Method for realizing secure communication of any two ends of the internet in DMVPN
A technology for secure communication at any two ends, applied in the direction of network interconnection, data exchange network, data exchange through path configuration, etc., can solve problems such as high rental fees, complex network configuration maintenance, etc., to simplify maintenance and improve throughput The effect of traffic flow and load reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the present invention will be further elaborated below in conjunction with specific illustrations and examples.
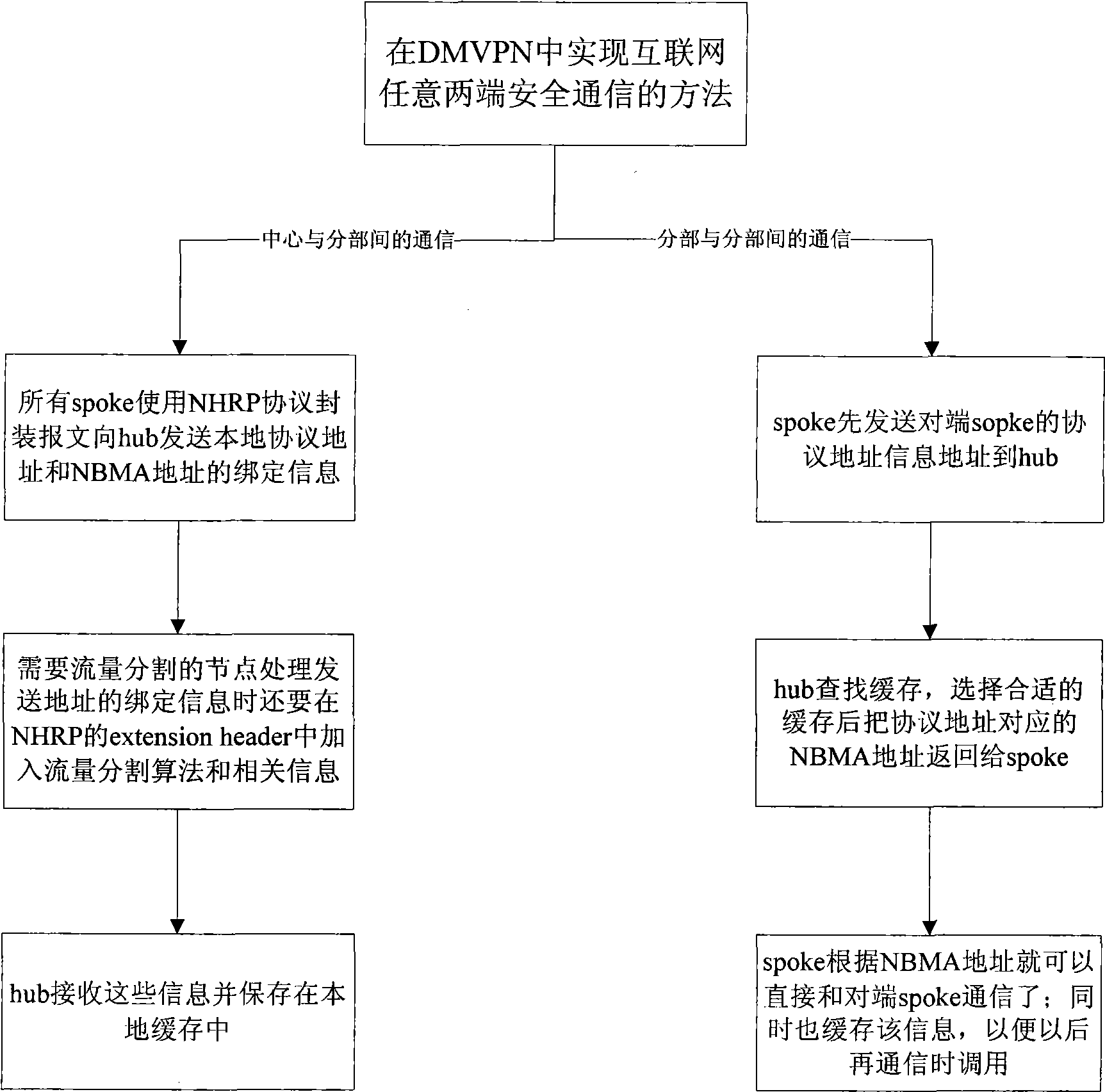
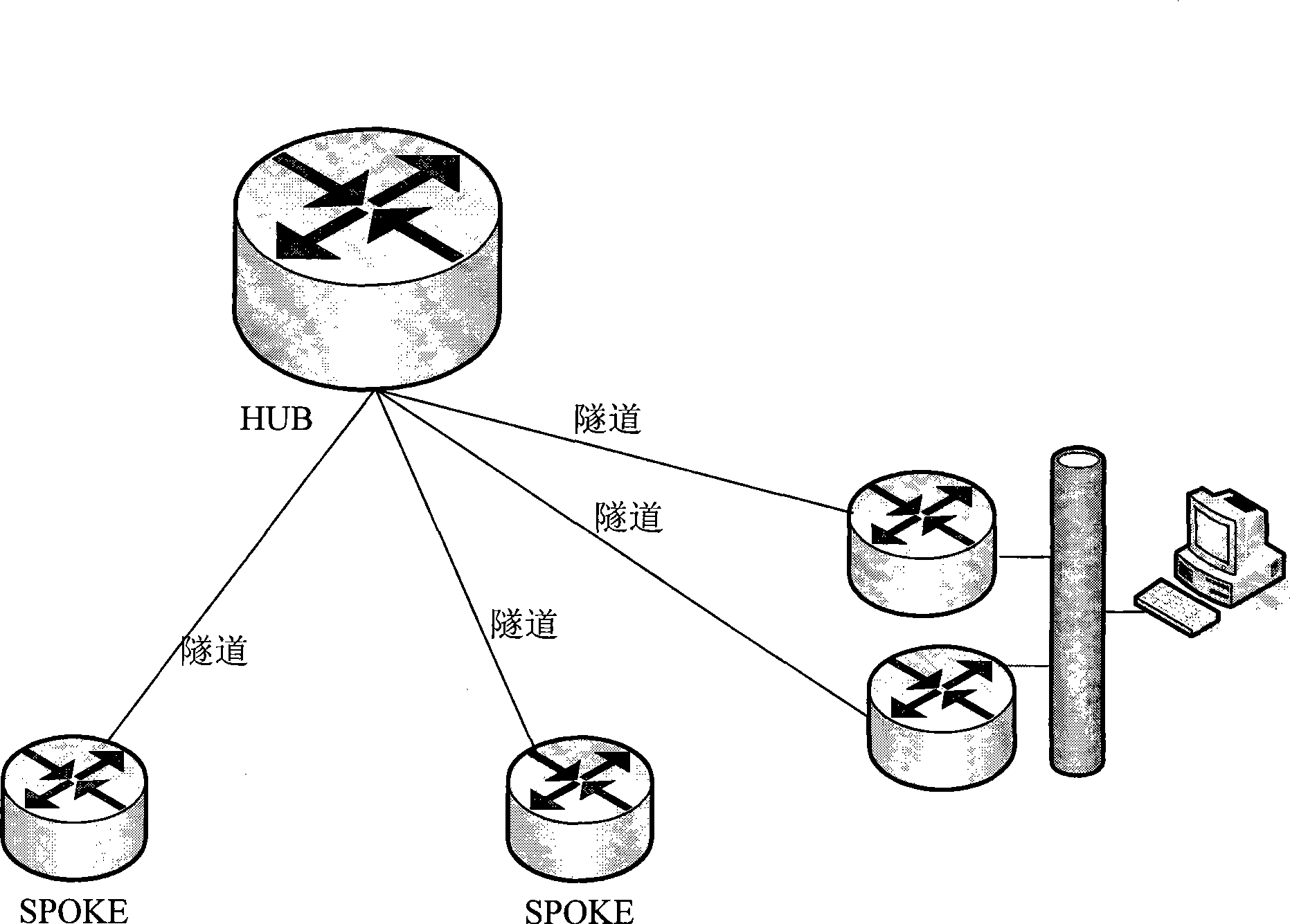
