False code prevention method and prevention program and the program recording medium
一种非法代码、程序的技术,应用在使用存储的程序进行程序控制、程序控制设计、仪器等方向,能够解决不能够完全把握非法代码执行等问题,达到抑制执行的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0071] Hereinafter, the best embodiment of the present invention will be specifically explained based on the drawings.
[0072] [Embodiment 1]
[0073] Hereinafter, Embodiment 1 of the present invention will be described.
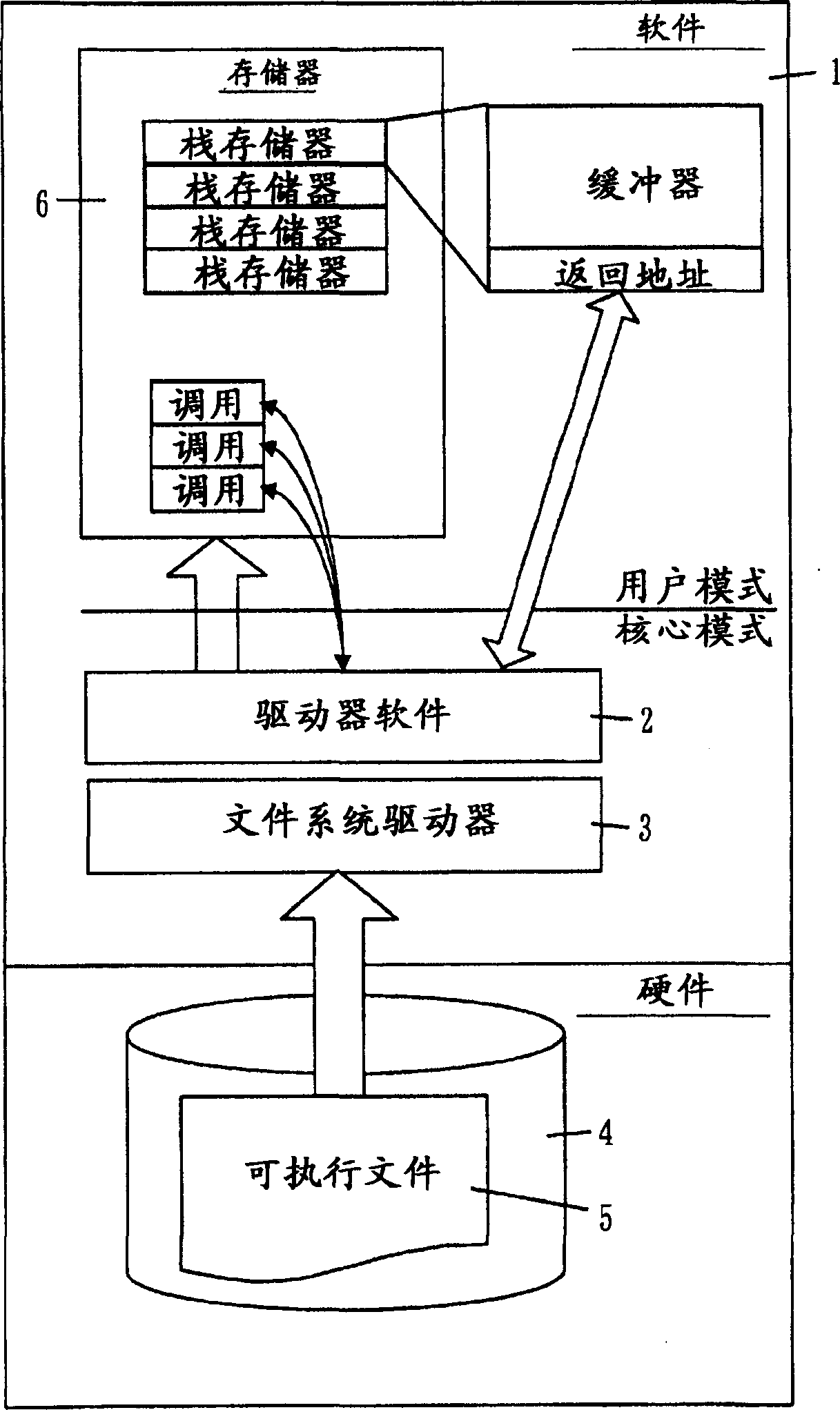
