Mixed network working software system antipirating method
A software system and mixed network technology, applied in the direction of instrument, program/content distribution protection, electronic digital data processing, etc., can solve the problems of poor confidentiality, high cost, and inability to limit the use time, etc., to achieve strong anti-cracking ability and low cost Low, enhance the effect of anti-tracking cracking ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
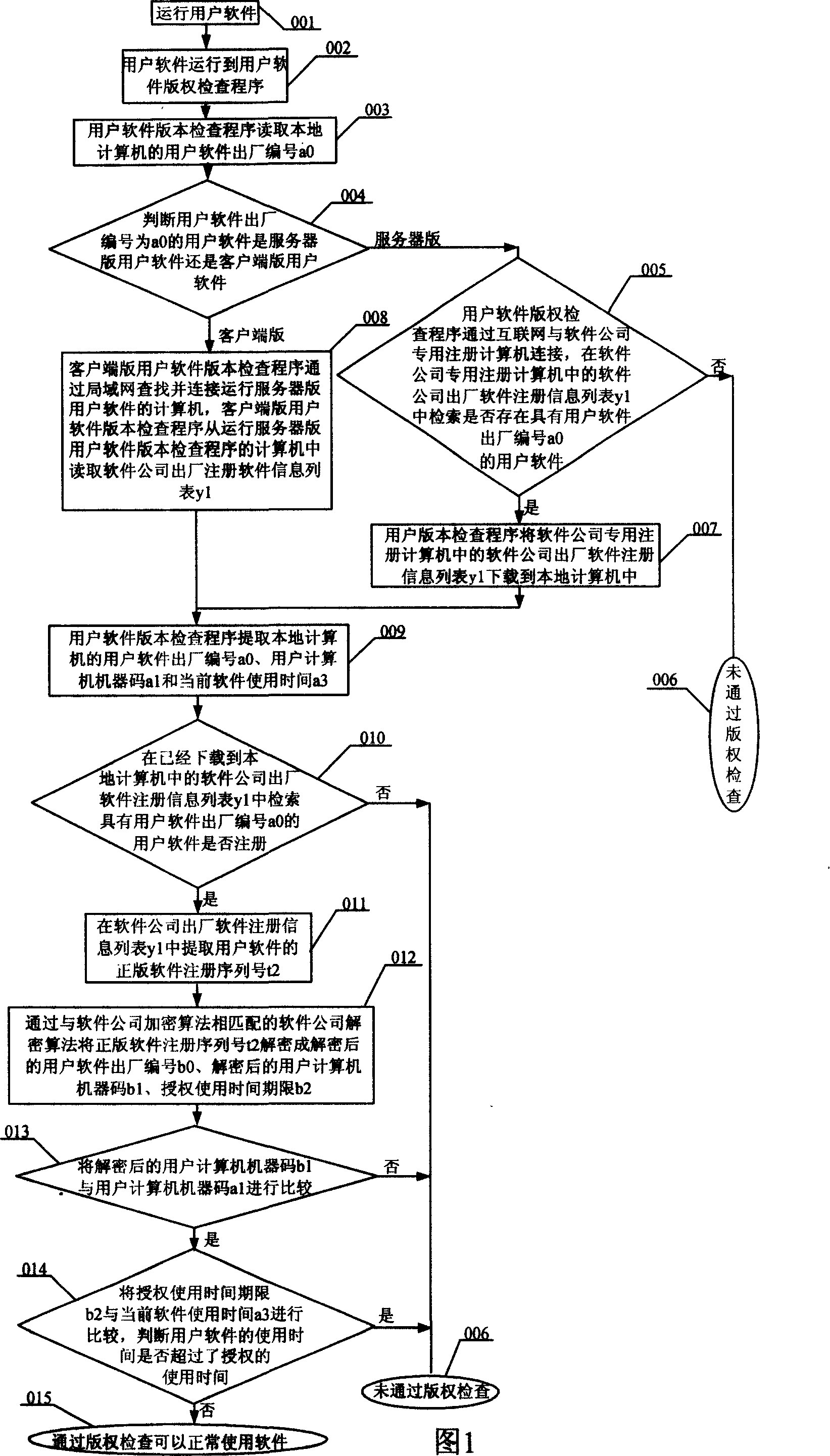
[0026] Specific embodiment one: below in conjunction with Fig. 1 specific description present embodiment, present embodiment is completed by the following steps:
[0027] Run user software 001;
[0028] The user software runs to the user software copyright check program 002;
[0029] The user software copyright checking program reads the factory number a0 003 of the user software of the local computer;
[0030] Determine whether the user software whose factory number is a0 is the server version user software or the client version user software 004;
[0031] If it is the "server version", the user software copyright check program is connected to the software company's dedicated registration computer through the Internet, and searches whether there is a user with the user software's delivery number a0 in the software company's factory software registration information list y1 in the software company's dedicated registration computer. Software 005;
[0032] No, copyright check...
