Source-tracing method and system for anonymous communication
An anonymous communication and node technology, which is applied in the traceability method and system field of anonymous communication, can solve problems such as invalid IP address traceability, and achieve the effect of ensuring authenticity and validity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
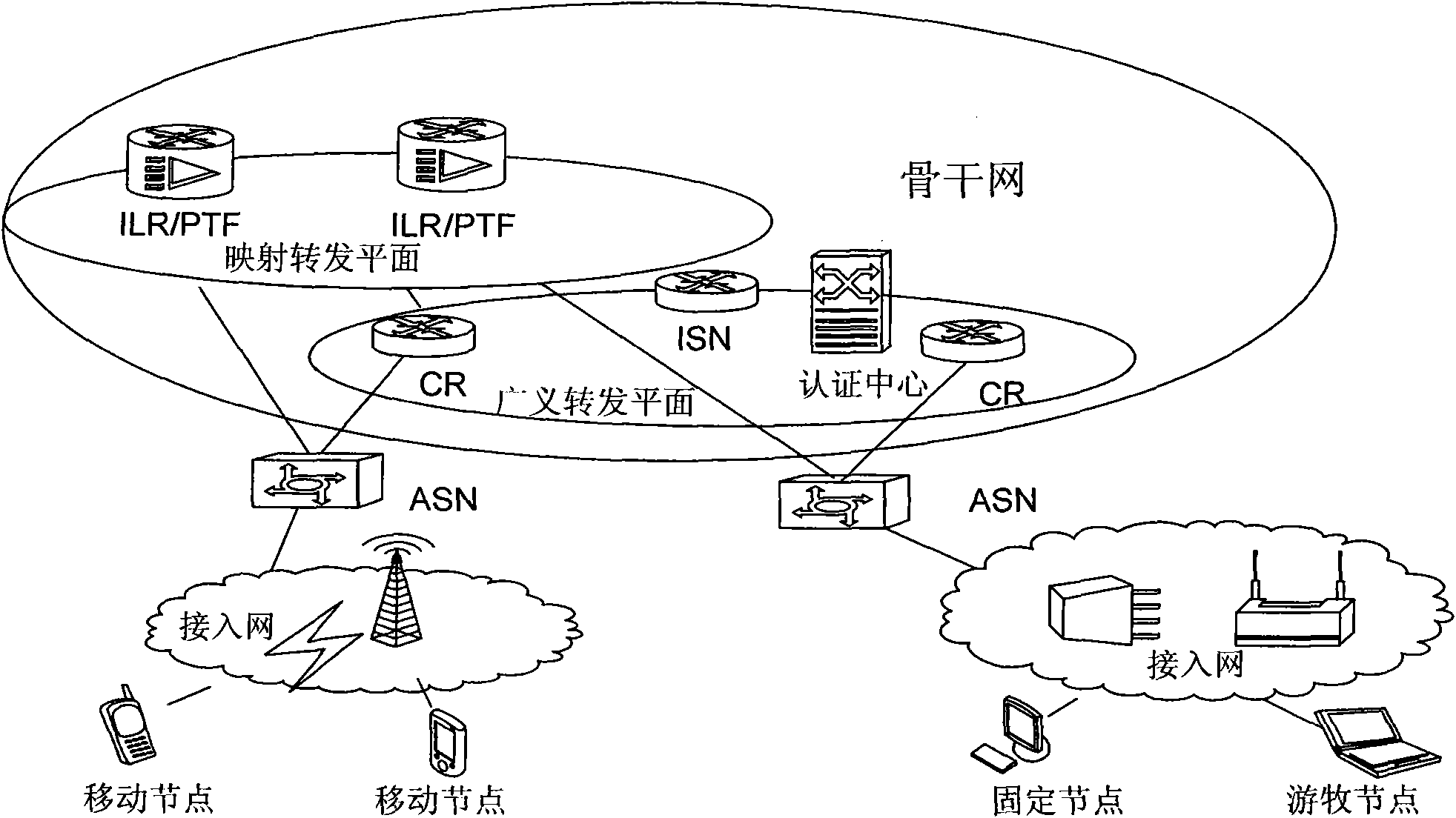
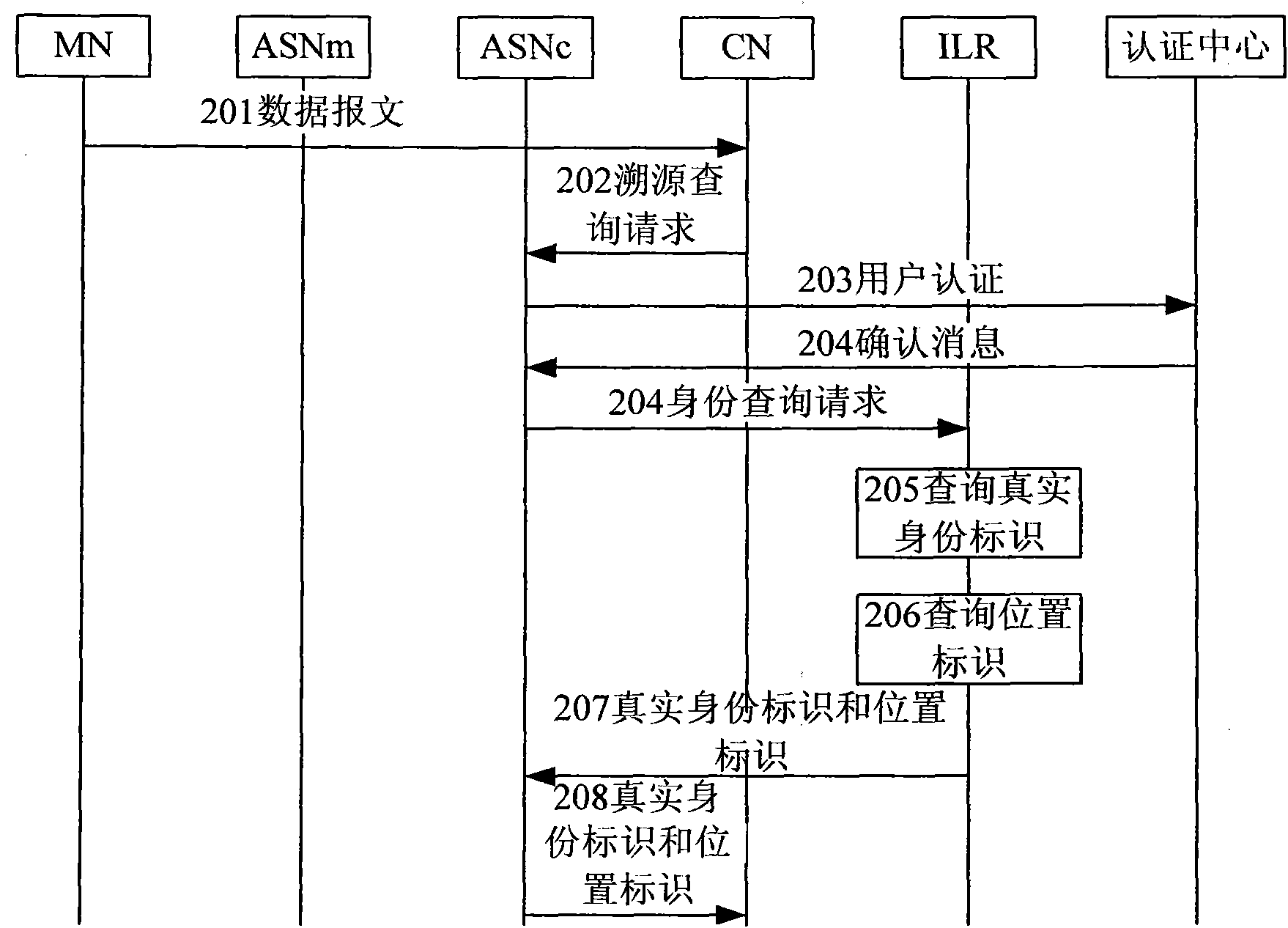
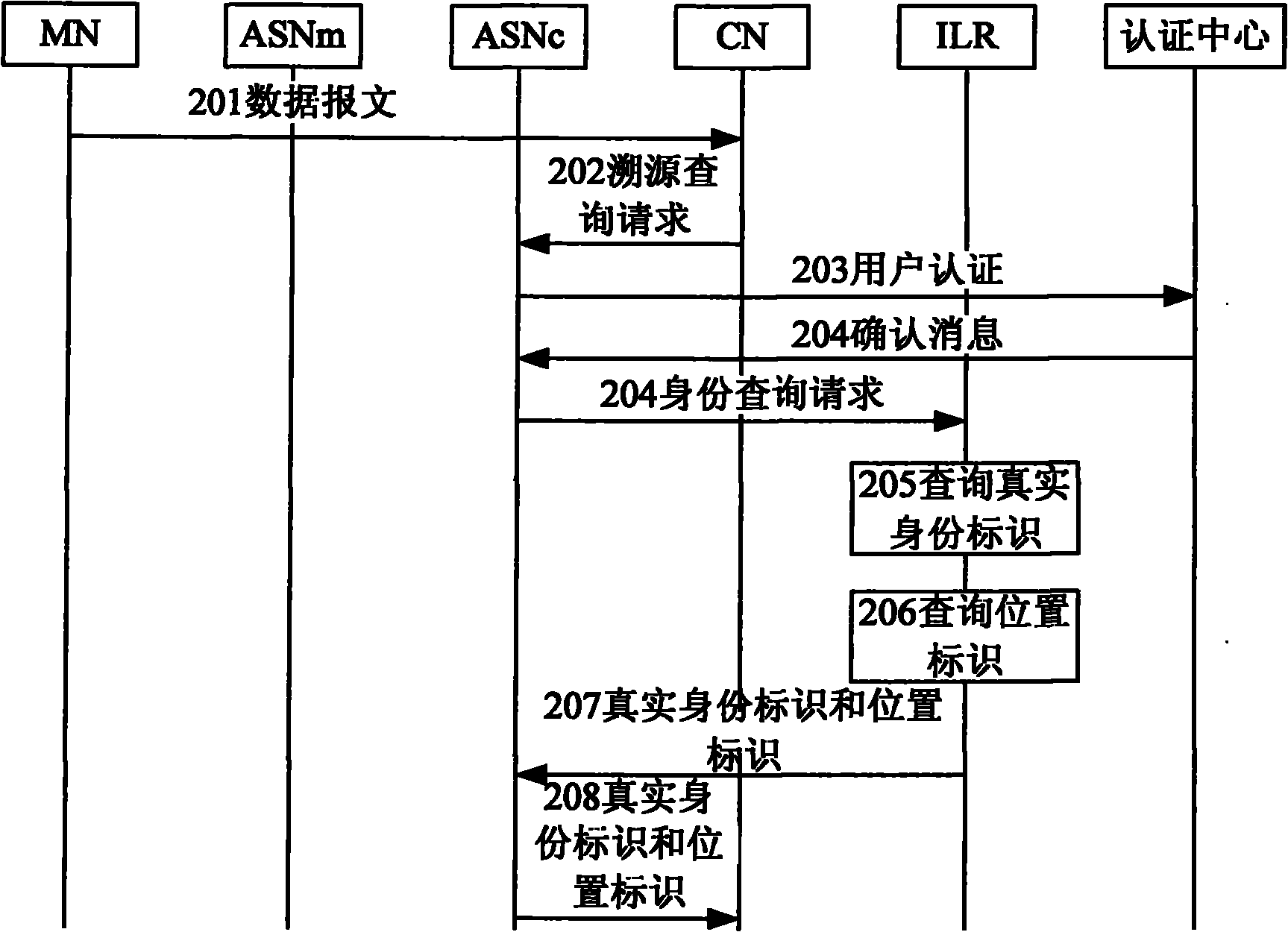
[0057] There are many network architectures based on the separation of identity and location. figure 1 It is a schematic network topology diagram of an identity identification and location separation architecture according to an embodiment of the present invention, which shows key network elements / functional entities of the system architecture related to the present invention.
[0058] Such as figure 1 As shown, in the architecture based on identity and location separation described in this embodiment (hereinafter referred to as this architecture), the network is divided into an access network and a backbone network. The access network is located at the edge of the backbone network and is responsible for the access of all terminals. The backbone network is responsible for the routing of different terminals accessed through the access network. An Access Service Node (ASN for short) is located at the boundary between the backbone network and the access network, and interfaces w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com