Evaluation method for WEB application
An application system and user technology, applied in the field of information security, can solve problems such as inapplicable IT application system evaluation, and achieve the effect of flexible penetration testing, low false positive and false negative rates, and accurate scanning results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be described in detail below with reference to the accompanying drawings and in combination with embodiments.
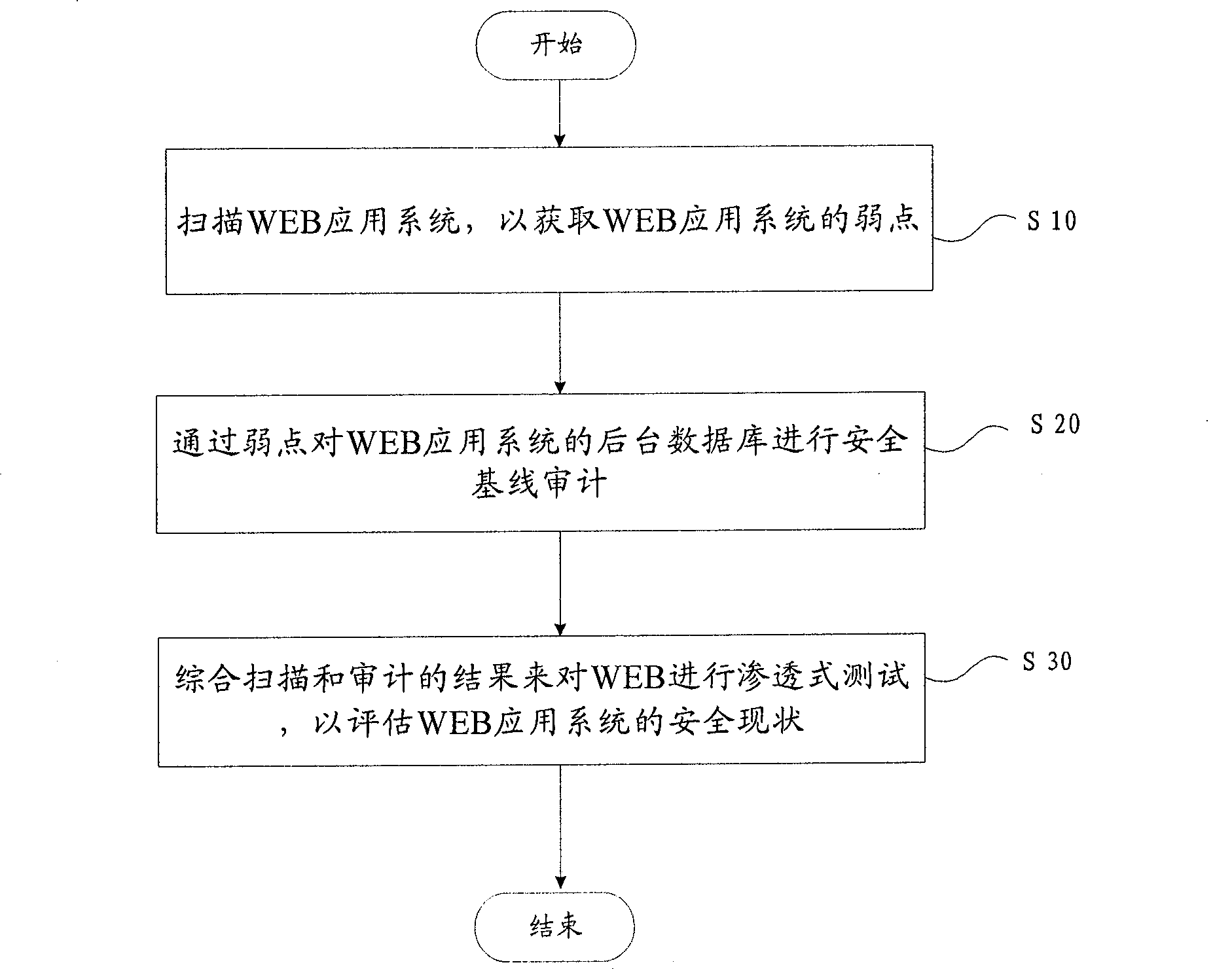
[0043] figure 2 A flow chart showing a method for evaluating a WEB application according to an embodiment of the present invention includes the following steps:
[0044] Step S10, scanning the WEB application system to obtain the weaknesses of the WEB application system;
[0045] Step S20, through the backstage of the WEB application system through the weakness;
[0046] Step S30, comprehensively scan and audit the results to infiltrate the WEB application system
[0047] Penetration testing to assess the security status of WEB application systems.
