Security audit method and system for kernel
A security auditing and kernel technology, applied in the computer field, can solve problems such as the inability of kernel security auditing, and achieve the effect of improving security and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
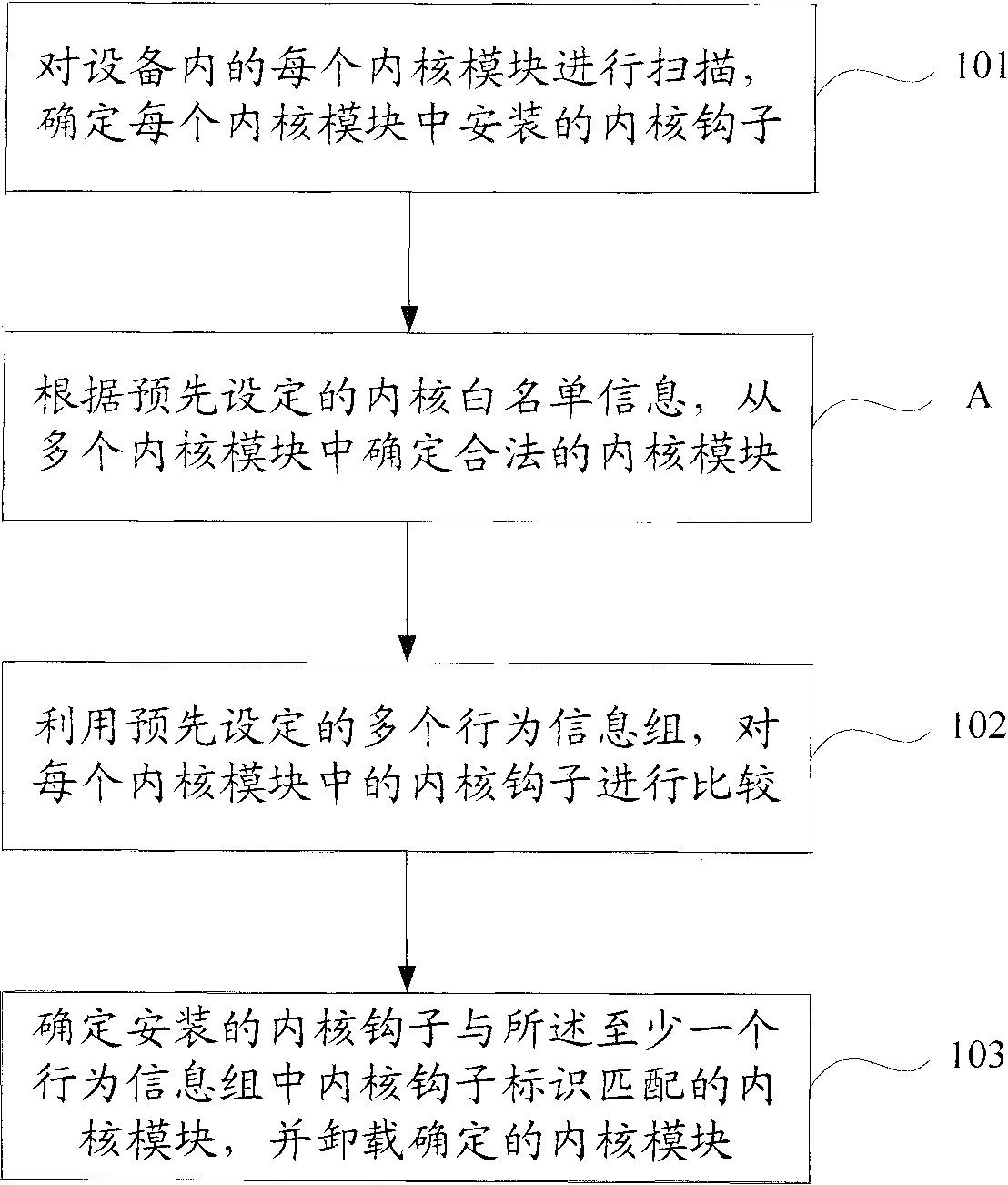
[0029] Embodiment 1 of the present invention applies the kernel anti-hook technology to the host security audit technology, and proposes a new kernel security audit method, such as figure 1 As shown, the method includes the following steps:
[0030] Step 101: Scan each kernel module in the device, and determine the kernel hooks installed in each kernel module.
