Card locking method, subscriber identity module card and mobile terminal
A technology of customer identification module and mobile terminal, which is applied in the field of communication, can solve problems such as no reusability, no solution proposed, lack of implementation method for many-to-many locking of mobile terminals and SIM cards, etc., and achieve the effect of locking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
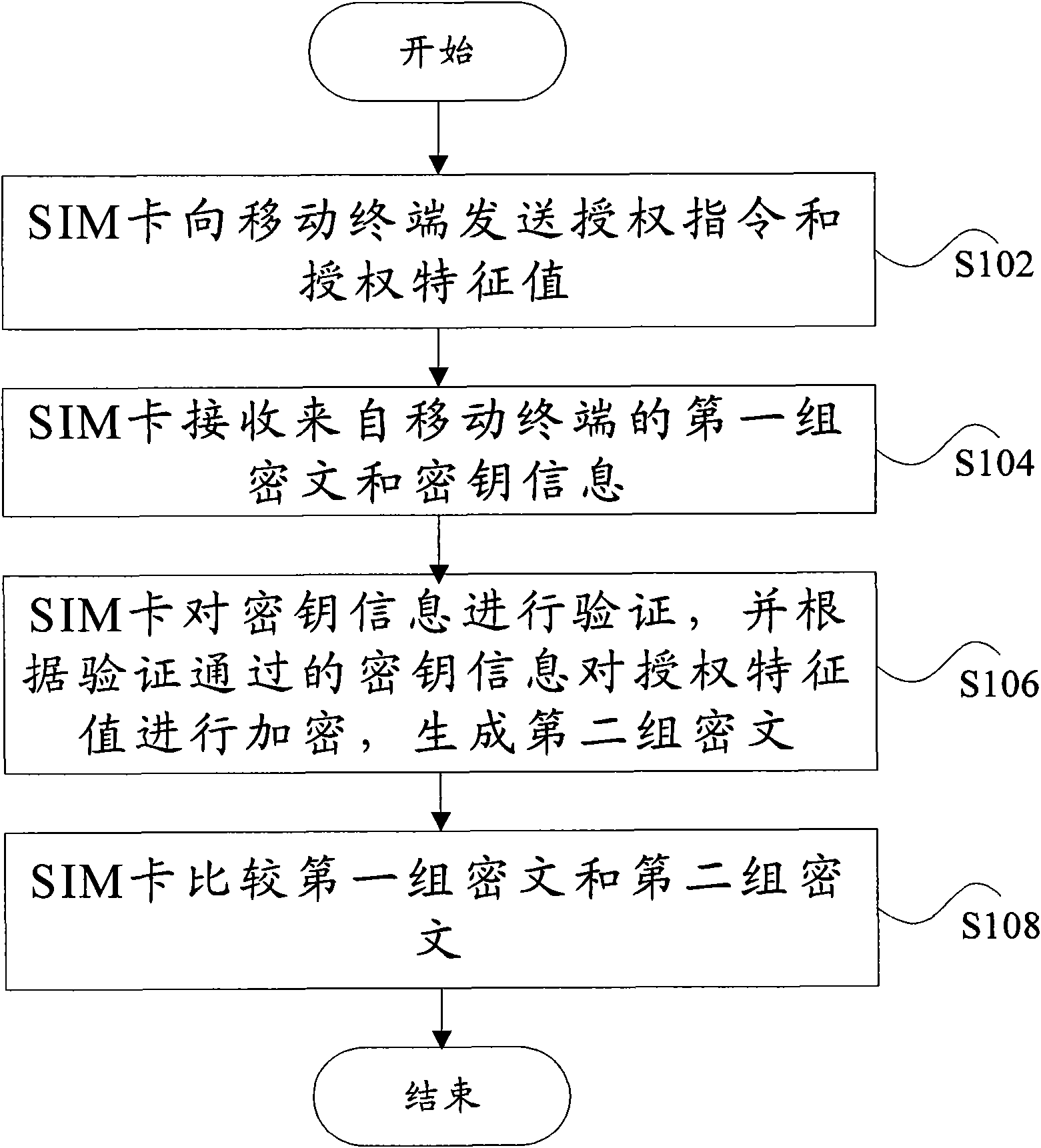
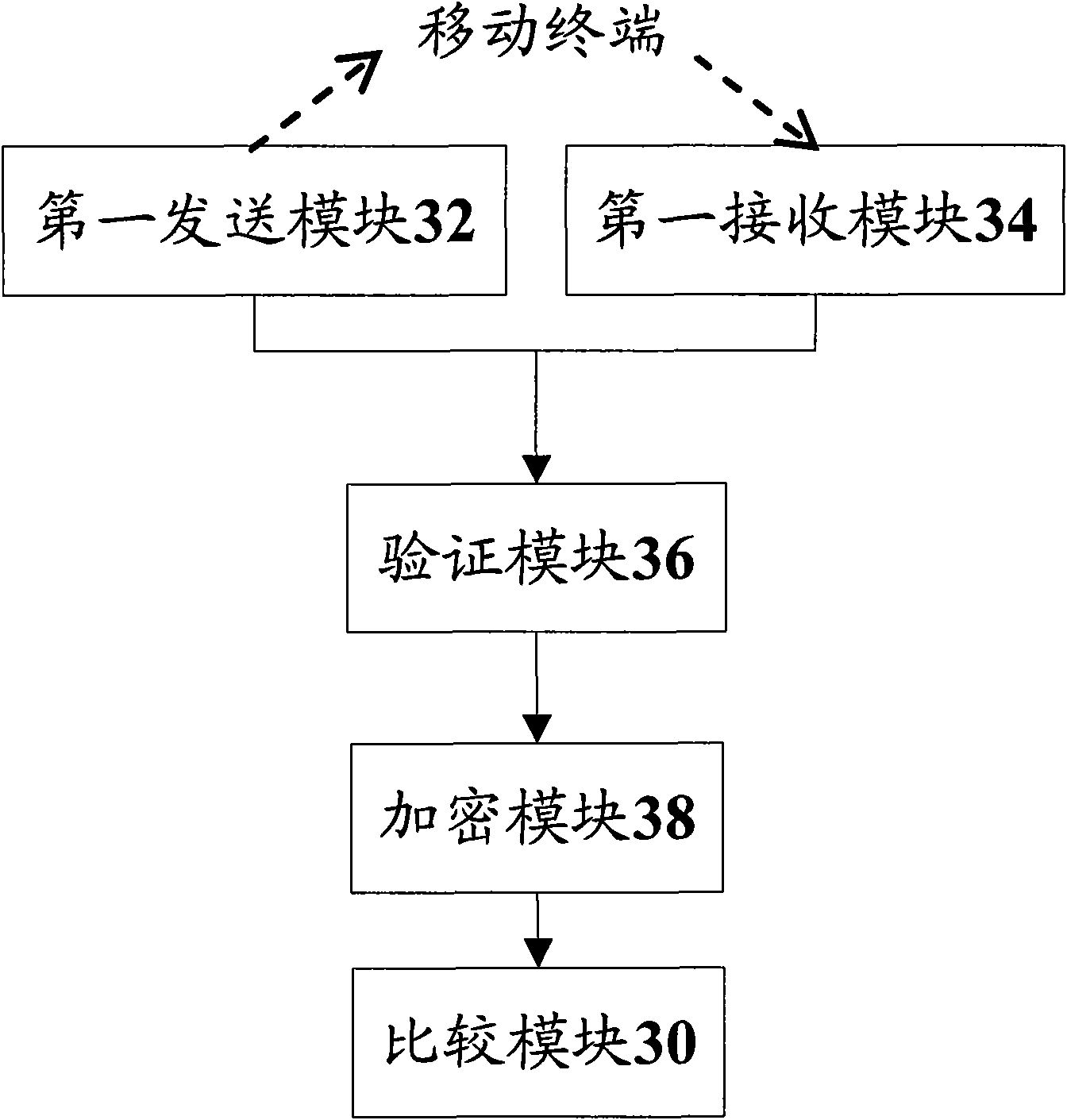
[0058] According to an embodiment of the present invention, a SIM card is provided, image 3 is a schematic diagram of the structure of a SIM card according to an embodiment of the present invention, such as image 3 As shown, the SIM card includes: a first sending module 32 , a first receiving module 34 , a verification module 36 , an encryption module 38 , and a comparison module 30 . This structure will be described in detail below.
[0059] The first sending module 32 is used to send the authorization instruction and the authorization feature value to the mobile terminal, wherein the authorization feature value is a group of data used to lock the mobile terminal and the SIM card; the first receiving module 34 is used to receive data from The first set of ciphertext and key information for the mobile terminal, wherein the first set of ciphertext is the ciphertext obtained by the mobile terminal encrypting the authorization feature value according to the key information; th...