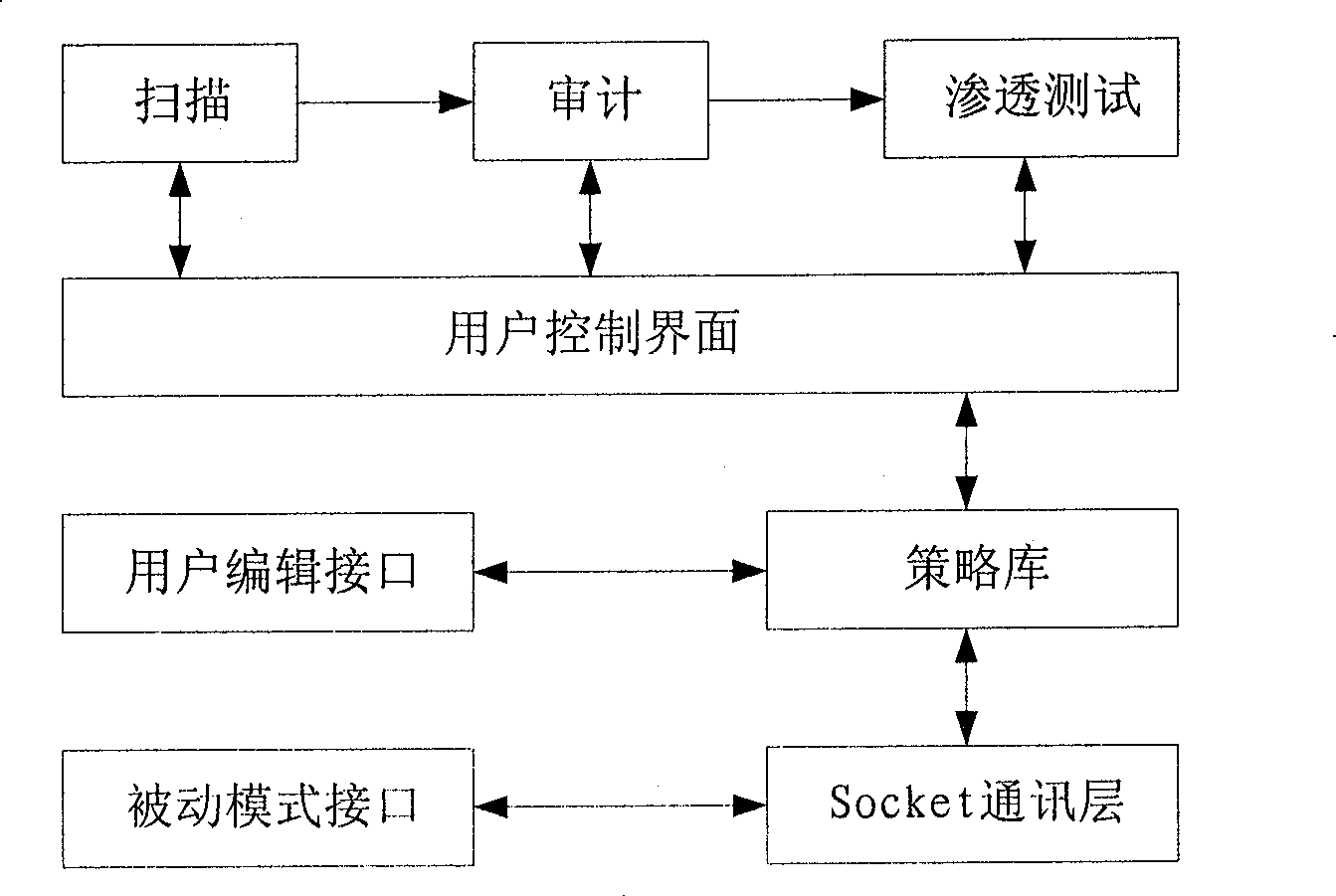
[0048] The WEB application evaluation method obtains evidence by first scanning the WEB application system and analyzing weaknesses, and then performs database security baseline audit and penetration testing on the obtained evidence to obtain a security performance evaluation. In th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com