specific Embodiment approach 2
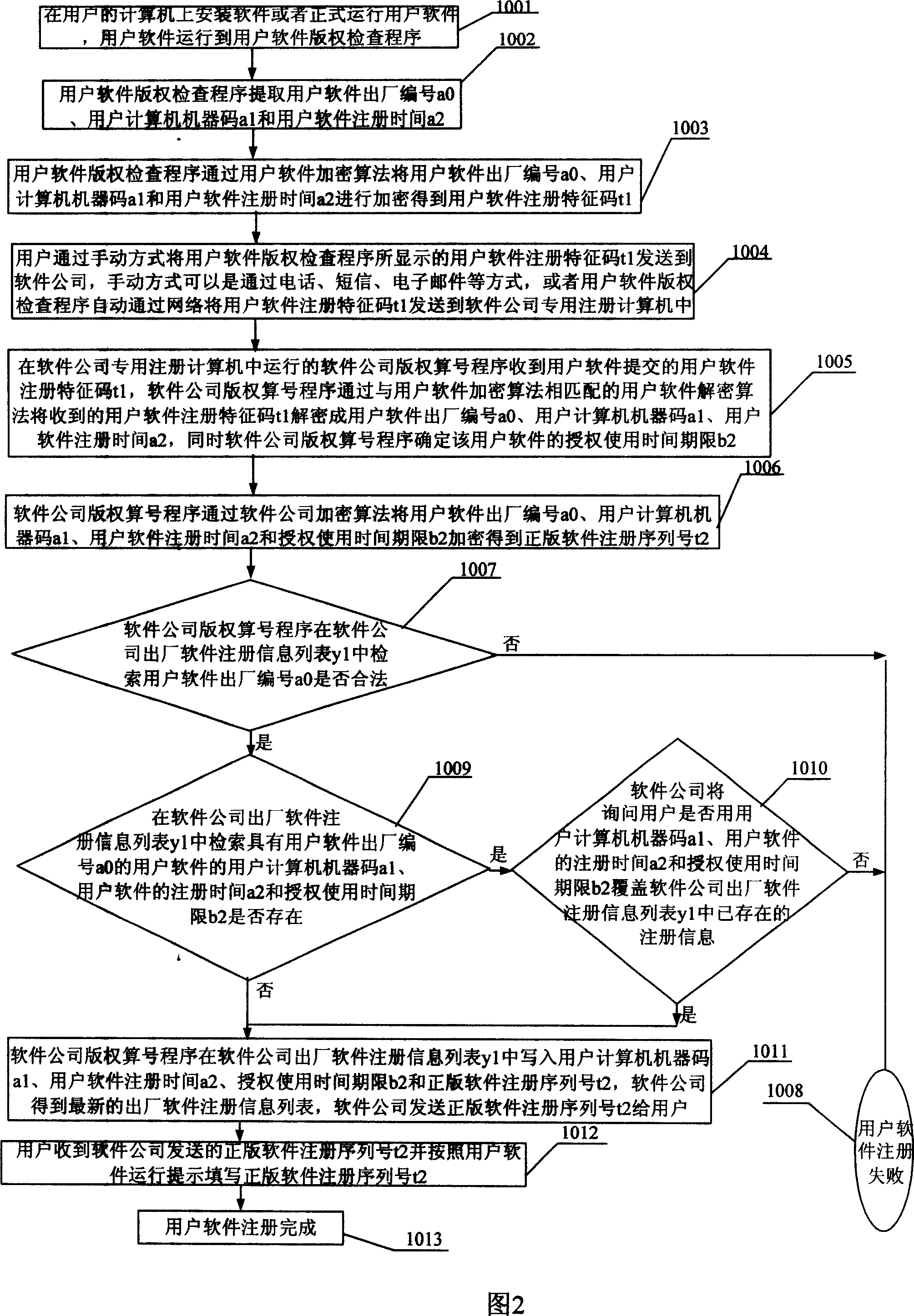
[0045] Specific embodiment two: below in conjunction with Fig. 2, specifically illustrate this embodiment, the registration process of user software among the present embodiment step 010 is finished by the following steps:
[0046] Install software on the user's computer or officially run the user software, and the user software runs to the user software copyright checking program 1001;
[0047] User software copyright checking program extracts user software factory number a0, user computer machine code a1 and user software registration time a2 1002;
[0048] The user software copyright inspection program encrypts the user software factory number a0, the user computer machine code a1 and the user software registration time a2 through the user software encryption algorithm to obtain the user software registration feature code t1 1003;
[0049] The user manually sends the user software registration feature code t1 displayed by the user software copyright check program to the sof...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com