Method and system for implementing safety access public network of network terminal as well as special network access controller thereof
A network terminal and network access technology, applied in the field of computer network security, can solve the problems of malicious intrusion of firewall equipment, unaffordable costs, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
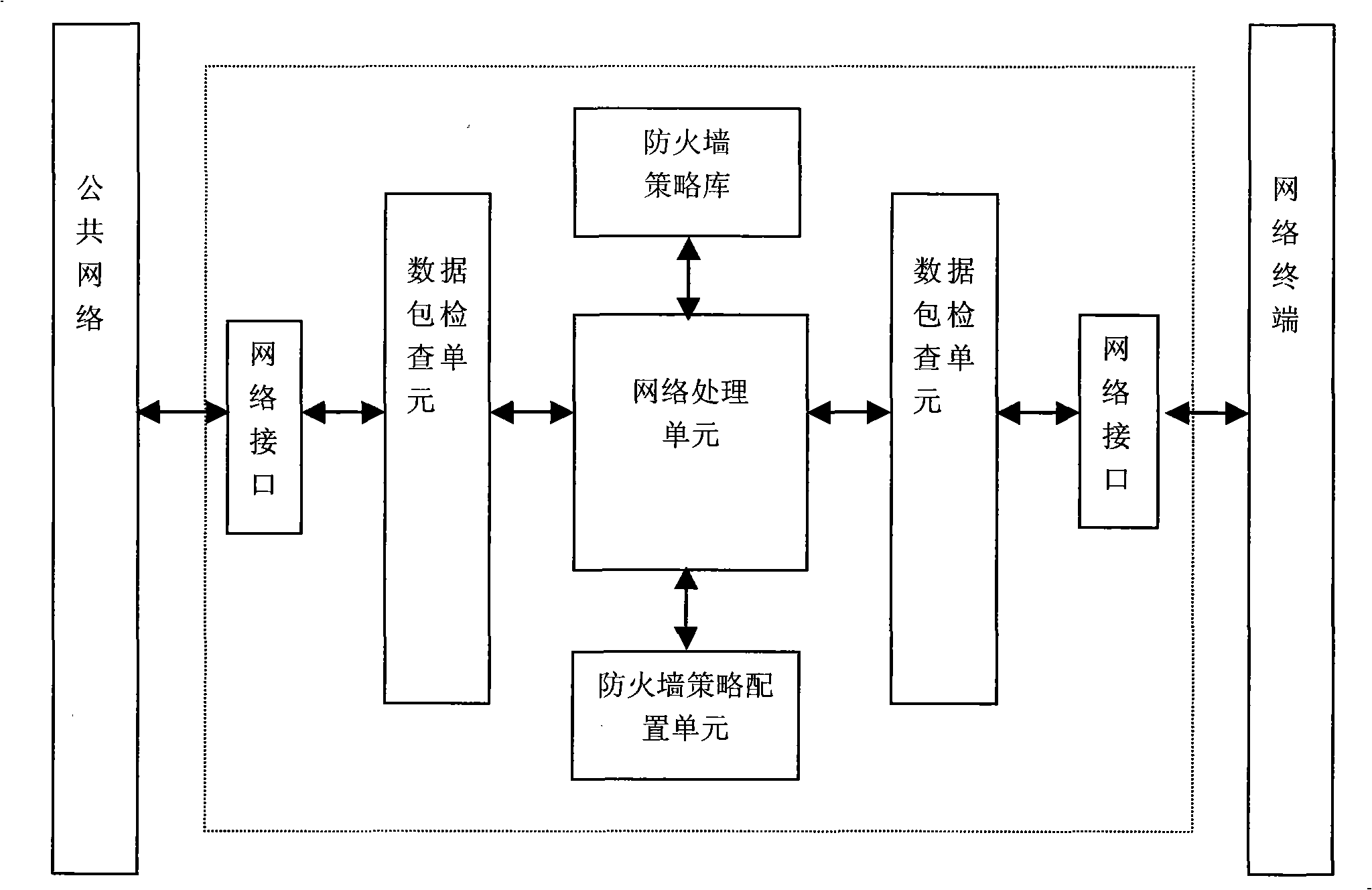
[0026] In a specific embodiment of the present invention, a network terminal access controller (NTAC) is connected in series between the network terminal (NT) and the Internet, and connected in series on the link between the Internet and the NT, to control the flow through the NTAC Packets are inspected and controlled. NTAC is a device transparent to NT and the Internet in the network topology, and does not need to assign IP addresses to it.
