Method and system for identifying service block
A technology for business and grouping information, applied in the field of network communication, can solve the problems of cumbersome users, achieve the effect of simplifying the authentication operation and improving the user experience
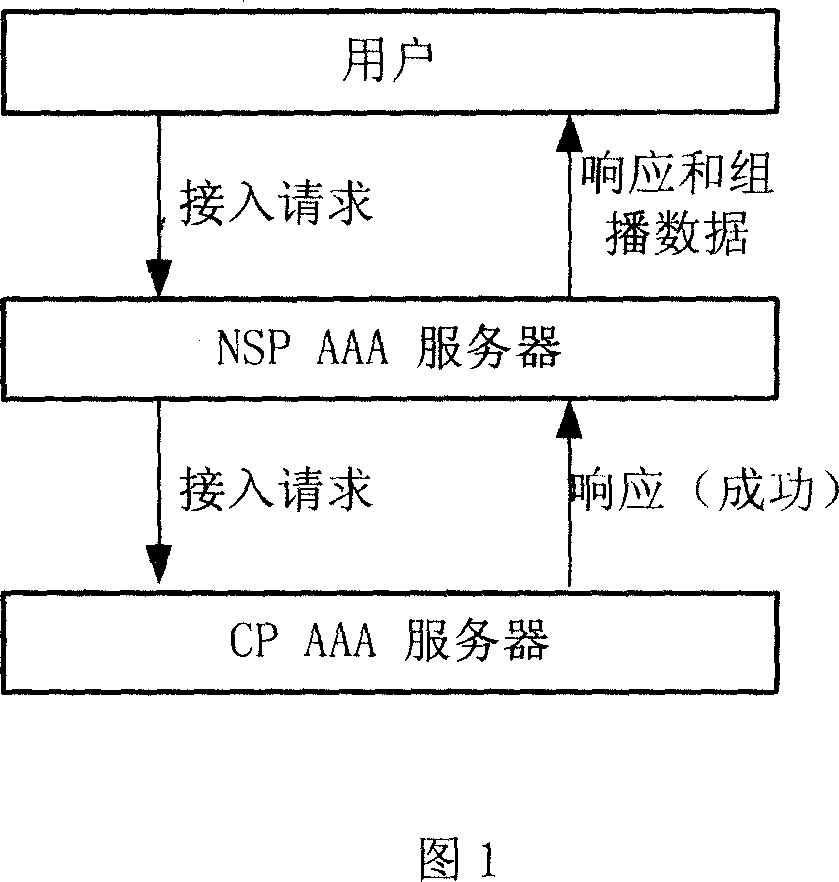
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
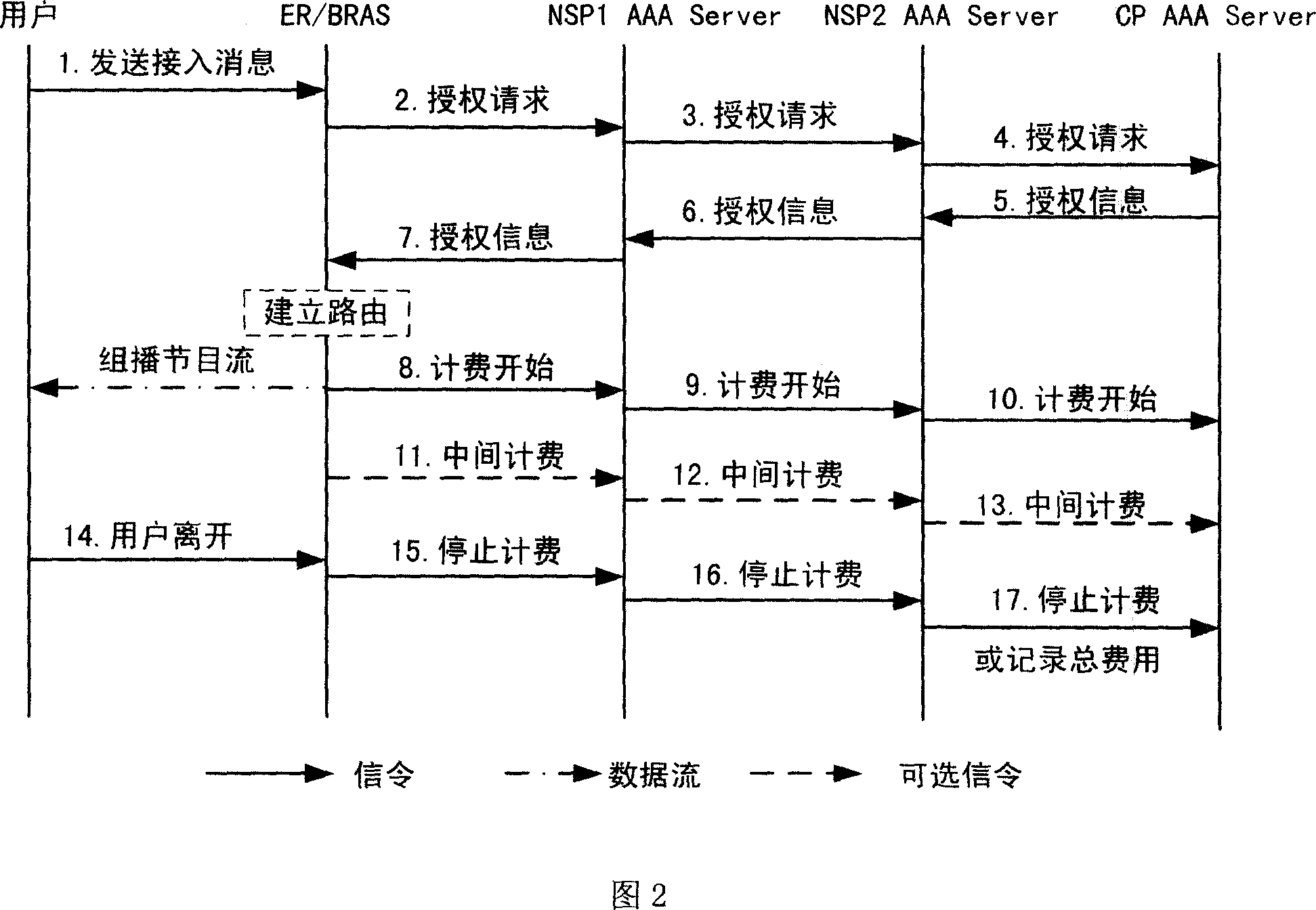
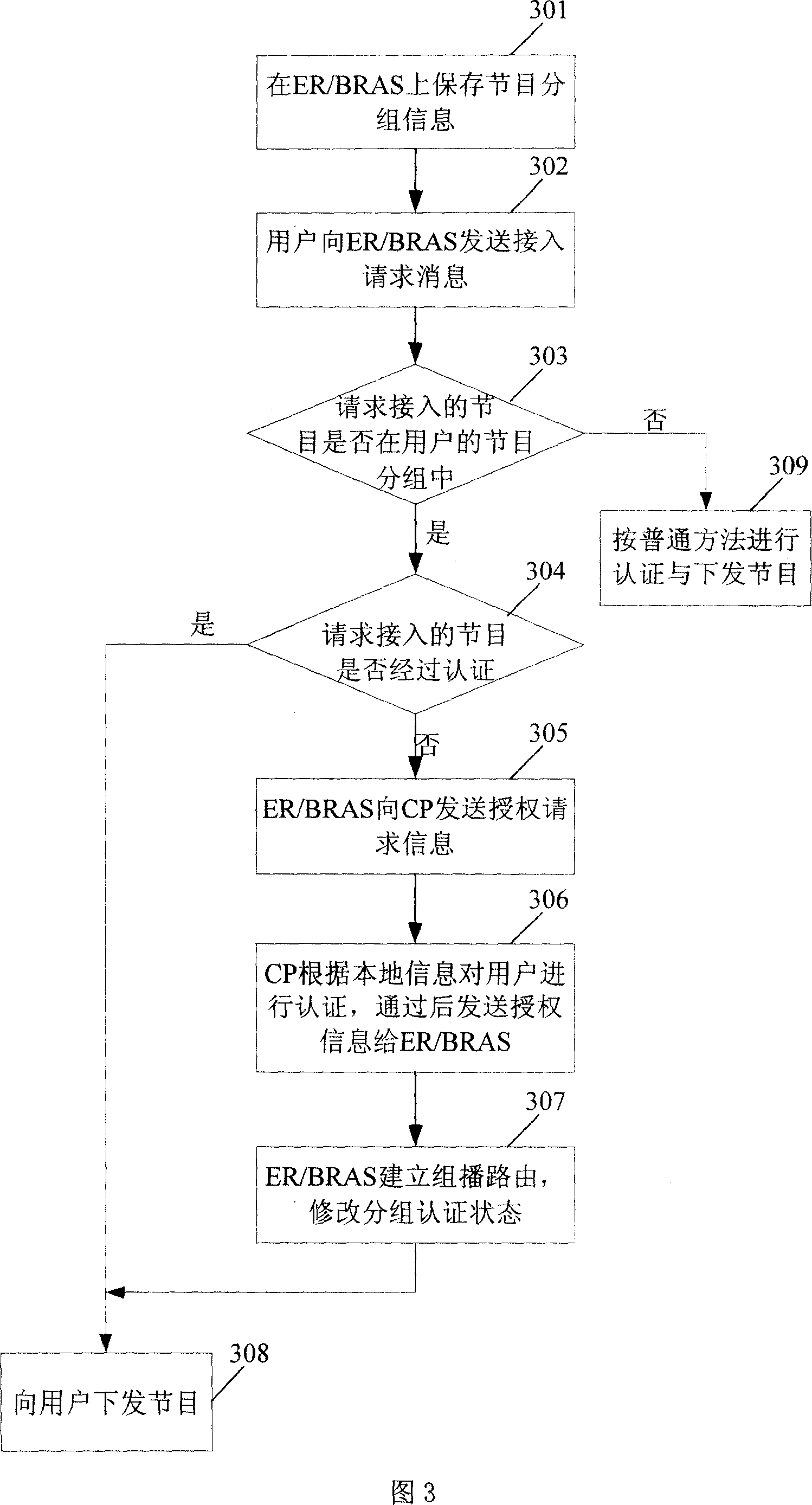
[0051] The present invention is illustrated by taking the user switching multicast program as an example, as shown in Figure 3, the group authentication method includes the following steps:
[0052] Step 301: The user saves program grouping information on the access device. The access device may be an edge router ER, a broadband remote access server BRAS or a digital subscriber line access multiplexer DSLAM, and this embodiment selects ER or BRAS.
[0053] Step 302: the user sends an access Join request message to the ER / BRAS.
[0054] Step 303: When the ER / BRAS receives the Join message sent by the user, it automatically judges whether the program accessed this time is in the user program group according to the locally saved information, and executes Step 304; otherwise, executes Step 309.