[0031] The devices involved in this step may be terminal devices such as computers, or other terminals that need to perform a security audit on the kernel state of the device.
[0032] The device to be processed has a kernel system, and at least one software is installed in the kernel system, and each software can correspond to a kernel module, where the kernel module refers to a driver file (equivalent to an exe file in the application layer), in each Kernel hooks may in turn be installed in kernel modules.
[0033] In order to conduct a security audit of the software behavior of the kernel state of the device, it i...
Embodiment 2
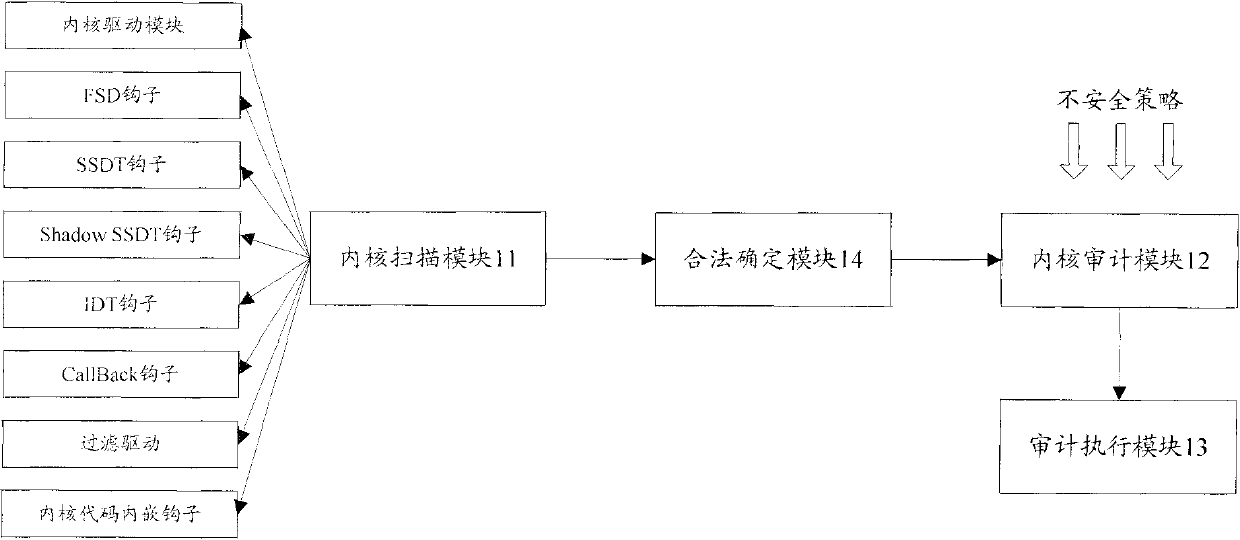
[0051] Embodiments of the present invention also provide a security audit system for the kernel under the same inventive concept as Embodiment 1, such as figure 2 As shown, the system includes the following components: a kernel scanning module 11, a kernel audit module 12 and an audit execution module 13, wherein: the kernel scanning module 11 is used to scan each kernel module in the device to determine the Installed kernel hooks; the kernel audit module 12 is used to compare the kernel hooks in each kernel module with a plurality of preset behavior information groups, and determine that the installed kernel hooks are consistent with the kernel in the at least one behavior information group A kernel module that matches the hook identifier, wherein each behavior information group contains at least one kernel hook identifier; the audit execution module 13 is used to unload the kernel module determined by the kernel audit module.
