Authentication method and apparatus
An authentication method and user authentication technology, applied in the field of authentication technology, can solve problems such as failure to notify servers or administrators
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] Hereinafter, embodiments according to the present invention will be described in detail with reference to the accompanying drawings.
[0029] System configuration common to each embodiment
[0030] figure 1 is a system configuration common to the first to sixth embodiments.
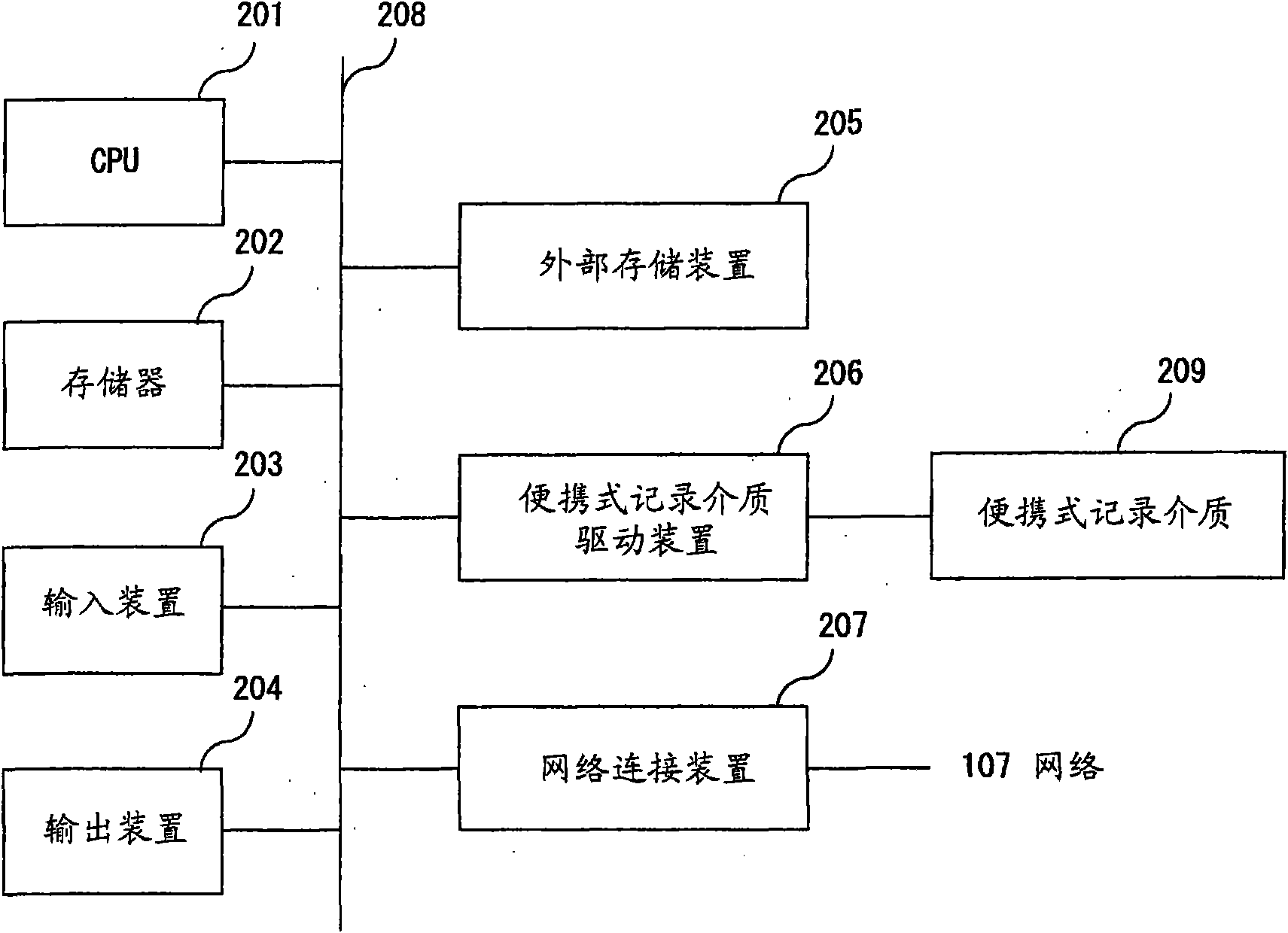
[0031] The client 101 is, for example, a personal computer system used by a user.