Embodiment 2
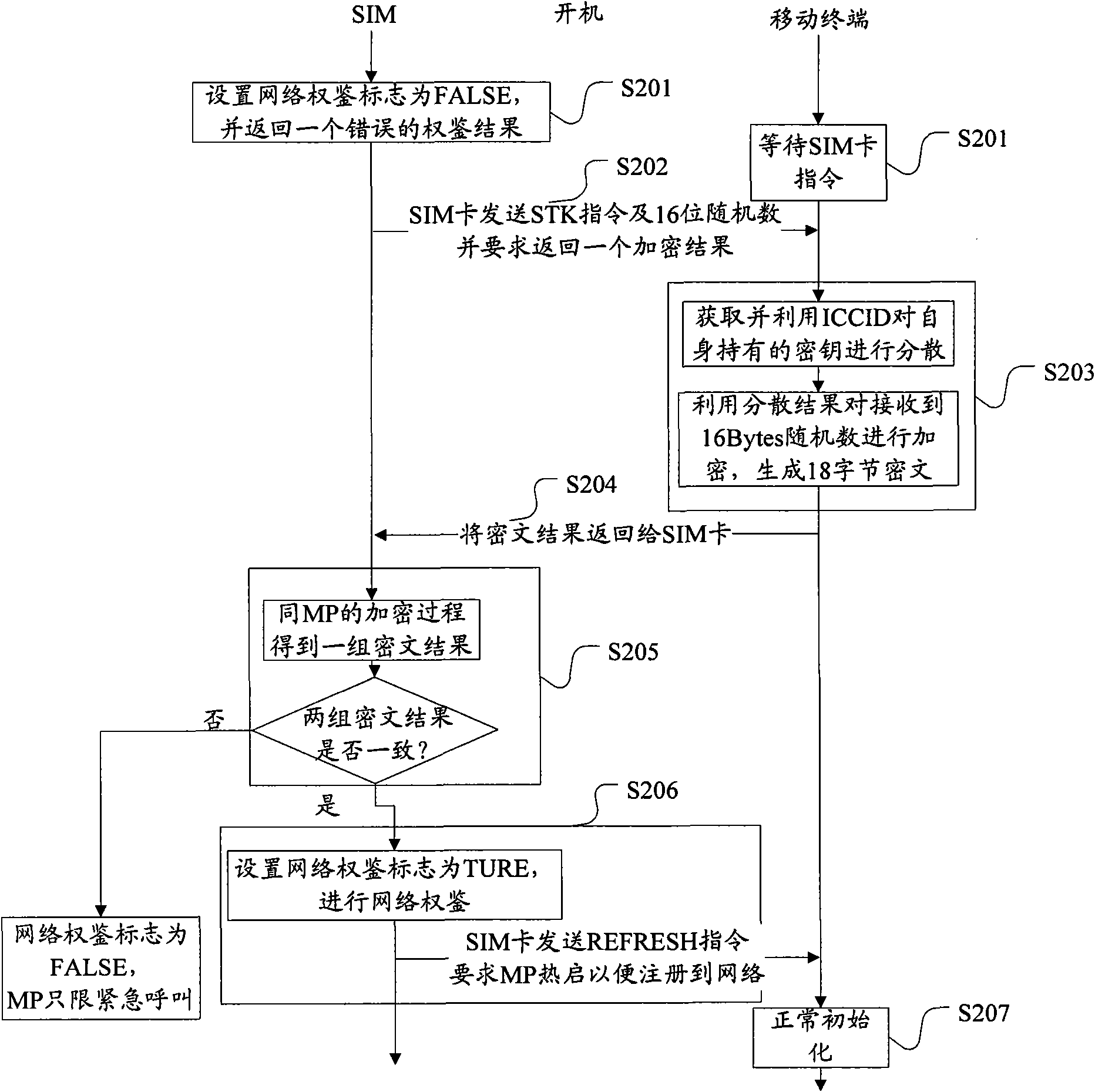
[0068] According to an embodiment of the present invention, a mobile terminal is provided, Figure 5 is a schematic diagram of the structure of a mobile terminal according to an embodiment of the present invention, such as Figure 5 As shown, the mobile terminal includes a second receiving module 52, an encryption module 54, and a second sending module 56, and the structure will be described in detail below.
[0069] The second receiving module 52 is used to receive authorization instructions and authorization feature values from the SIM card, wherein the authorization feature value is a group of data used to lock the mobile terminal and the SIM card; the encryption module 54 is connected to the second receiving module. Module 52 is used to encrypt the authorization feature value using a key according to the authorization instruction received by the second receiving module 52 to obtain the first group of ciphertexts; the second sending module 56 is connected to the encryptio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com