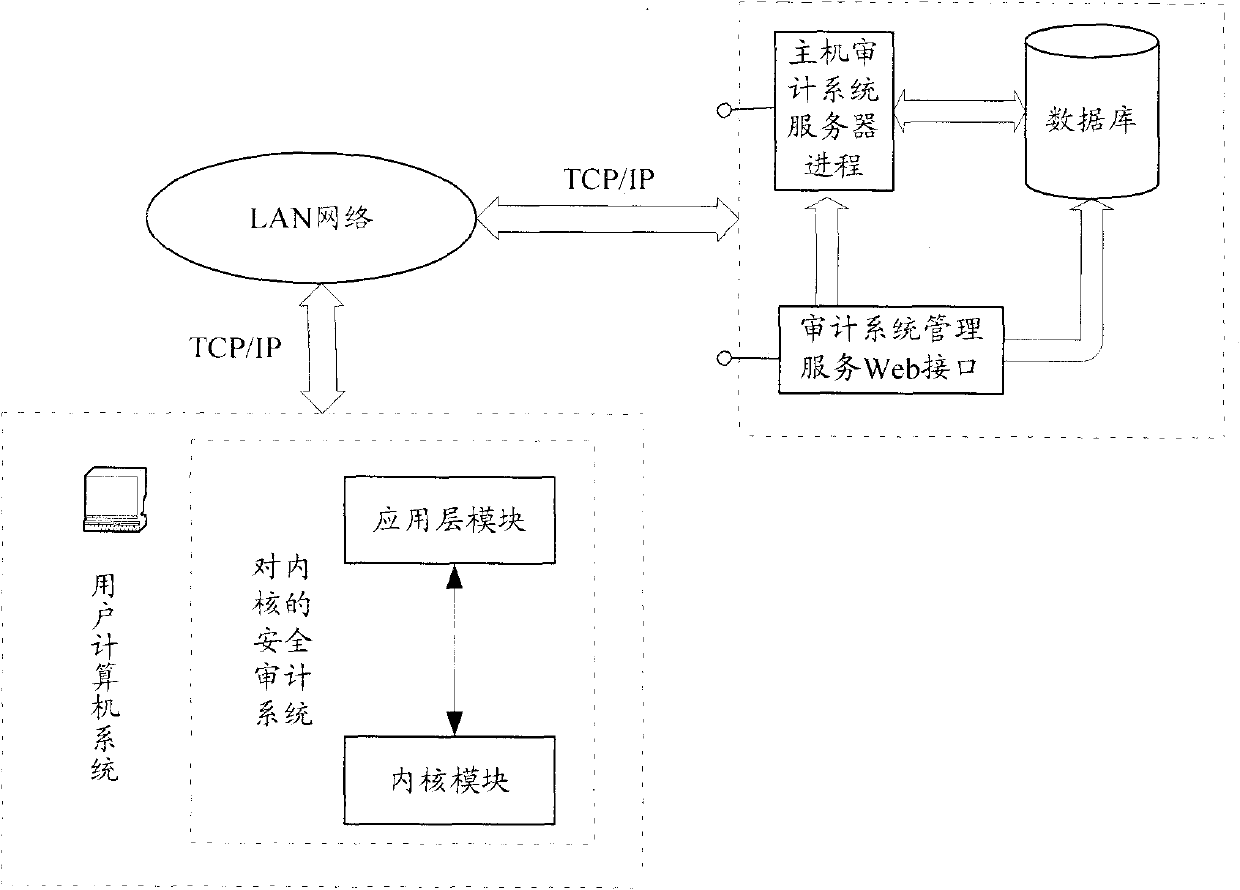
[0052] The kernel security audit system in thi...
Embodiment 3
[0058] The schemes of Embodiment 1 and Embodiment 2 of the present invention will be described in detail below through a specific example.
[0059] Assume that two behavior information groups are preset in the third embodiment, wherein: the kernel hook identifier contained in behavior information group 1 is IDT keyboard hook identifier+TDI network communication hook identifier; the kernel hook identifier contained in behavior information group 2 IDT keyboard hook identifier + NDIS network communication hook identifier.
[0060] Kernel scanning module 11 scans each kernel module of computer, obtains the behavior of installing hooks in 3 kernel modules respectively, and sends the identification of these 3 kernel modules to legal determination module 14; Legal determination module 14 according to preset Kernel whitelist information, determine that kernel module 3 is a legal kernel module; Legal determination module 14 sends the scan result of kernel module 1 and kernel module 2 t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com