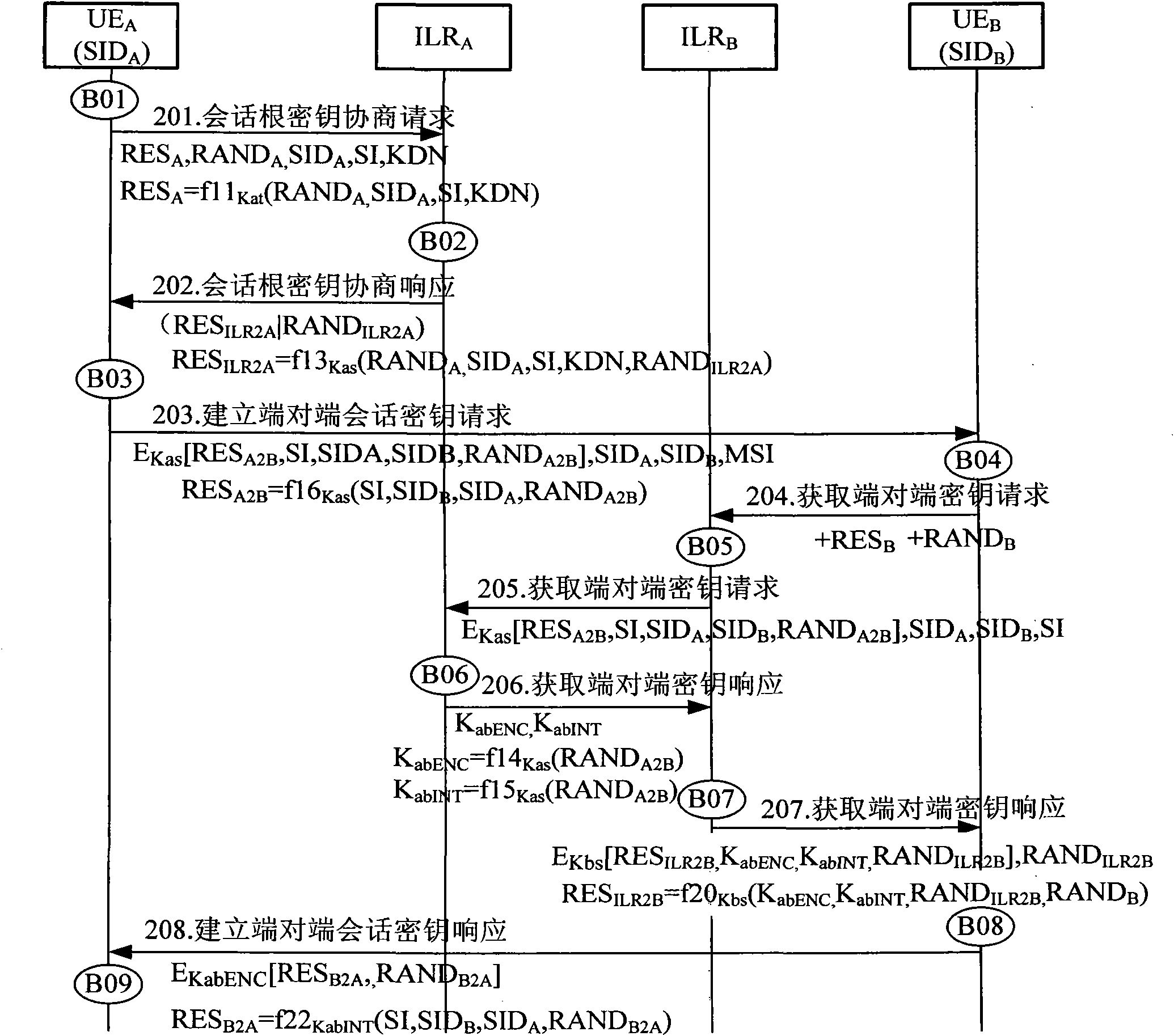
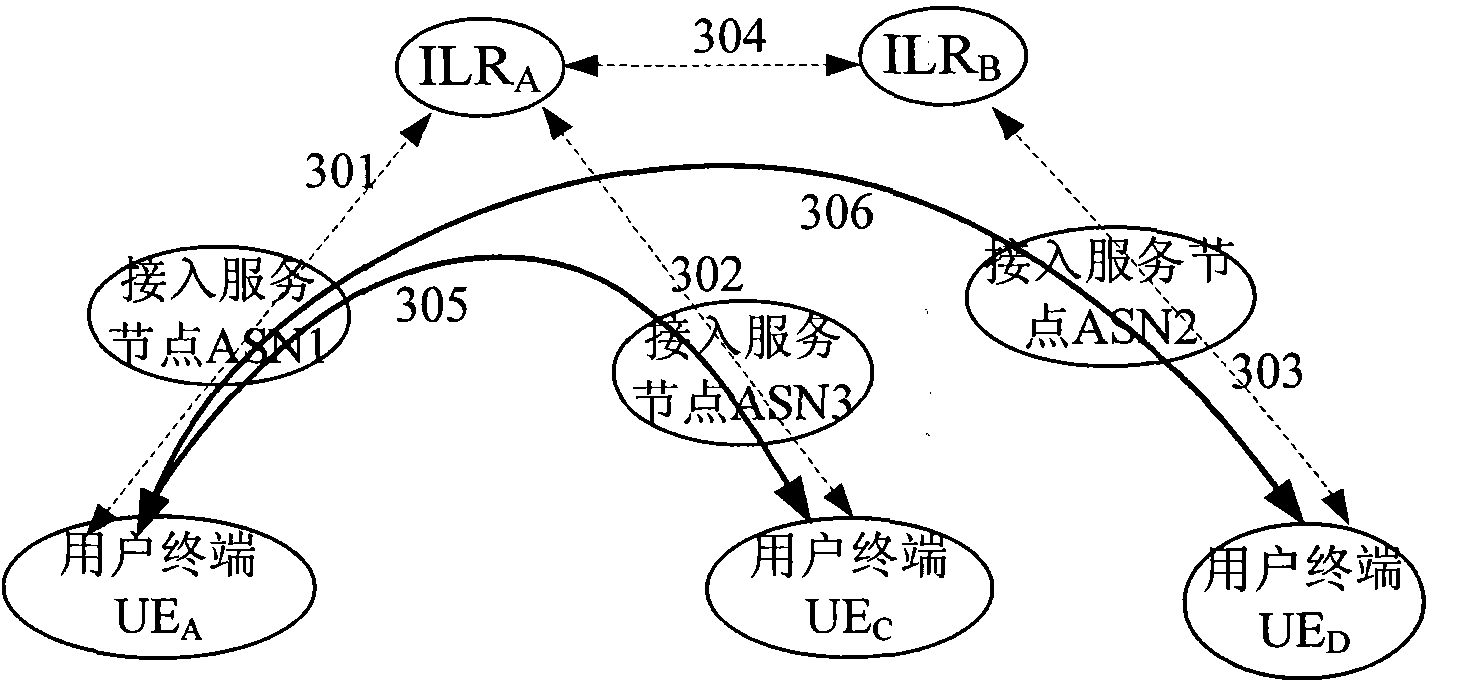
[0119] figure 1 Shown is a schematic diagram of the system architecture of this embodiment, and the system includes a user terminal (UserEquipment, UE): UE A and UE B ; Access Server (Access Server Node, ASN): ASN1 and ASN2; and Identity Location Register (Identification Location Register, ILR): ILR A and ILR B . Among them, the terminal UE A and UE B The data link between is an insecure link, such as an IP link, so the UE A and UE B The session key cannot be passed in clear text, because the UE A It is possible to communicate with one of hundreds of millions of other users at any time, UE A It is impossible to contain the pre-shared keys of all users, so UE A Cannot use pre-shared key with UE B To establish a secure end-to-end session, it is necessary to design an end-to-end session key negotiation mechanism to solve the security ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com