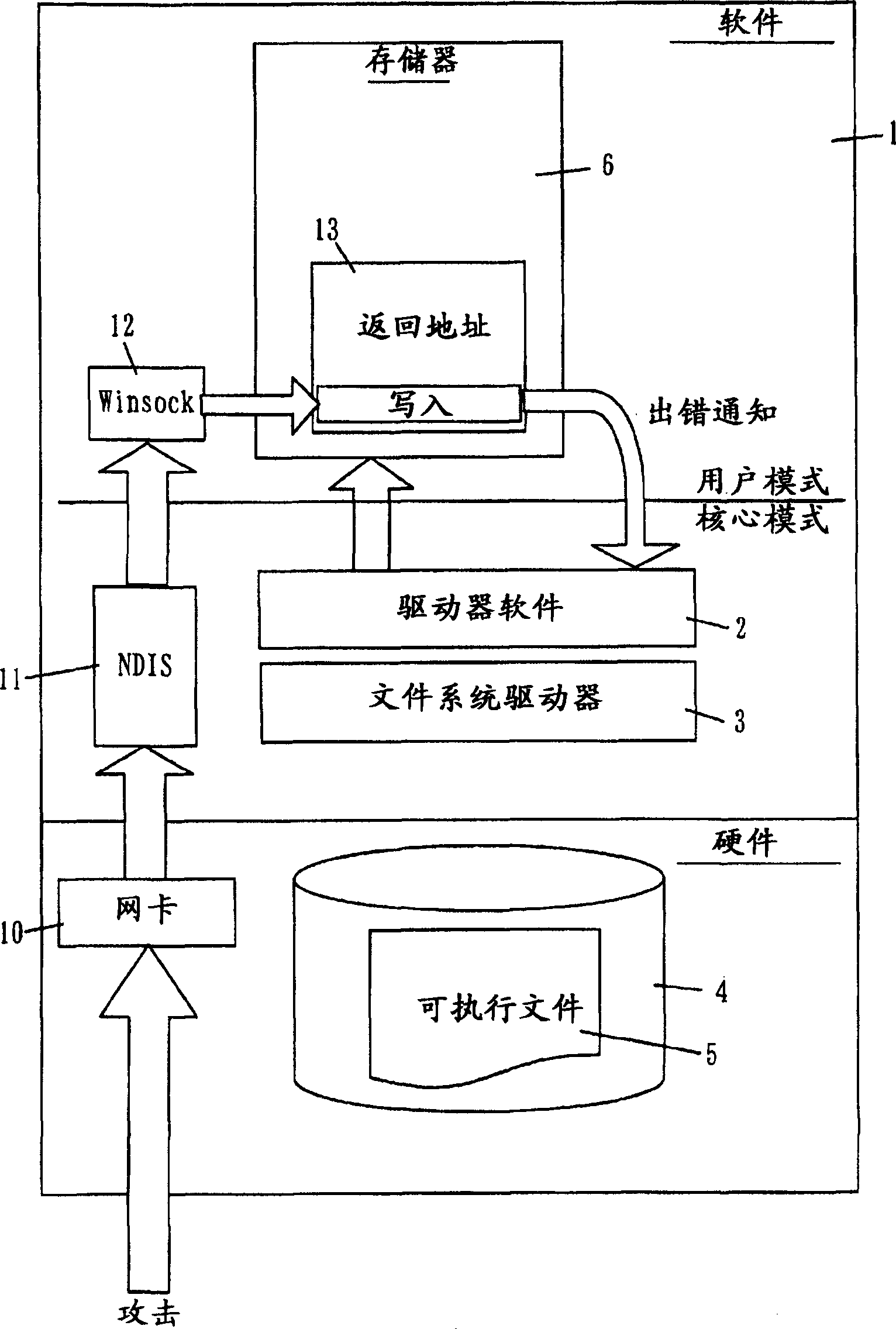
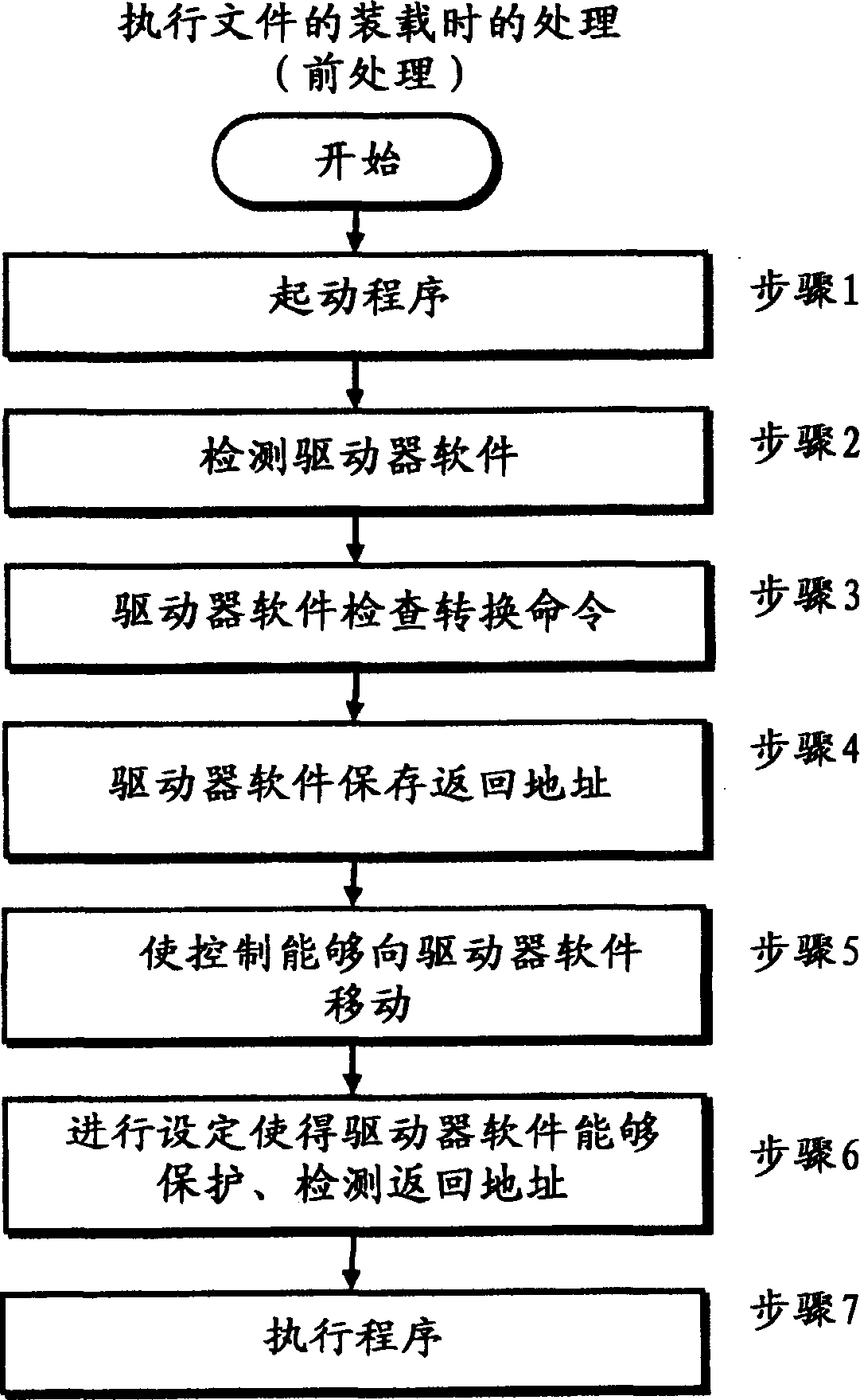
[0074] The present invention provides a method for detecting the behavior of rewriting or tampering with data stored in the main memory of an electronic computer. In addition, a program is provided for detecting the act of rewriting or tampering with data stored in the main memory of the electronic computer according to this method, and restoring the rewritten or tampered data. Furthermore, the present invention provides a recording medium on which the program is recorded. The outline of the embodiment of the present invention will be described.
[0075] The troubleshooting function of the CPU is a function for detecting errors that occur while executing an application program. For this reason, a plurality of memories called troubleshooting registers are prepar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com