Management system for integrated information security service and the protection method thereof
An information security and management system technology, which is applied in the management system and protection field of integrated information security services, can solve the problems of numerous and complicated information security event records, and it is difficult to prevent the decrease of bandwidth connected to external networks, so as to reduce manpower demand and reduce The effect of maintenance costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The embodiments of the present invention are described below through specific specific examples, and those skilled in the art can easily understand other advantages and effects of the present invention from the contents disclosed in this specification. The present invention may also be practiced or applied through other and different specific embodiments.
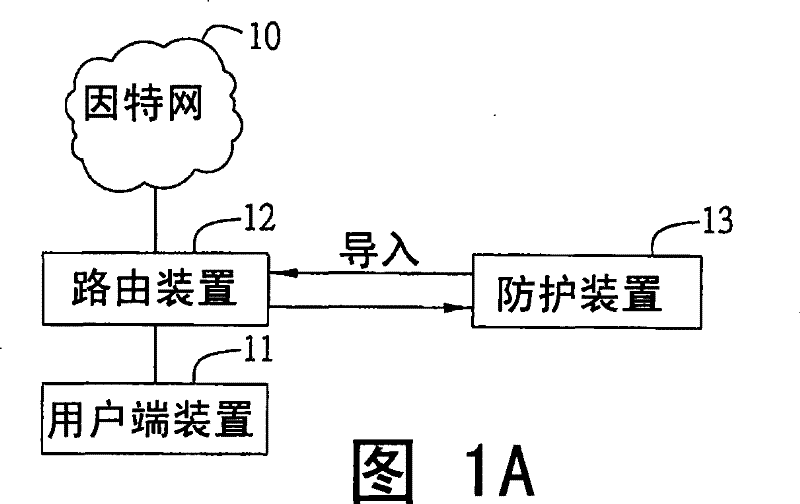
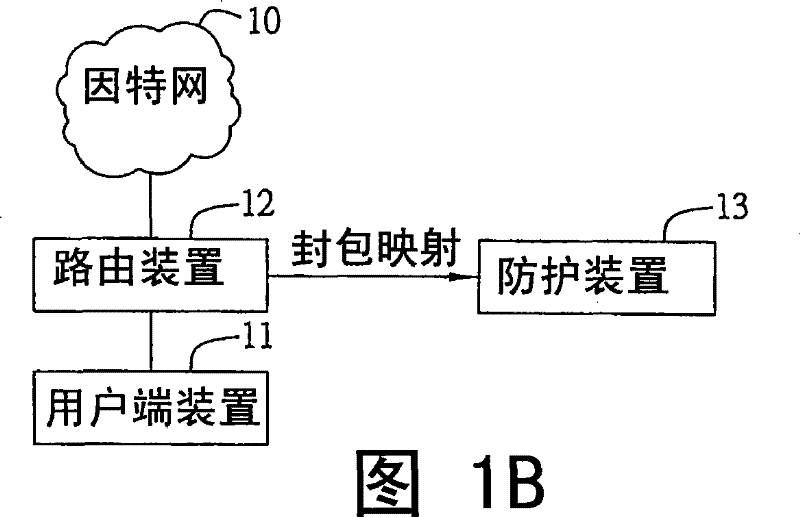
[0047] see Figures 1A to 1D , which is the architecture diagram of the management system integrating information security services of the present invention. like Figure 1A As shown, the system includes the Internet 10 , a client device 11 , a routing device 12 and a protection device 13 .
[0048] The client device 11 is an electronic device that can access data and perform data processing, such as a desktop computer, a notebook computer, a digital television device, a personal digital assistant and / or a mobile phone.
[0049] The routing device 12 is used for providing the connection routing path of the client d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com