[0055] Step 304: Analyze the authentication status of the group. If the group is not authenticated, execute step 305, and if the group is authenticated, execute step 308.
[0056] Step...
Embodiment 2
[0080] The access device in this embodiment still uses the ER or BRAS as an example. The grouping methods of programs can be divided into two categories:
[0081] 1) User-designated program grouping: users can bundle multiple multicast programs into one group according to their own preferences. These programs may come from the same CP, or may be provided by multiple CPs separately; The voice or SMS platform registers its own multicast channel grouping information with the AAA Server or network management system of the NSP; then the information is sent to ER / BRAS by the AAA Server or network management system, and ER / BRAS completes initialization after receiving the information operate. The group information may include group number, multicast service code, user identity information (optional) and other information. Taking the user to register / cancel the grouping information with the network management system through the web page, and the network management system sending the...
Embodiment 3
[0095] Referring to Figure 7, a system for business group authentication, the system includes:
[0096] User equipment: Initiate a request to access services and provide user identity authentication information, which can be set-top boxes, PCs, and other equipment.
[0097] Access device: responsible as AAA Client (customer) and user agent, used to judge whether authentication is required according to the user's access service request, if necessary, initiate authentication operation, store user group information and authentication ID, and perform authentication based on group information Group authentication processing, after the authentication is passed, modify the authentication flag to pass the authentication.
[0098] Wherein, the above access device may be ER / BRAS / DSLAM.
[0099] Additionally, the system includes:
[0100] Web site: Optional, as an interface for users to set group information in the system, the Web site can be replaced by the voice or SMS service platfo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com