Backup device and mobile memory apparatus bound method and backup device
A mobile storage device and a technology for installing equipment, which is applied in the field of information security, can solve the problem of unreliable binding between backup devices and mobile storage devices, and achieve the effect of reliable binding and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
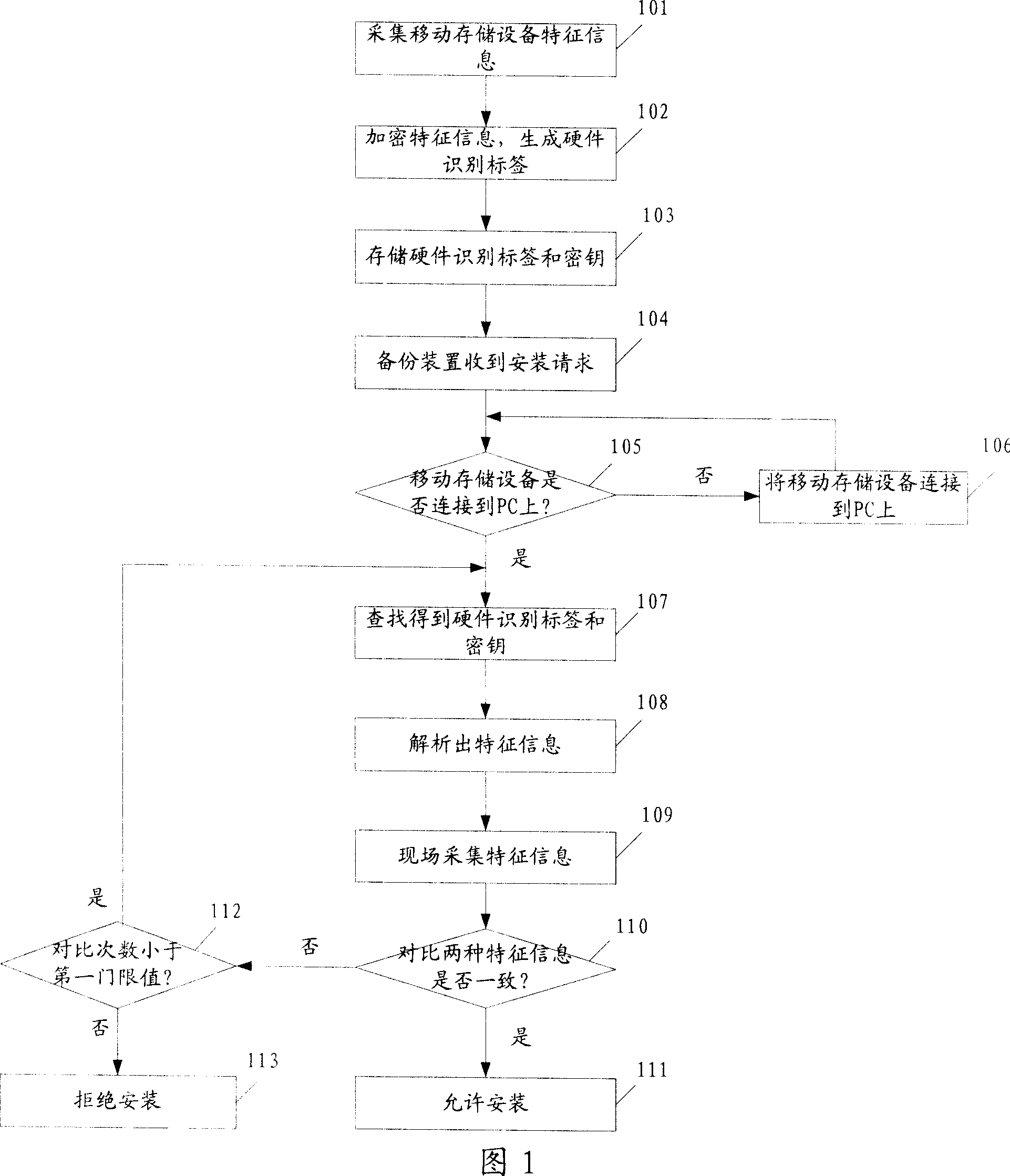
[0056] Generally speaking, Embodiment 1 includes: collecting the feature information of the mobile storage device, encrypting and generating a hardware identification tag, storing the hardware identification tag and its key in the hidden area of the mobile storage device; installing the backup device on the installation device (PC ), the backup device verifies the hardware identification label, and decides whether to allow the installation operation according to the verification result.
