Management method and system of vent key
A technology of air interface keys and management methods, applied in security devices, electrical components, wireless communications, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
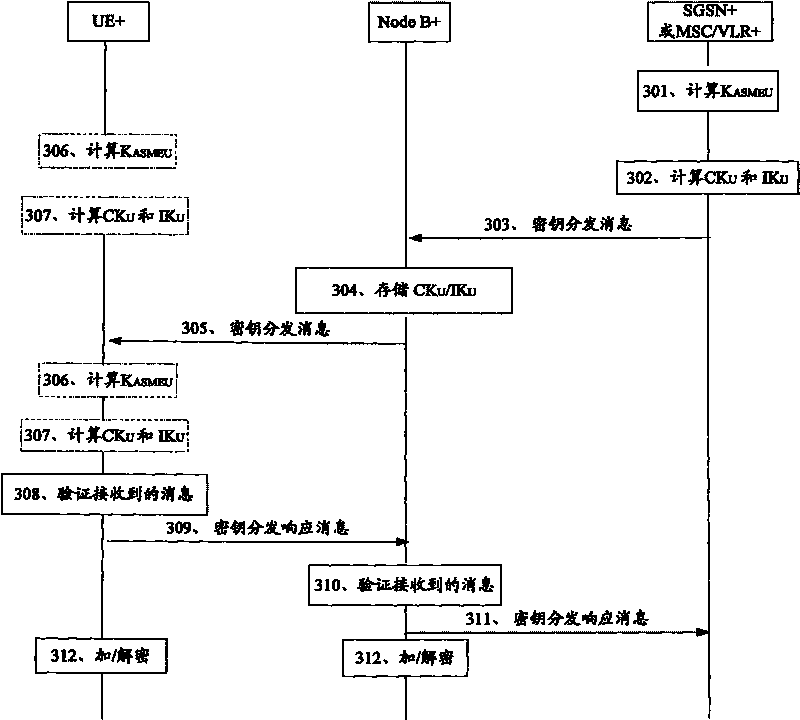
[0093] This embodiment describes an example in which the user equipment and the base station distribute the air interface key through the key distribution process. In this embodiment, after the SGSN+ or MSC / VLR+ generates the air interface key, it distributes the key to the Node B+. The specific process is as follows: image 3 Shown:
[0094] Step 301, SGSN+ or MSC / VLR+ calculates the intermediate key K according to the encryption key CK and integrity key IK received from the HSS ASMEU .
[0095] Optionally, this step also includes: SGSN+ or MSC / VLR+ decides the allowed encryption algorithm set and / or integrity algorithm set. The encryption algorithm set and / or the integrity algorithm set used by the SGSN+ or MSC / VLR+ may be a predetermined algorithm or a re-determined algorithm.
[0096] where the K ASMEU The generation parameters of can also include one or more of the following parameters:
[0097] Random number NONCE generated by SGSN+ or MSC / VLR+, service network ident...
Embodiment 2
[0125] This embodiment describes another example in which the user equipment and the base station distribute the air interface key through the key distribution process, such as Figure 4 shown. The difference between this embodiment and Embodiment 1 is that the encryption key CK of HSPA+ U and integrity key IK U Generated at Node B+. At this time, SGSN+ or MSC / VLR+ needs to set K ASMEU Sent to Node B+ in a key distribution message. If K ASMEU The generation parameters of the parameter include the random number NONCE, and the NONCE is generated by SGSN+ or MSC / VLR+, and needs to be delivered to Node B+ along with the key distribution message. If CK U / IK U The generation parameters of the parameter include the random number NONCE, and the NONCE is generated by Node B+, and needs to be sent to the user equipment along with the key distribution message.
[0126] Step 401, SGSN+ or MSC / VLR+ calculates K according to the encryption key CK and integrity key IK received from ...
Embodiment 3
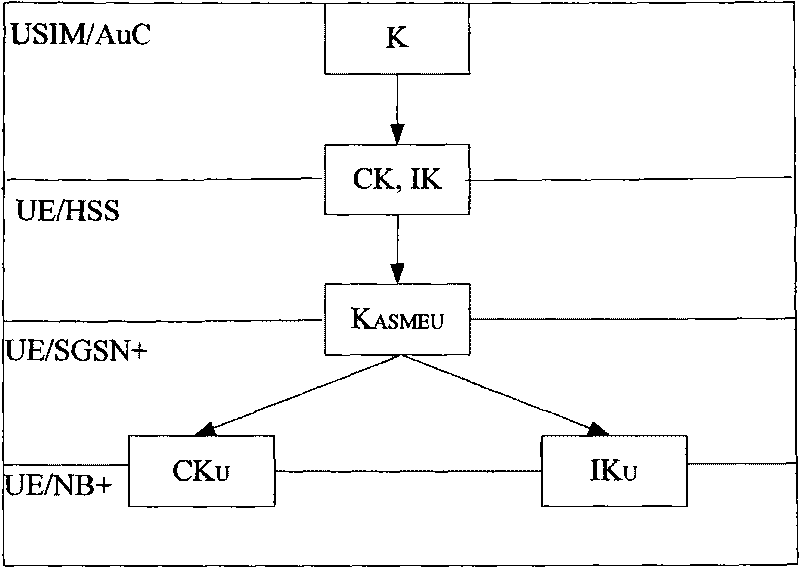
[0152] This example illustrates the calculation of K from IK and CK ASMEU An example of . K ASMEU In addition to IK and CK, the generation parameters include one of the following or any combination thereof: random number NONCE generated by SGSN+ or MSC / VLR+ or Node B+, service network identifier (SN ID), serial number SQN, hidden key AK , authentication management field AMF, user identity (such as IMSI, IMEI, TMSI), encryption algorithm identifier enc-int-ID, integrity algorithm identifier int-alg-ID, re-entry counter COUNTER.
[0153] K ASMEU = F1(CK, IK, NONCE);
[0154] or K ASMEU = F1(CK, IK, SN ID);
[0155] or K ASMEU =F1(CK, IK, SN ID, SQN, AK);
[0156] or K ASMEU =F1(CK, IK, SN ID, SQN);
[0157] or K ASMEU = F1(CK, IK, SN ID, AK);
[0158] or K ASMEU = F1(CK, IK, SQN, AK);
[0159] or K ASMEU = F1(CK, IK, SQN, AK);
[0160] or K ASMEU = F1(CK, IK, COUNTER).
[0161] where the K ASMEU The generated parameter COUNTER is the number of re-entry times, w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com