High-efficiency dynamic software vulnerability exploiting method
A software vulnerability and dynamic technology, applied in the field of software engineering and information security, can solve problems such as impossible completion, heavy workload, relying on manual definition of abnormal data generation rules, etc., to achieve the effect of improving efficiency and increasing possibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
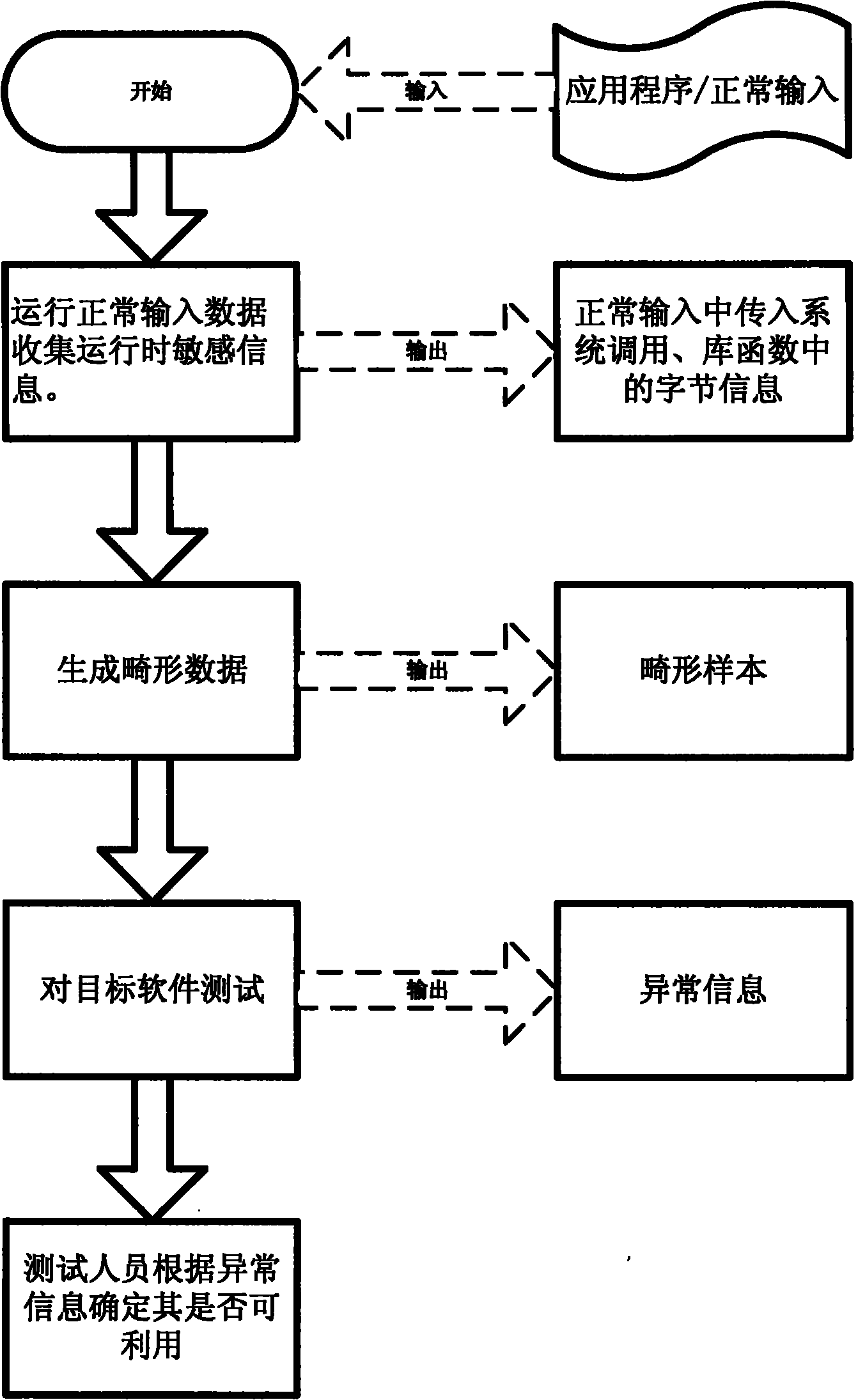
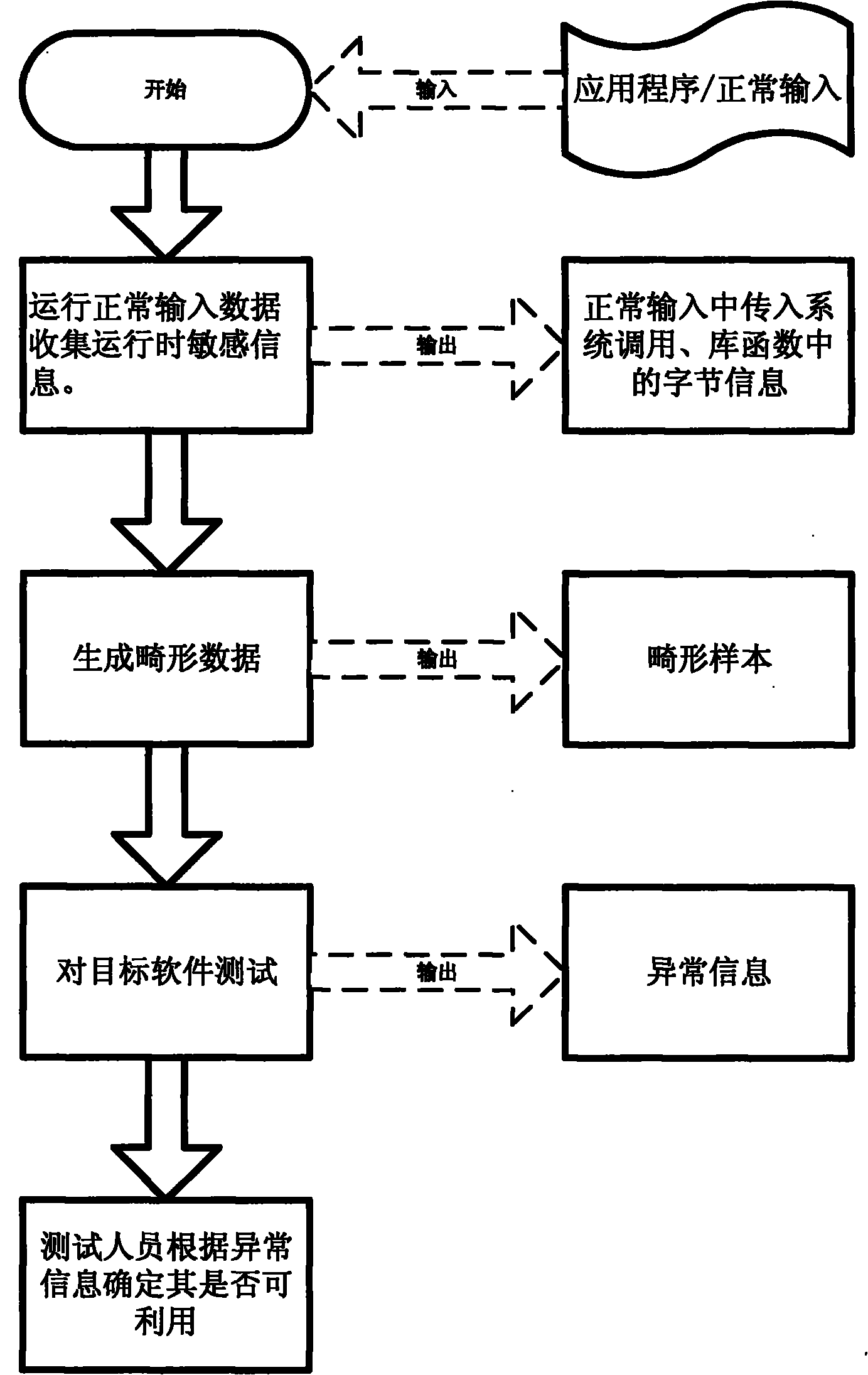
[0036] The specific implementation manner of the present invention will be described in more detail below in conjunction with the accompanying drawings.
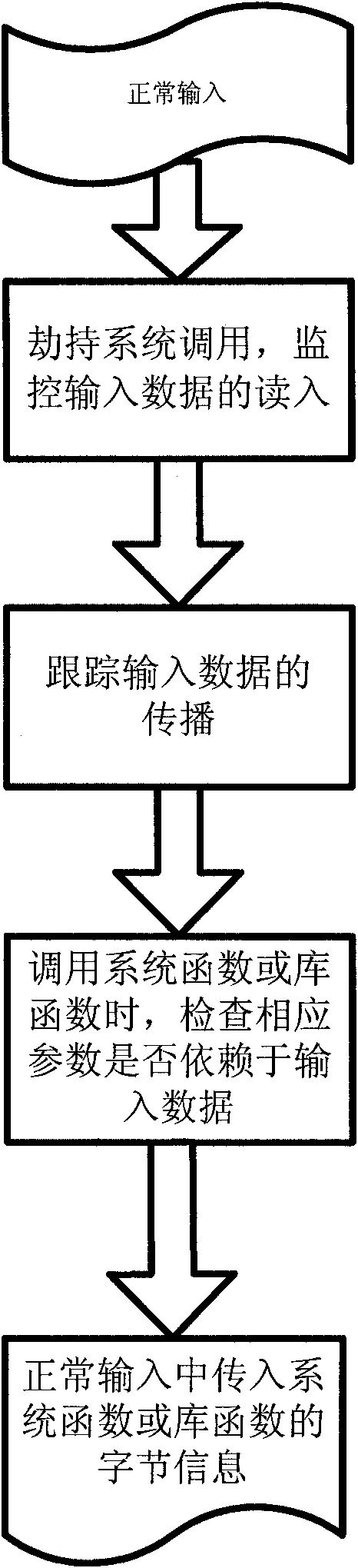
[0037] Step 1. Run normal input data, collect runtime sensitive information.
[0038] This step is based on the binary dynamic code instrumentation technology, runs the target software in the instrumentation mode, and tracks the reading, dissemination, and use of input data. It is also possible to use a binary change method or a source code code insertion method (see document [1] GeorgeC.Necula.CIL: Intermediate Language and Tools for Analysis and Transformation of C Programs.Proceedings of the 11th International Conference on Compiler Construction.2002.[ 2] Susanta Nanda. BIRD: Binary Interpretation using Runtime Disassembly. Fourth IEEE / ACM International Symposium on Code Generation and Optimization, 2006.)
[0039] The existing binary dynamic code instrumentation technology is very mature. Many famous IT companies such a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com