Method and apparatus for intercepting junk mail
一种垃圾邮件、邮件的技术,应用在网络通信领域,能够解决效率低下、影响用户使用效果等问题,达到提高扫描速度和效率的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
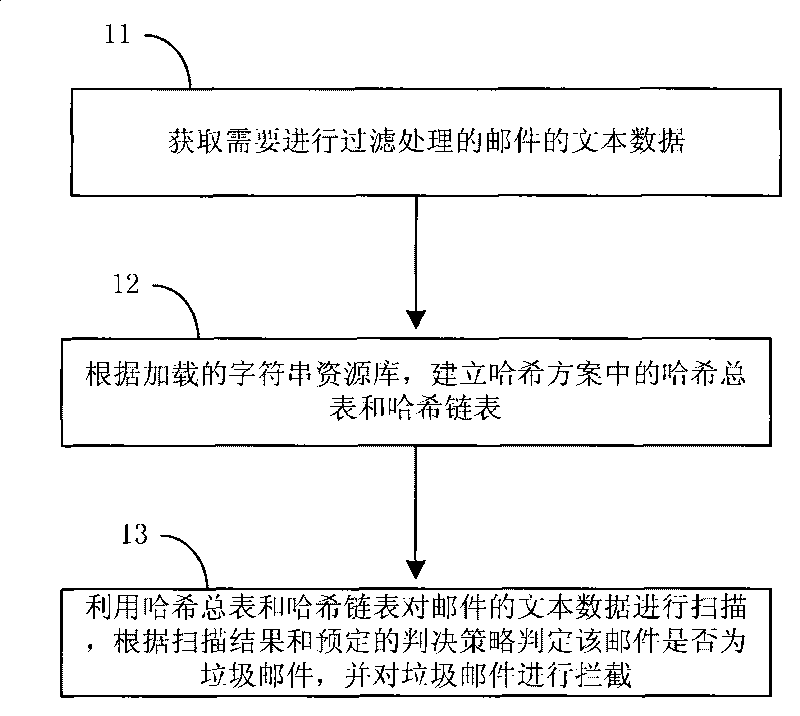
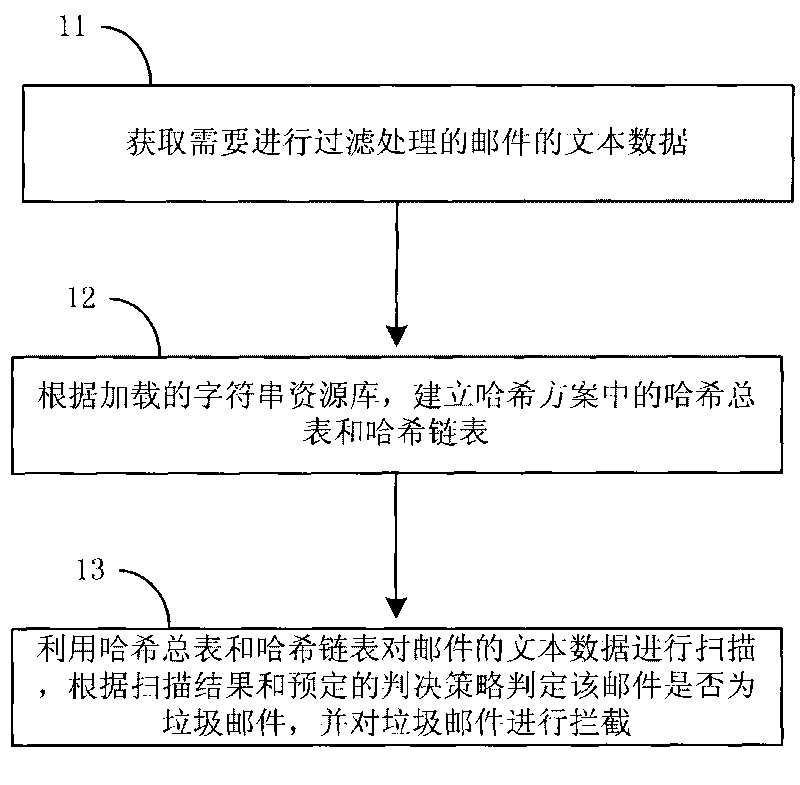
[0039] The processing flow of the method for intercepting spam provided by this embodiment is as follows: figure 1 As shown, the following processing steps are included:
[0040] Step 11, acquiring the text data of the emails that need to be filtered.