[0036] Such as figure 2 As shown, this figure is one of the network topology structures described in the method of the present invention. The usual procedure in a practical setup is as follows:
[0037] A. Establish a suitable network topology. If there are spokes with relatively heavy loads, devices can be added to reduce the burden on the spokes.
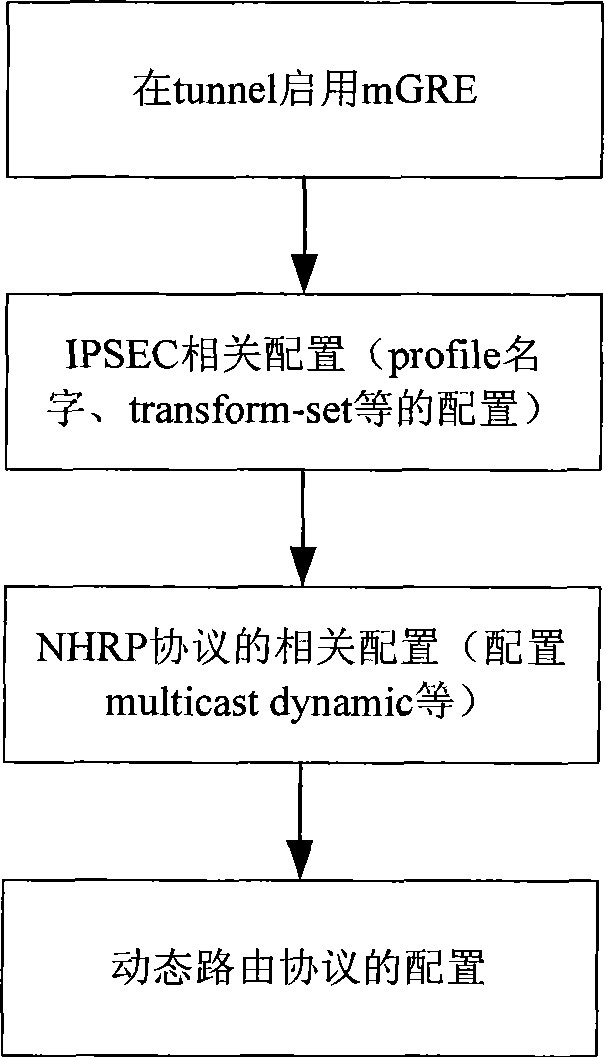
[0038] B. Configure the hub node (see image 3 ). Configure a tunnel interface and use the mGRE mode on the interface. IPSEC-related configuration (profile name, transform-set used, etc.), and apply the profile name to the tunnel port for encryption protection of the tunnel. NHRP related configuration (configure multicast dynamic, mainly used to send multicast messages to all re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com