Apparatus and method for exchanging cryptographic information with reduced overhead and latency
a cryptographic information and overhead-reducing technology, applied in the field of cryptographic information exchange, can solve the problems of key encryption, more computation and/or memory, and difficulty in secure key exchange itsel
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
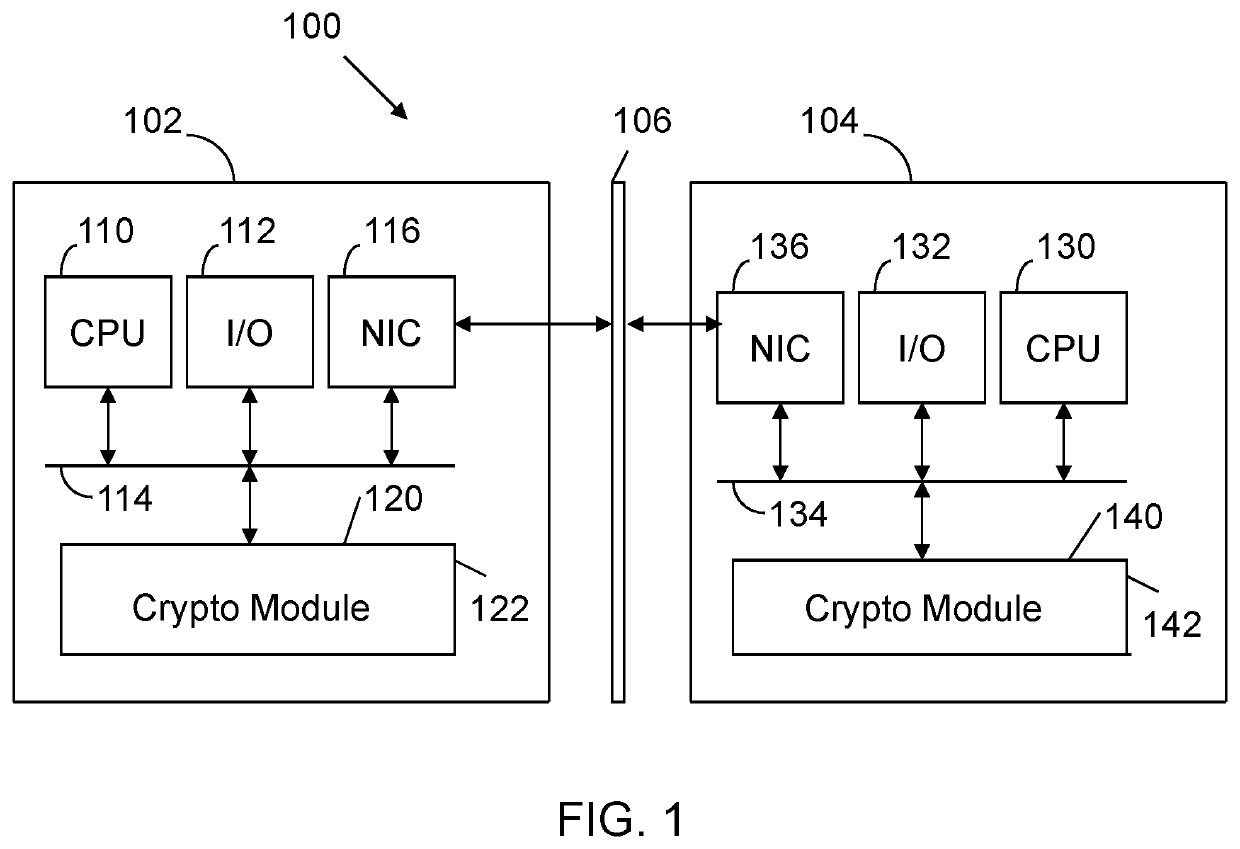
[0017]FIG. 1 illustrates a system 100 including a first computer 102 associated with a first user and a second computer 104 associated with a second user. The first computer 102 and second computer 104 communicate via a network 106, which may be any combination of wired and wireless networks. The first computer includes a processor (e.g., central processing unit or CPU) 110 and input / output devices 112 connected via a bus 114. The input / output devices 112 may include a keyboard, mouse, touch display and the like. A network interface circuit 116 is also connected to the bus 114 to provide connectivity to network 106. A memory 120 is also connected to the bus 114. The memory 120 stores a crypto module 122. The crypto module 122 includes instructions executed by processor 110 to implement operations disclosed herein.
[0018]The second computer 104 includes similar components, including a central processing unit 130, input / output devices 132, a bus 134, a network interface circuit 136 and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com