Reference monitor implementing method of high safety grade operating system
A security level and operating system technology, applied in the field of non-bypassable reference monitor implementation, can solve the problems that the reference verification mechanism cannot be bypassed, etc., to improve security and service capabilities, ensure effectiveness, and meet security requirements required effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
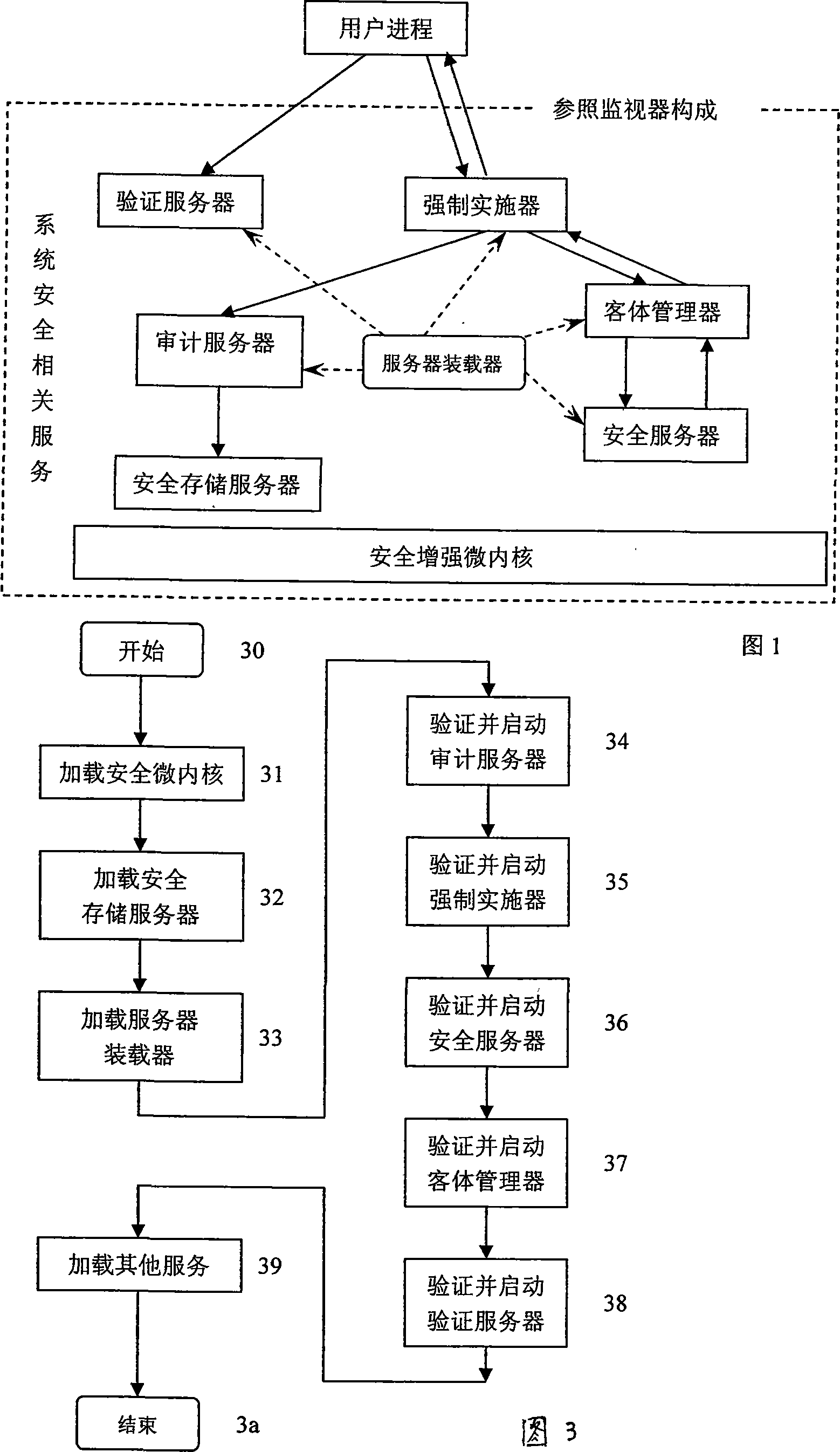
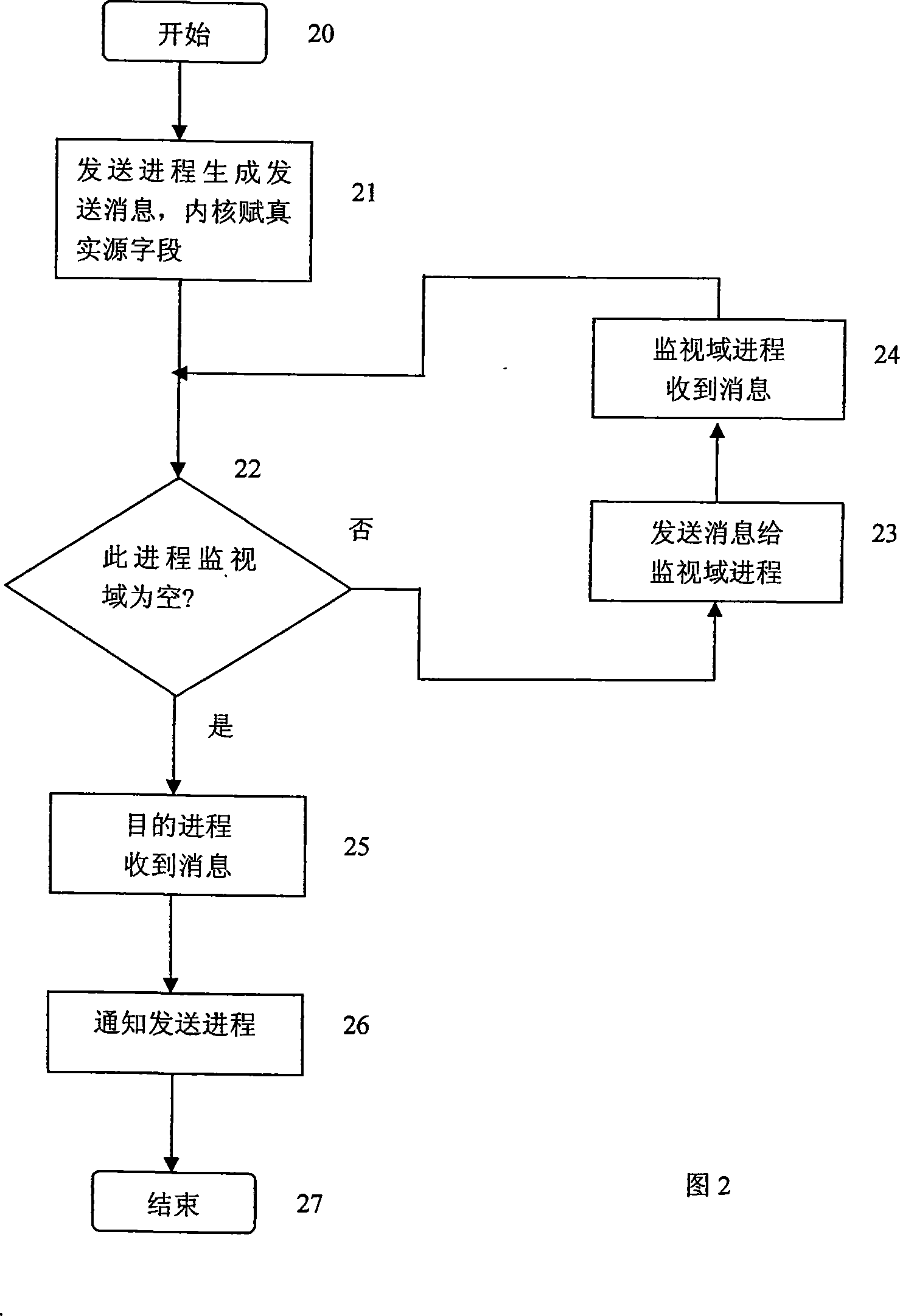
[0013] As shown in Figure 1, in the reference monitor structure of the present invention, each security service is interrelated to realize arbitration and monitoring that cannot bypass access control. The design purpose and function of each service are described as follows. The user process makes an access control request to the object manager, and receives the result of the object manager's implementation of access control. The authentication server is responsible for verifying the identity of the principal represented by the user process. Important security servers are started by the server loader in a safe and credible manner after the integrity check is performed, and the server loader is also responsible for the configuration and management of trusted servers. The enforcer has the ability to control all requests sent to the server, intercepts all user requests, and realizes the characteristics of comprehensive verification. It is the basis of the access control subsystem ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com