[0027] The involved NTACs have the following characteristics:
[0028] NTAC cannot be assigned an IP address, it is not assigned an IP address, and it is transparently set in the overall network topology;
[0029] NTAC has a unique device identification code ID;
[0030] NTAC can store firewall policies for detecting and controlling IP data packets;
[0031] NTAC initialization is set to "Stop NTAC Firewall".
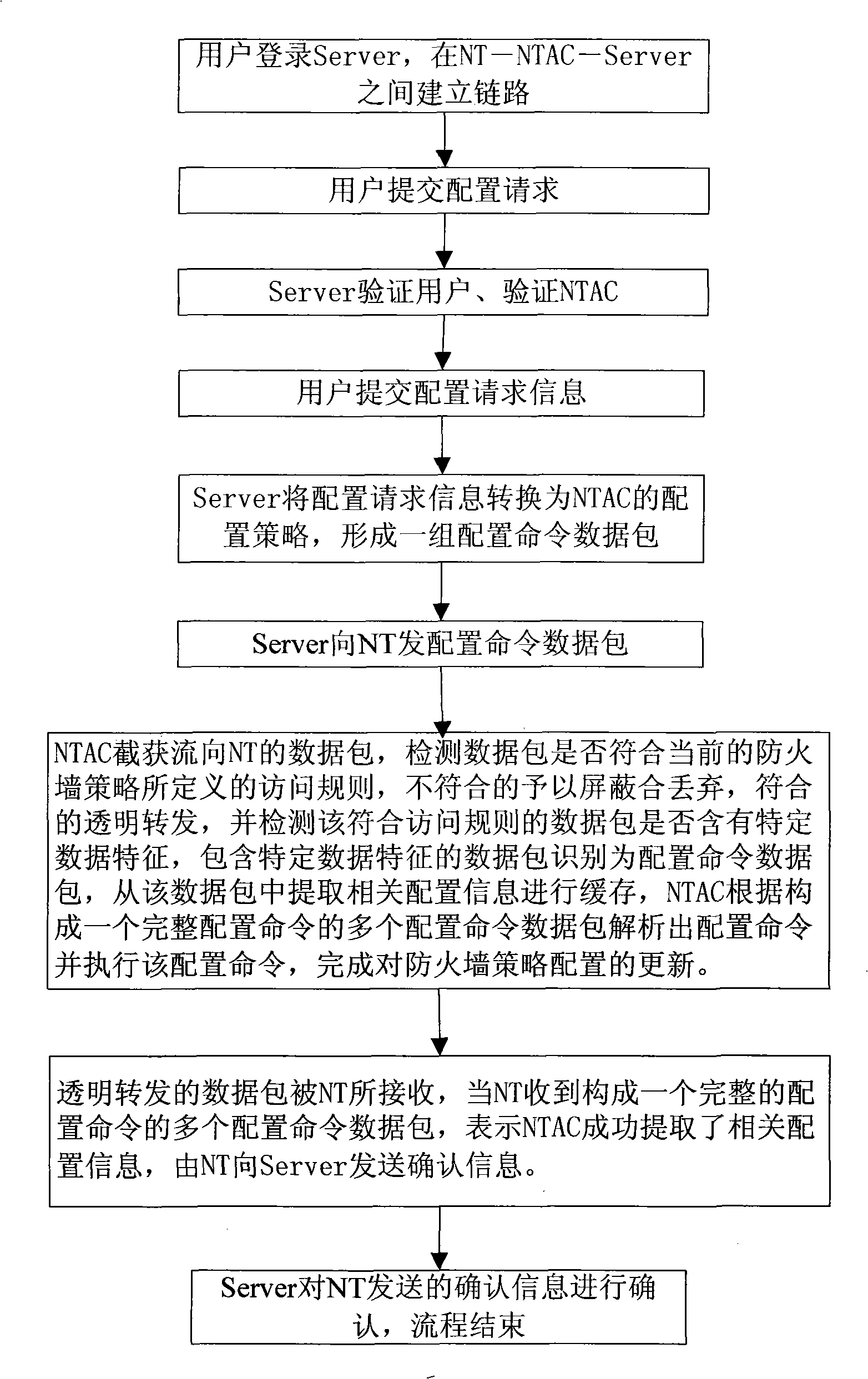
[0032] A feature of the firewall policy is to shield all data packets flowing to NT by default, and only when it detects tha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com