Protection system for data security transmission between computer and disc
A data security and protection system technology, applied in computer security devices, digital data protection, computing, etc., can solve problems such as low efficiency, inability to realize data security transmission, confidential data leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
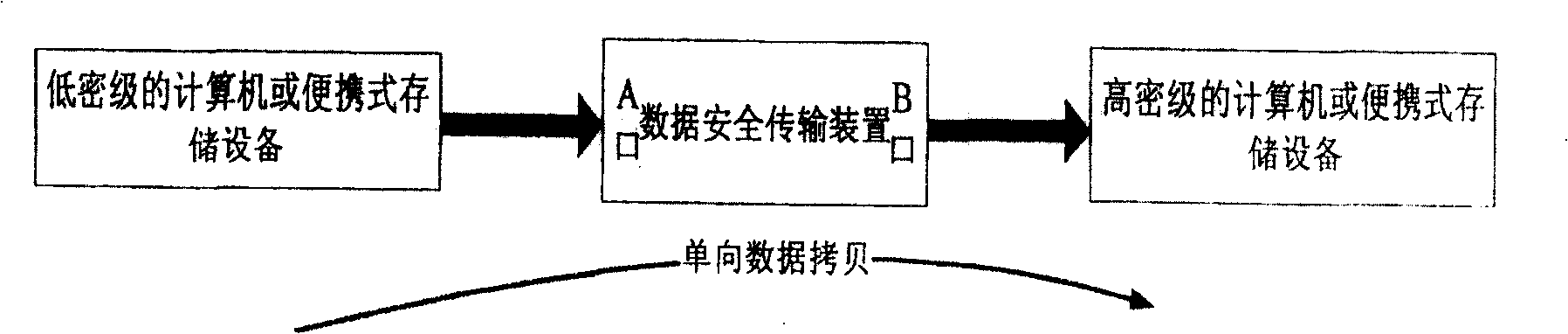
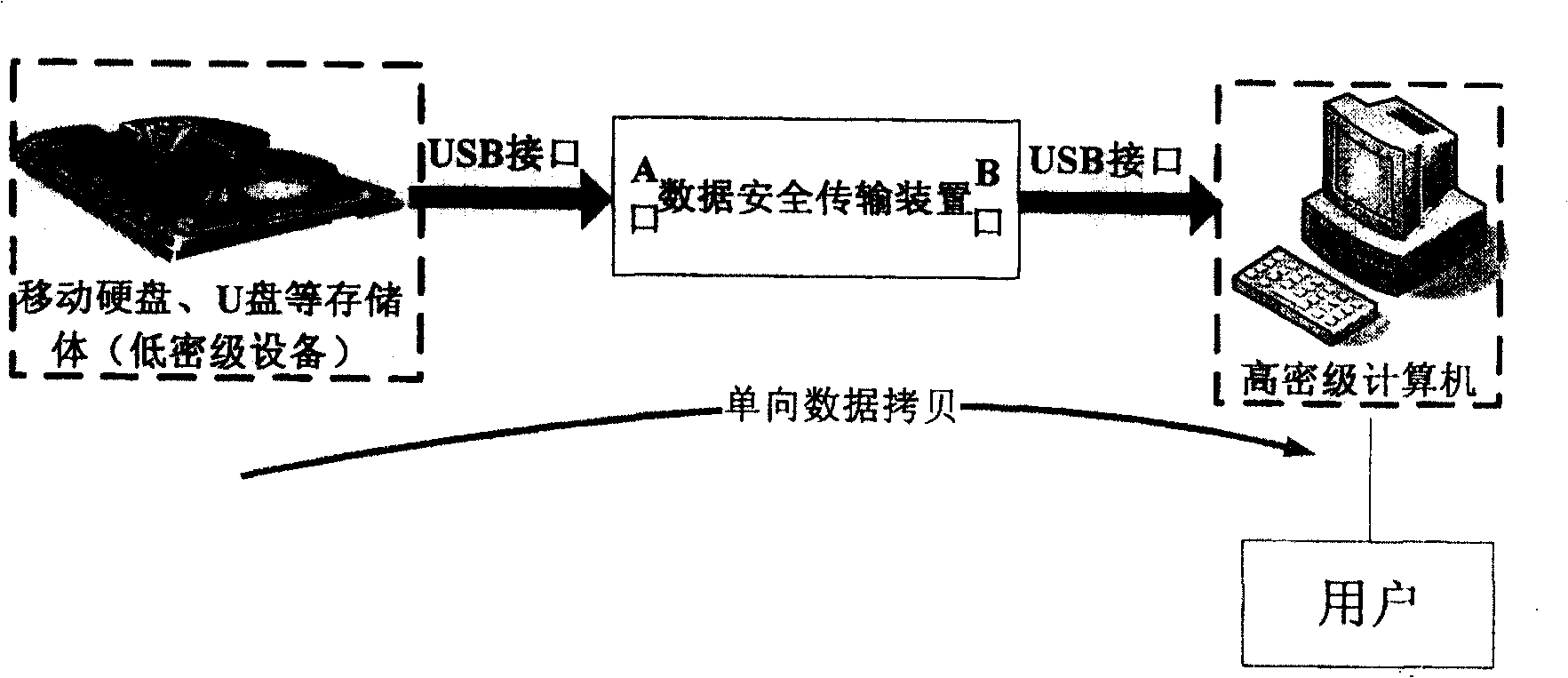
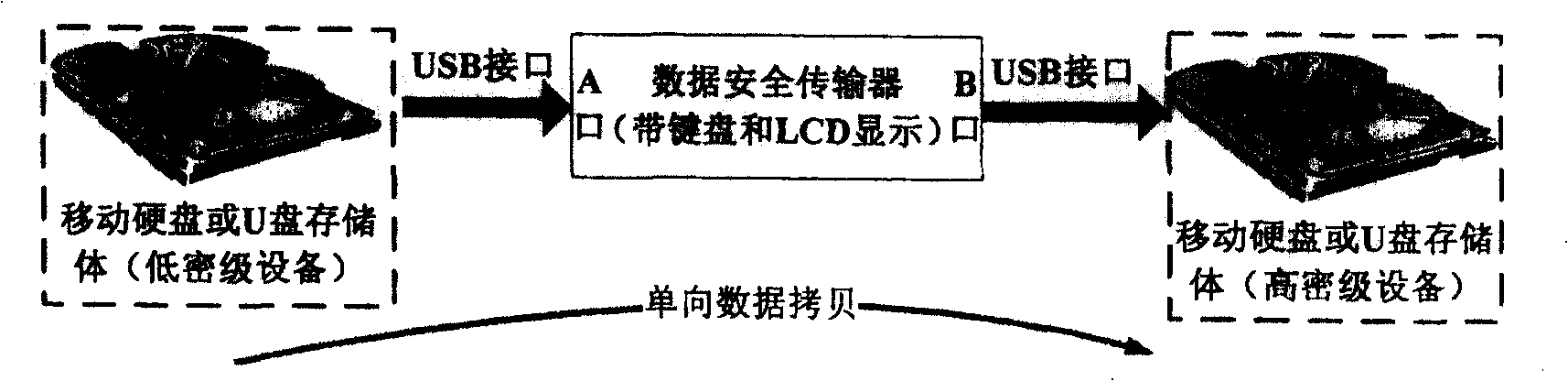
[0027] figure 1 It is a simple schematic diagram of the system to be designed, wherein the "data security transmission device" is the hardware core device to be realized in the present invention. The device mainly has two USB interfaces (but the interface can also use COM port, Ethernet port or their various combination interfaces, etc.), one is A port, which is used to connect low-density portable storage devices or computers; the other is B port. Port, used to connect high-density mobile hard disk, U disk or computer. When working, the data of the low-secret equipment connected to port A is read in through the USB interface of the data security transmission device, and then the data just read is output to the connected high-secret computer or portable device through the USB interface of port B in the device. In order to ensure that the secret-related data in the high-secret equipment connected to the B port will not leak to the low-secret equipment connected to the A port,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com