[0057] As shown in Figure 1, Embodiment 1 includes:
[0058] Step 101: Collect characteristic information of the mobile storage device;
[0059] Wherein, the feature information may include: PID / VID, manufacturer information, file system, capacity, etc. of the mobile storage device, and may also be adjusted according to actual needs.
[0060] Step 102: using the key to encrypt the feature information to generate a hardware identification tag;
[0061] Among them, the key is randomly gener...
Embodiment 2
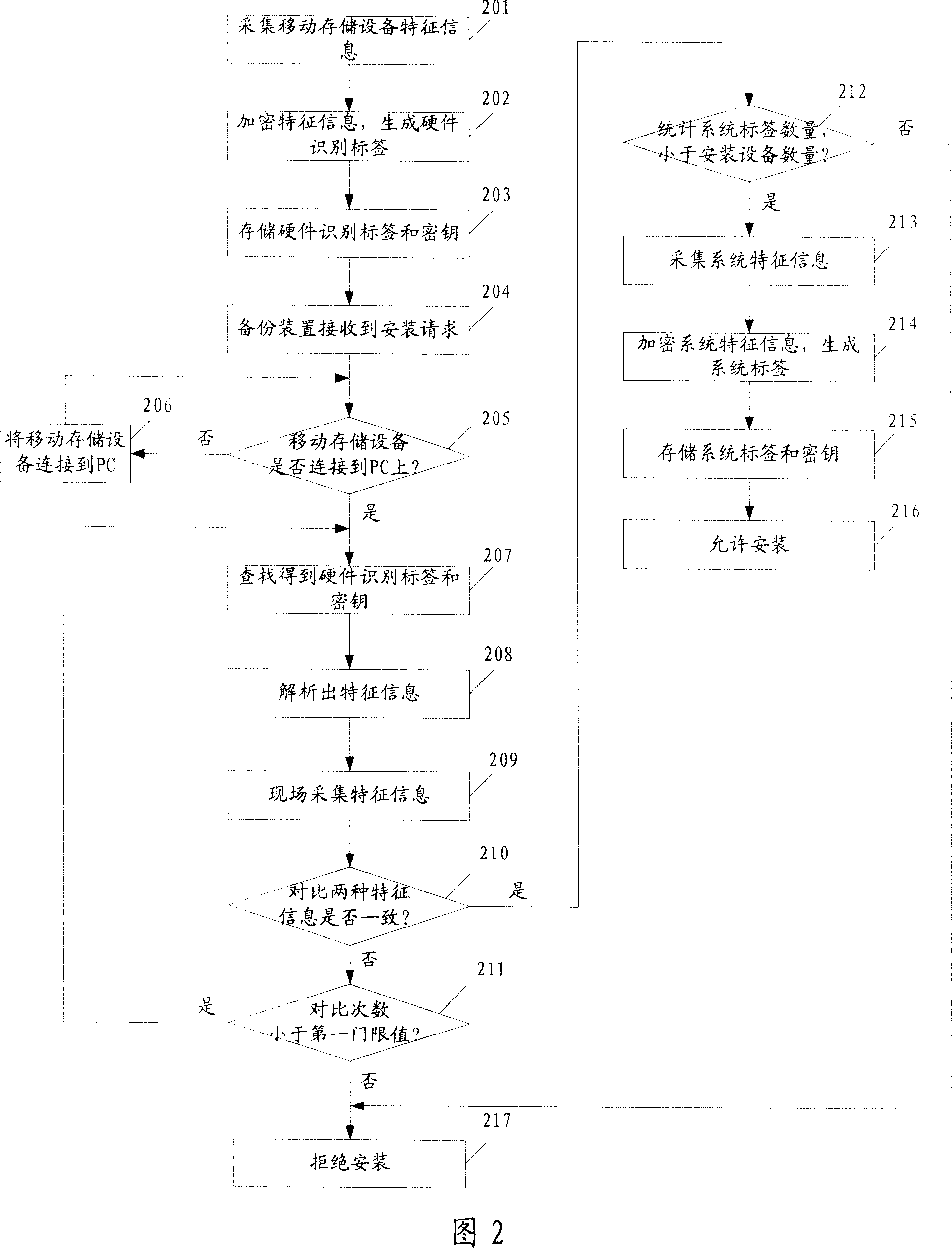
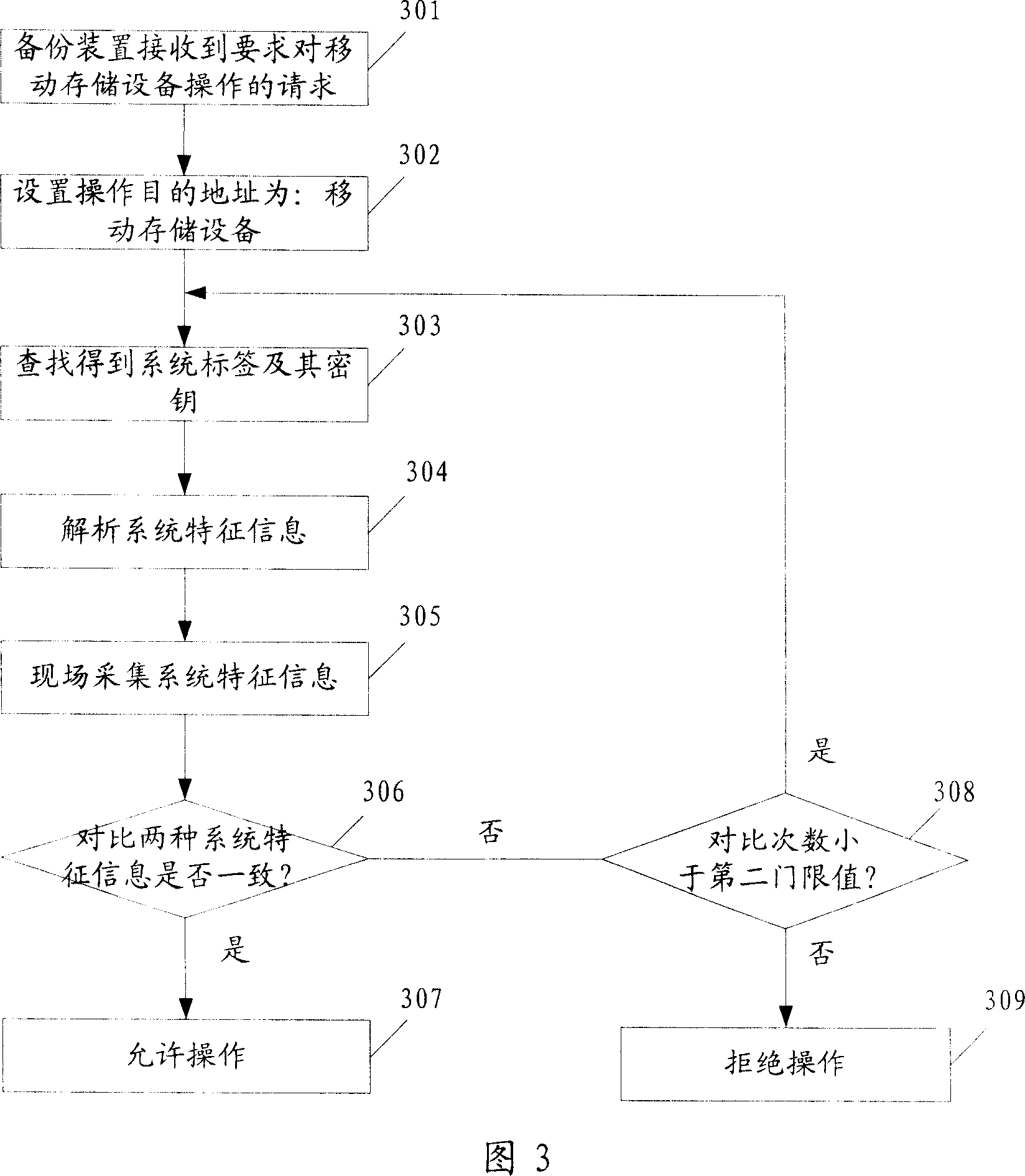
[0083] Compared with the first embodiment, the most fundamental difference of the second embodiment is the introduction of a new system label. The system label is generated when the backup device is installed, and is stored in the mobile storage device; the number of devices (PCs) on which the backup device is installed is limited by the number of system labels.
[0084] Moreover, when using the backup device to perform operations such as data backup or data restoration on the mobile storage device, the system label must be verified, which makes the binding of the backup device and the mobile storage device more tightly.
[0085] As shown in FIG. 2 , steps 201 to 210 are the same as the corresponding steps in the first embodiment. Embodiment two includes:
[0086] Step 201: collecting characteristic information of the mobile storage device;
[0087] Step 202: using the key to encrypt the feature information to generate a hardware identification tag;
[0088] Step 203: stori...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com