Hardware monitoring and micro-packet protocol-based key data restoration method
A key data and packet protocol technology, applied in the redundancy of operations for data error detection, response error generation, etc., can solve problems such as low execution efficiency, inability to perform seamless recovery, and large monitoring granularity.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
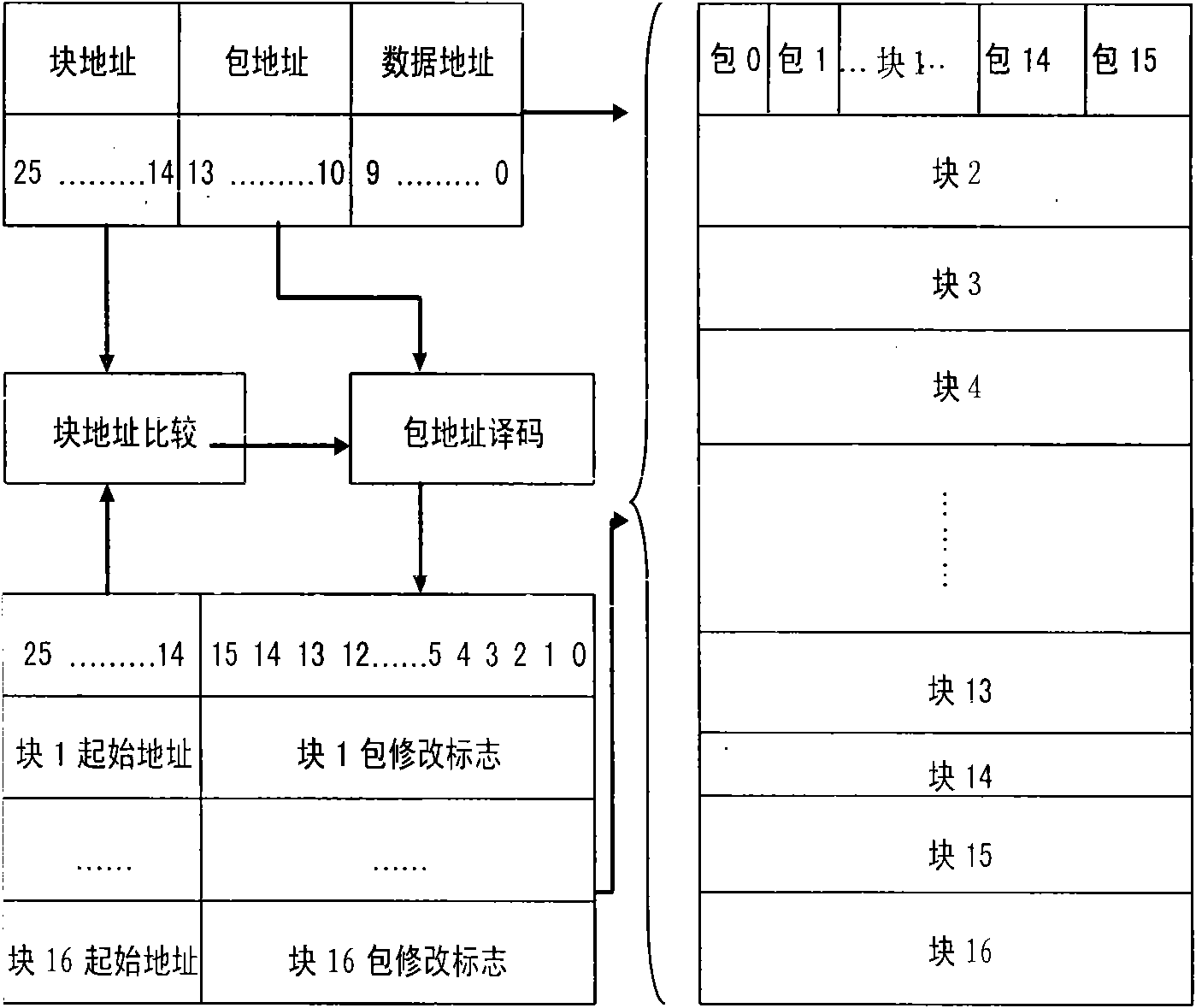
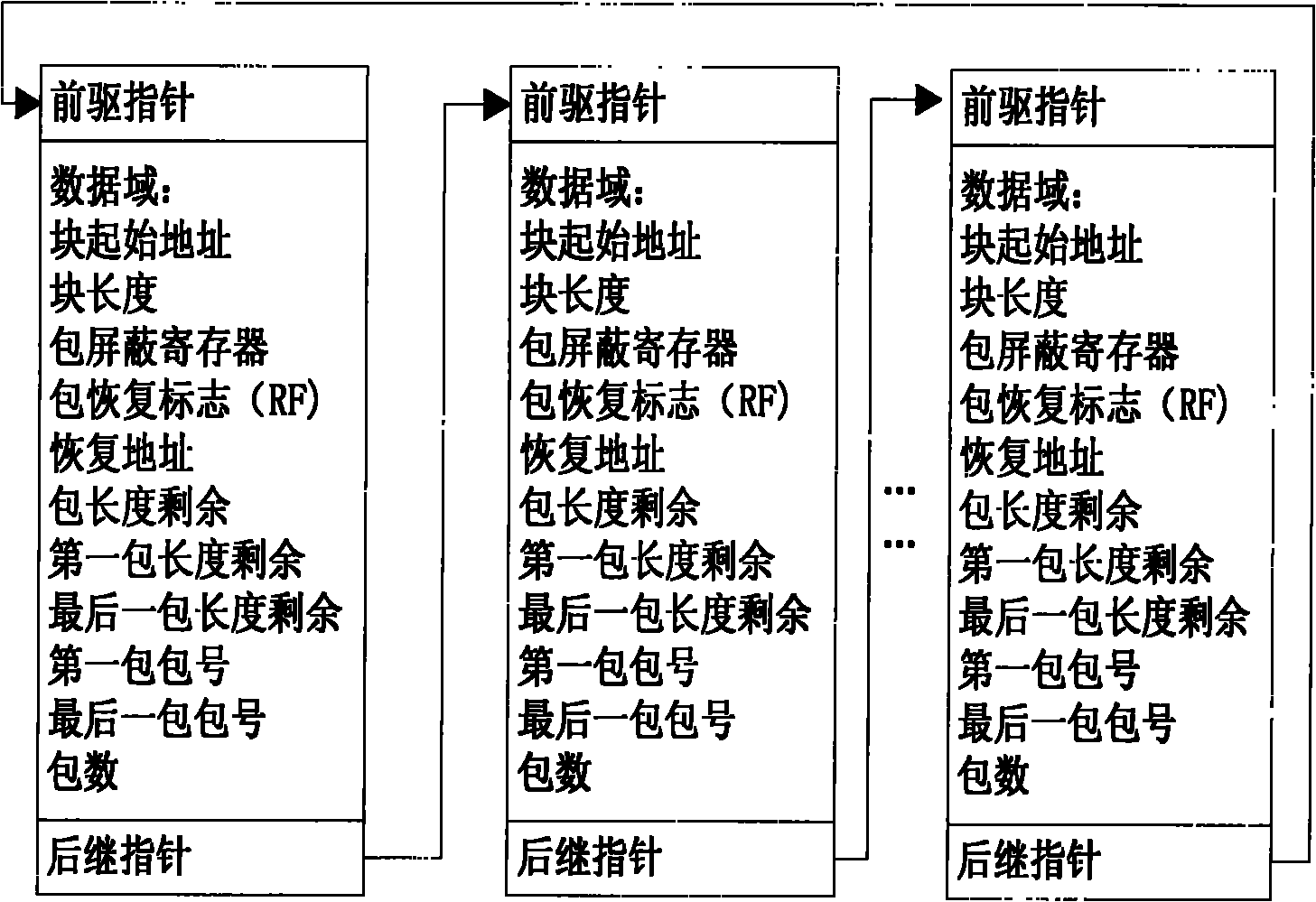
[0014] The key data recovery method in the three-mode redundant fault-tolerant computer system based on hardware monitoring and micropacket protocol of the present invention will be described below in conjunction with the accompanying drawings.