[0041] After receiving an email that needs to be filtered, the email is decoded to obtain the title and text content of the email, and after the title and the text are directly spliced, a text data to be filtered is obtained, and the text data is saved.
[0042] Step 12, according to the loaded character string resource library, establish the total hash table and the hash linked list in the hash scheme.
[0043] After obtaining the text data of the above email, the string resource library needs to be loaded. The strings in the string resource library are composed of one or more character units, which can be: an English word, a Chinese character, a single English letter, half a Chinese character, or a full-width and half-width p...
Embodiment 2
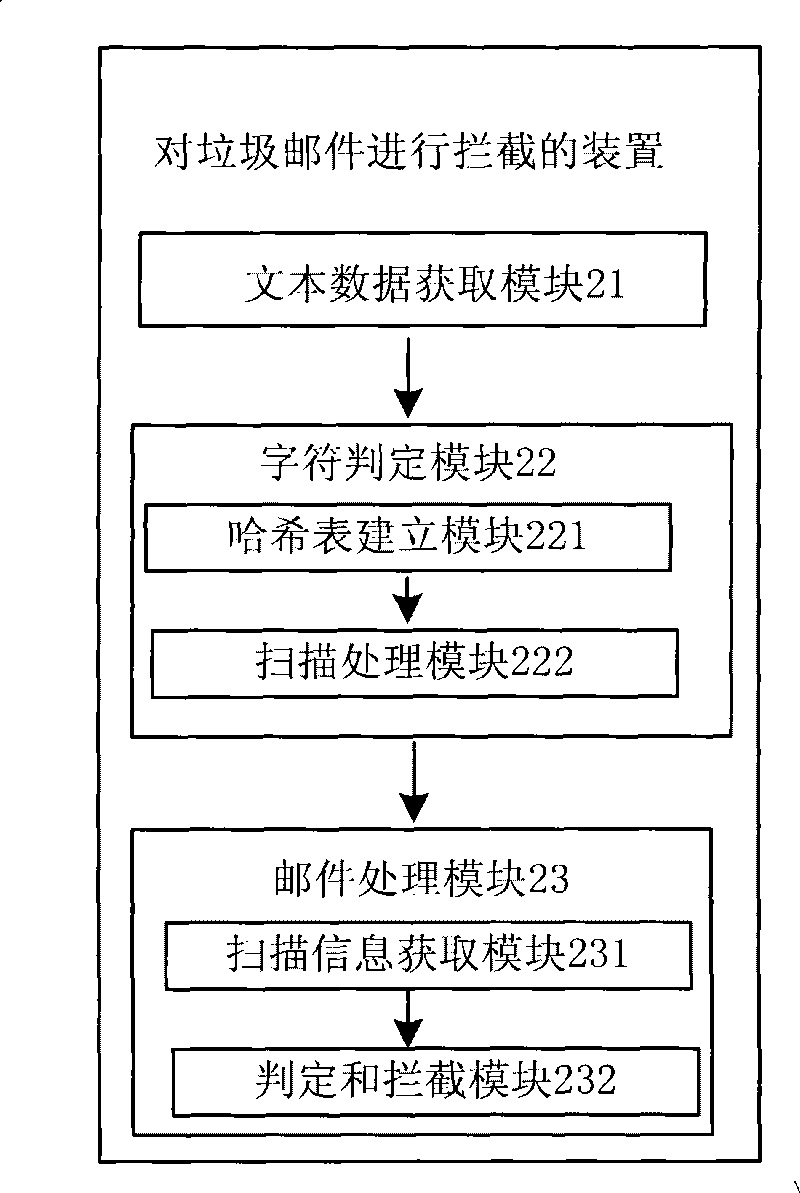
[0060] The embodiment of the present invention also provides a device for intercepting spam, and its specific implementation structure is as follows: figure 2 As shown, it may specifically include:
[0061] Text data obtaining module 21, is used for obtaining the text data of the mail that needs to be filtered;
[0062] Character judging module 22, is used for judging whether described text data contains the keyword in the character string in the character string resource storehouse that is used for mail filtering, when described text data contains described keyword, then judges described Whether the text data contains the character string in the character string resource library corresponding to the keyword;
[0063] The email processing module 23 is configured to determine whether the email is spam according to the determination result of whether the text data contains the character string in the character string resource library corresponding to the keyword, and a predete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com