Data encapsulation method and equipment thereof
A technology of data encapsulation and equipment, applied in the field of communication, can solve the problems of increasing equipment load, increasing the network bandwidth of IPsec tunnel transmission path, and limiting the scope of IPsec encapsulation, so as to reduce the encapsulation process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
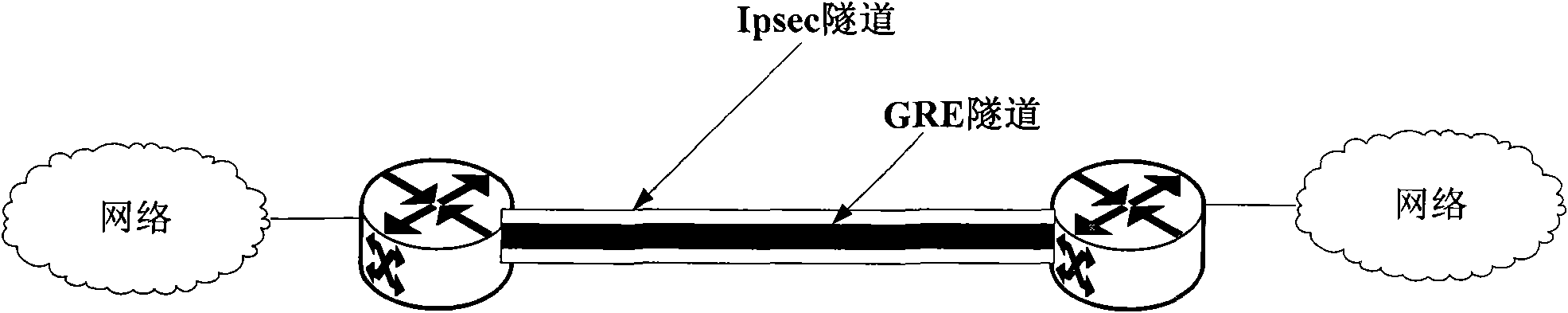
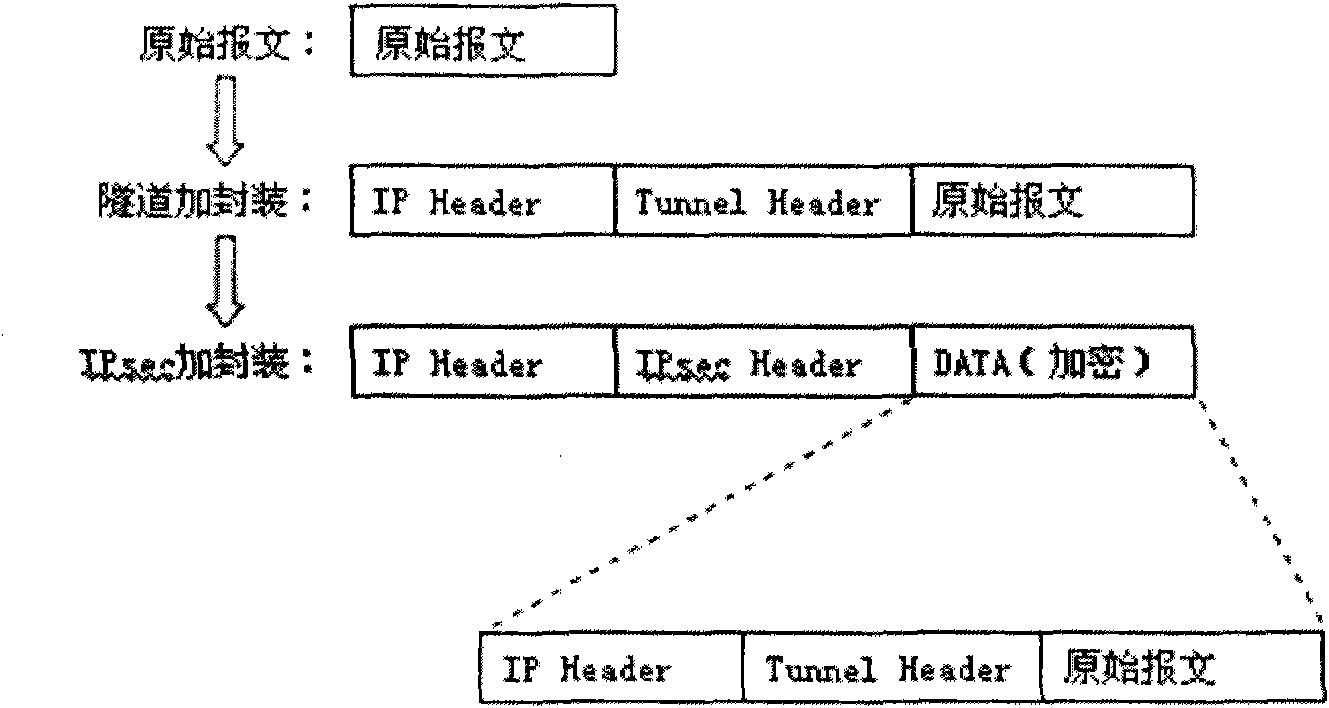
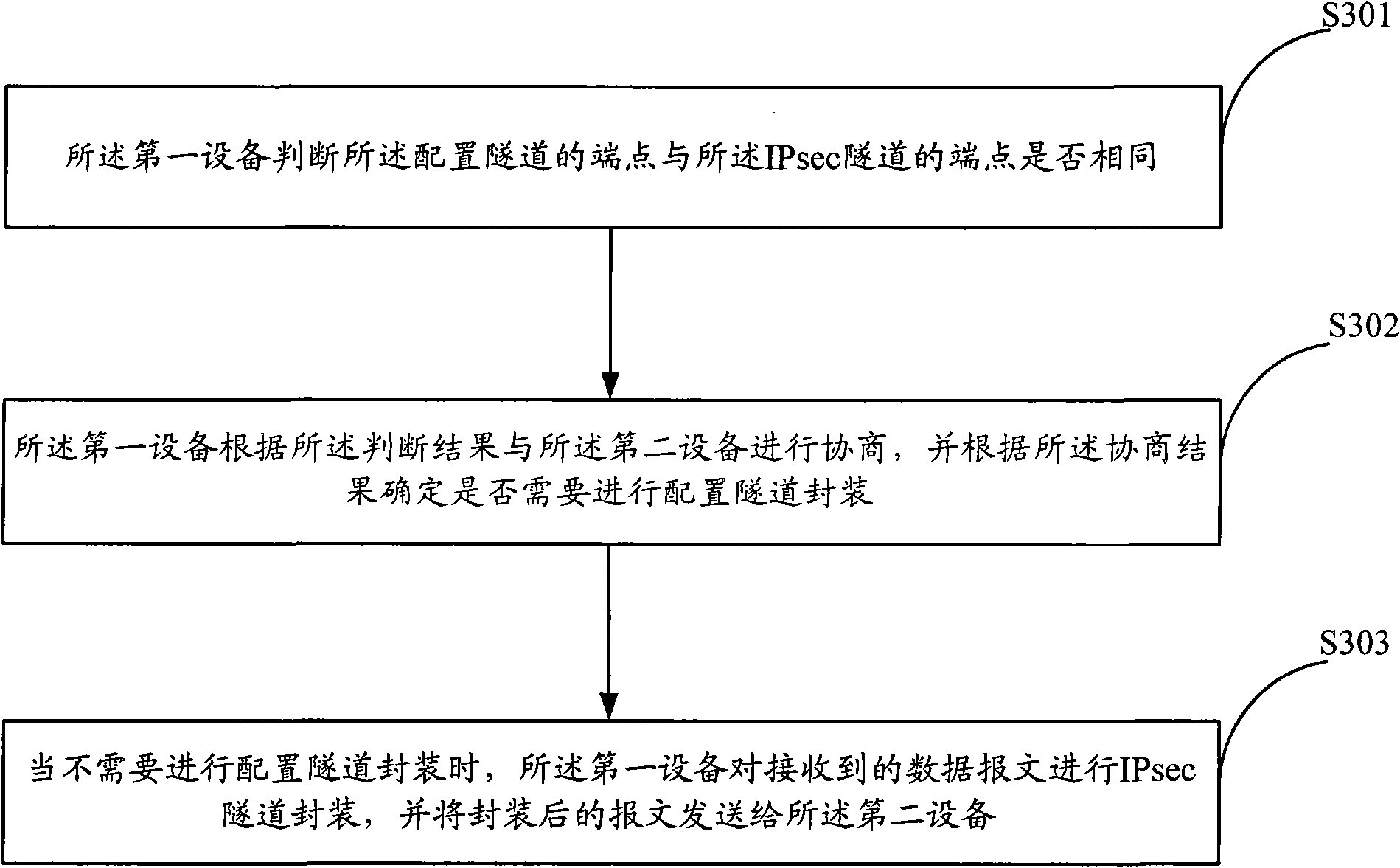
[0054] The core idea of the present invention is under the situation that configuration tunnel (for example, GRE tunnel) and IPsec tunnel exist between IPsec peers using IPsec protocol, by judging whether configuration tunnel end point and IPsec tunnel end point are identical, and according to the judgment result Negotiate between IPsec peers. When the judgment result of the IPsec peers is that the configured tunnel endpoint is the same as the IPsec tunnel endpoint, only the IPsec tunnel encapsulation process is performed on the data packet, and the configuration tunnel encapsulation process is not required. process, thereby omitting the encapsulation process of configuring the tunnel, reducing the load on the device, and improving the efficiency of IPsec encryption. After the encapsulated packet reaches the peer end of the IPsec tunnel, IPsec decapsulates it and directly processes the original packet, omitting the process of configuring tunnel decapsulation and also reducing...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com