Secure, efficient, and mutually authenticated cryptographic key distribution
a cryptographic key and mutual authentication technology, applied in the direction of wireless communication, eavesdropping prevention circuits, instruments, etc., can solve the problems of limited computational capabilities and inefficient authentication and authorization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
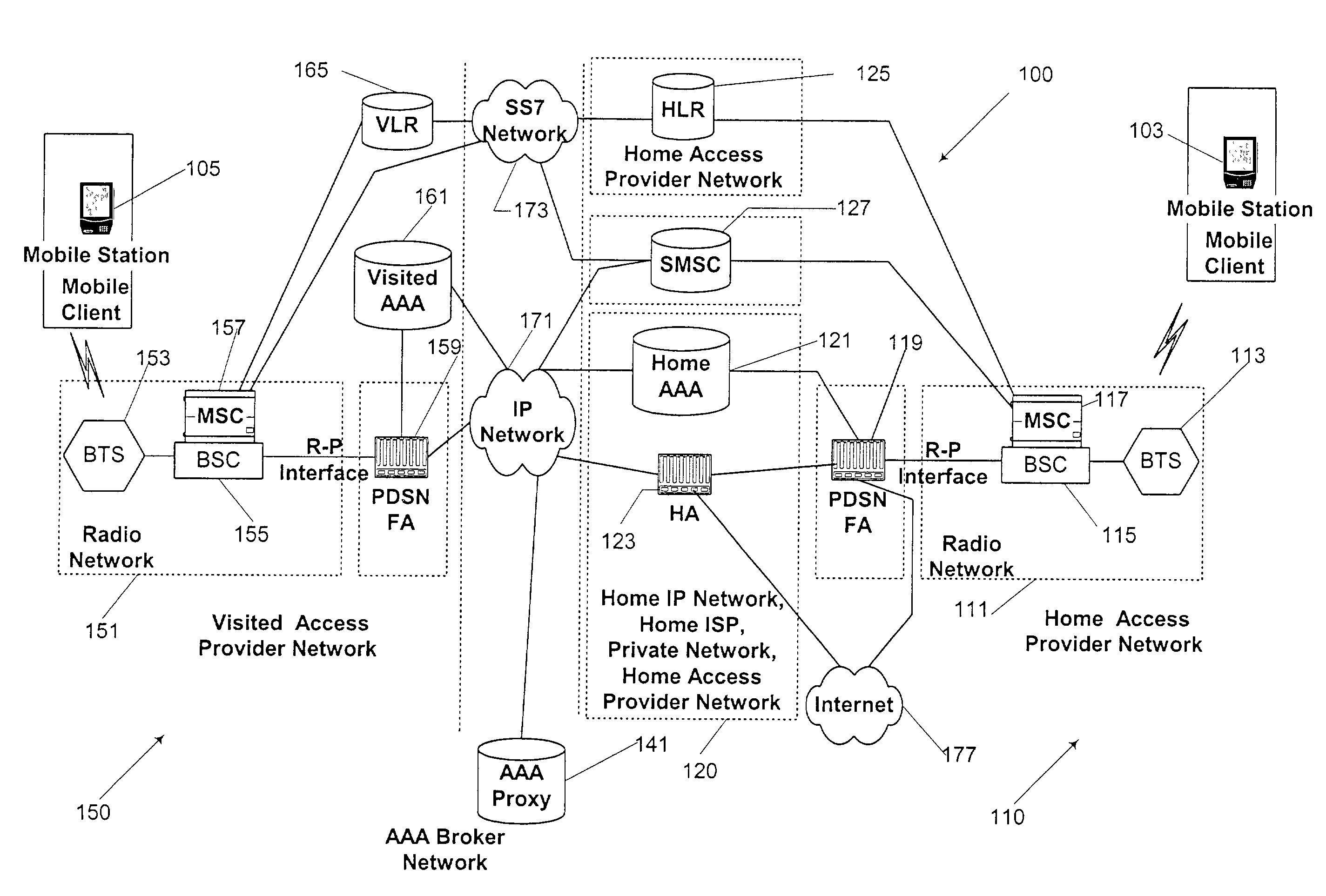
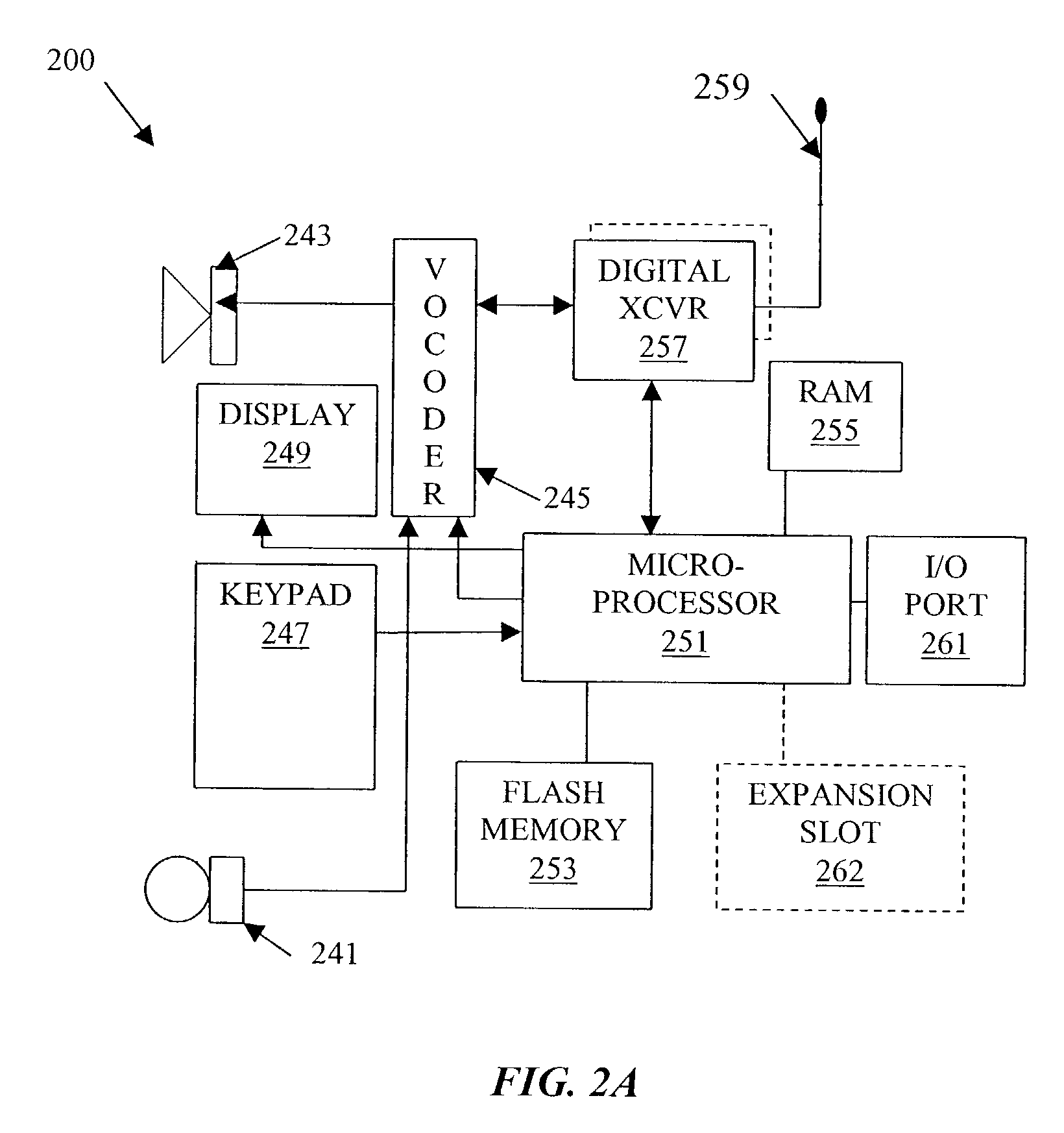
[0033]The present systems and methods provide secure, efficient, and mutually authenticated cryptographic key distribution. Such systems and methods allow a client or client manufacturer to pre-generate and pre-encrypt cryptographic keys, store the encrypted keys within the client, and deliver such keys to a serving network's access server via the client. Such systems and methods may also rely upon, if available, authentication performed by a trusted access server of an intermediate network which the client must traverse in order to obtain access the serving network. If not available, a client password stored within the client may be used to enable client authentication by the serving network prior to acceptance of the delivered cryptographic keys. A particularly advantageous use of the key distribution in accordance with the present invention relates to distribution of encryption keys to wireless portable communication terminals. Although, in various embodiments, other types of dev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com