An intrusion detection system based on distinct network
A unique, network technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as difficult identification, inability to clone and amplify antibodies, and inability to retain features, and achieve good detection performance and false positives. Low rate and false negative rate, avoid the effect of regular updates
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The detailed description and technical contents of the present invention are described below in conjunction with the accompanying drawings.
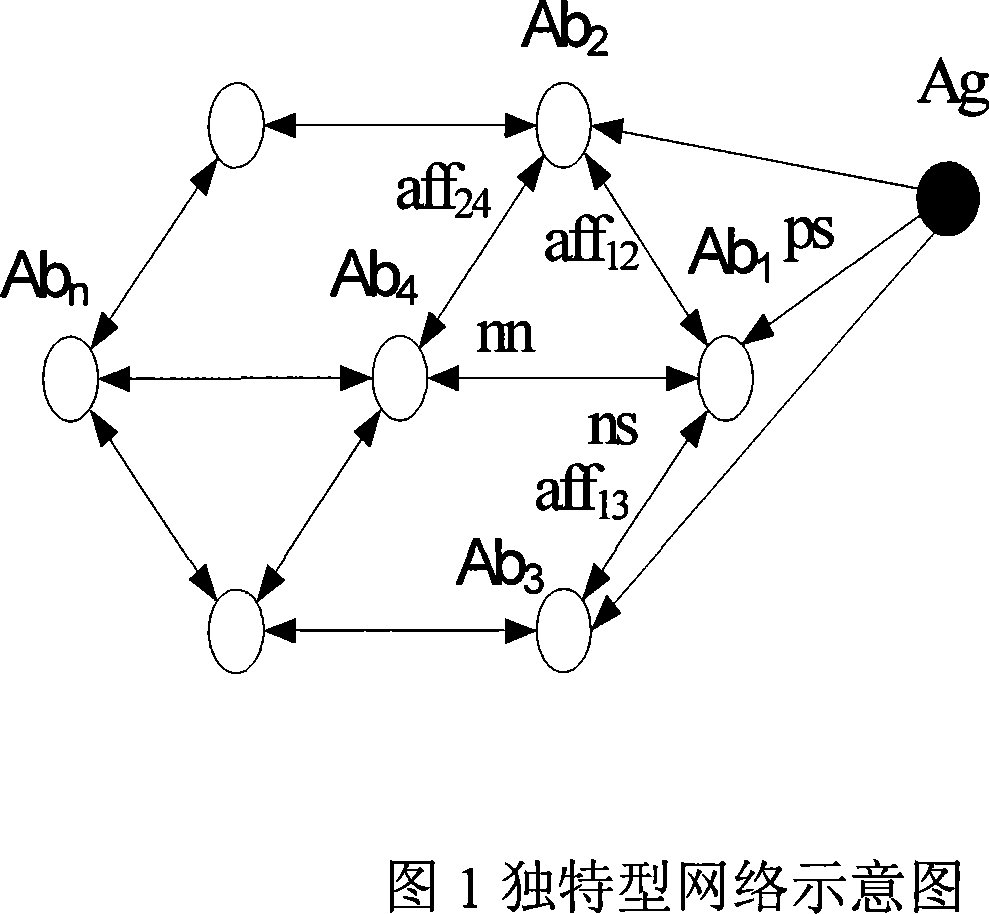
[0020] Referring now to FIG. 1, the method for establishing an idiosyncratic network of the present invention is illustrated.
[0021] Antibody Ab 1 Because it matches the antigen Ag and recognizes the antigen Ag, it is stimulated (ps). Ab 1 with another antibody Ab 4 match and are therefore stimulated (ns) and inhibited (nn). Antibody Ab 4 It is called the internal image of the antigen Ag in the network, because it can be recognized by the same antibody Ab of the antigen Ag 1 recognized. Usually there is more than one internal image, and it is usually a set, because there are more than one antibody that can recognize the antigen, as shown in Figure 1 Ab 2 and Ab 3 . In addition, antibody Ab 2 and Ab 3 It can also be matched with other antibodies, and there is also a stimulating and inhibitory effect between them, thus ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com