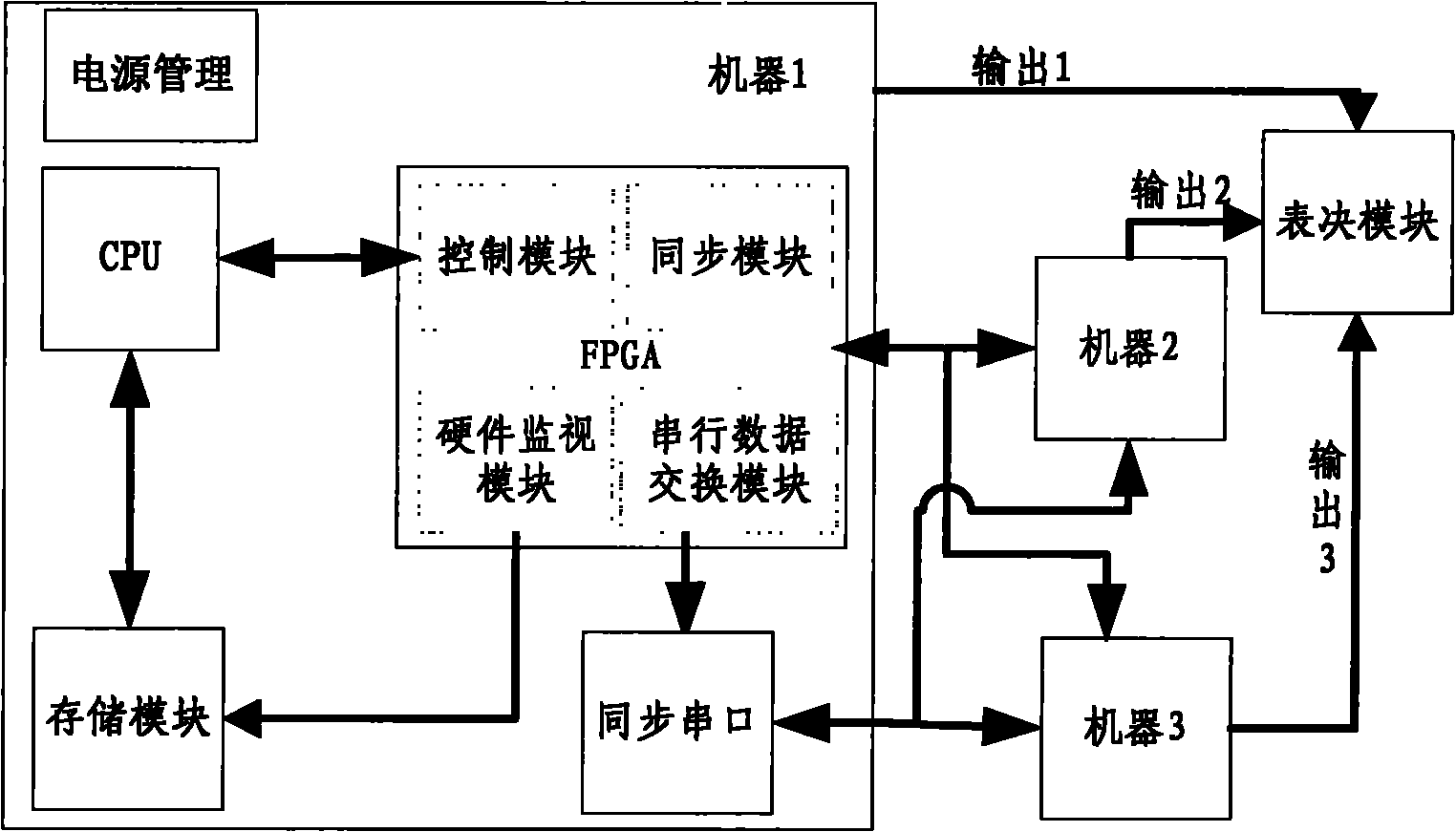
[0015] The system composition of the triple-mode redundant fault-tolerant computer is as follows: figure 1 shown. The system is composed of three identical high-performance embedded computer motherboards and an output voting module. Through the built-in tightly coupled synchronization mechanism, a triple-mode redundant computer oriented to embedded control with no single-point failure mode is formed. Among them, the CPU module is the core component of the computer mainboard. It uses a 32-bit microprocessor BM3803MG based on the SPARC V8 architecture. The three computer mainboards are integrated with special synchronization modules and serial data exchange modules. Completely independent, it can collect external input data synchronous...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com