[0032] The biometric information input unit 102 inputs fingerprint information by causing the user to place his or her finger for fingerprint authentication.
[0033] The output unit 103 displays an authentication screen to the user, and displays various types of applications after startup.
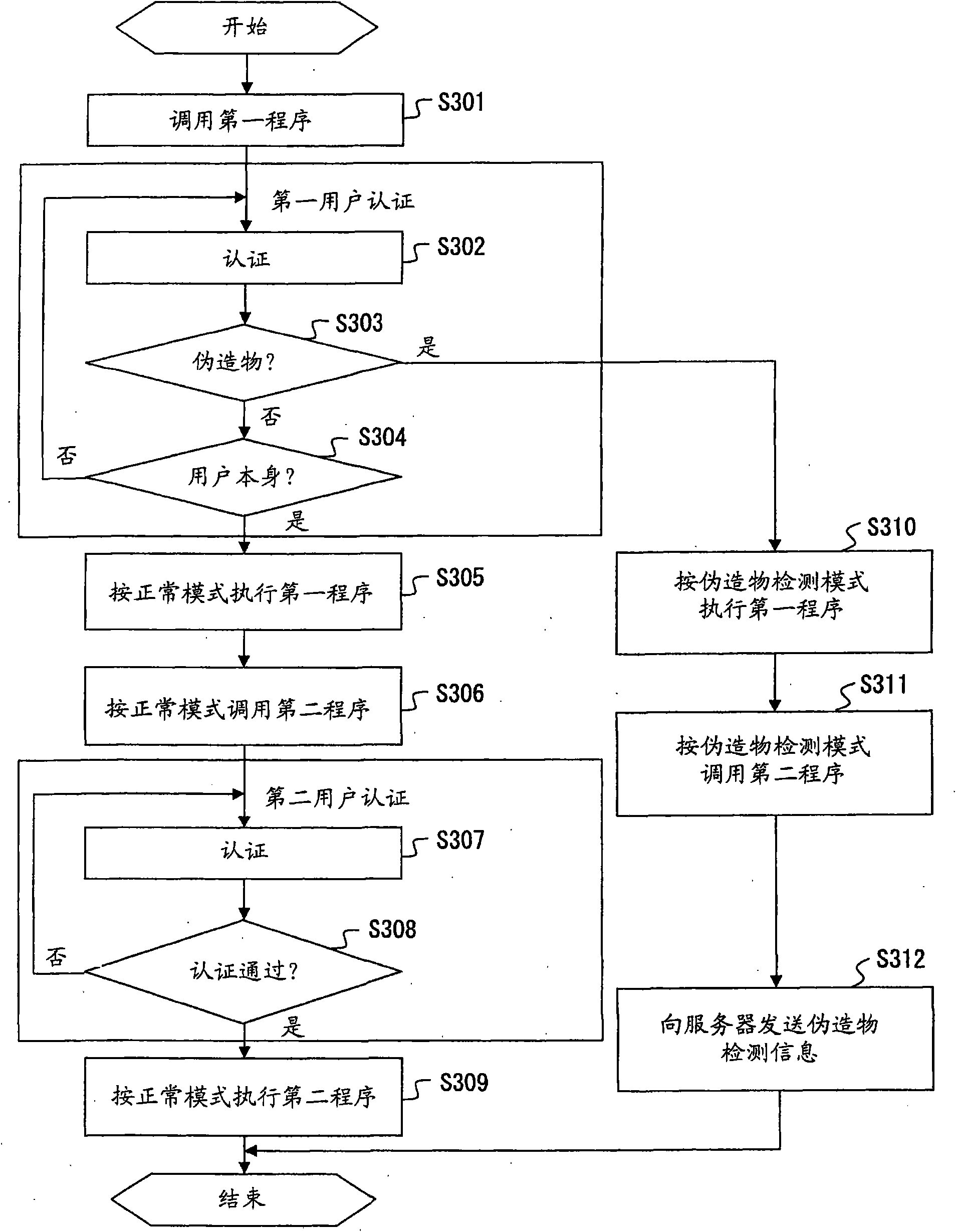
[0034] The control unit 104 controls authentication processing of biometric information, and calls the first program 105 and the second program 106 as necessary. The first program 105 is, for example, BIOS (Basic Input Output System), and the second program 106 is, for example, an operating system.
[0035] The server 108 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com