Statistic handwriting identification and verification method based on separate character
A verification method, handwriting technology, applied in character and pattern recognition, computing, computer parts, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0236] Embodiment 1: handwriting identification system
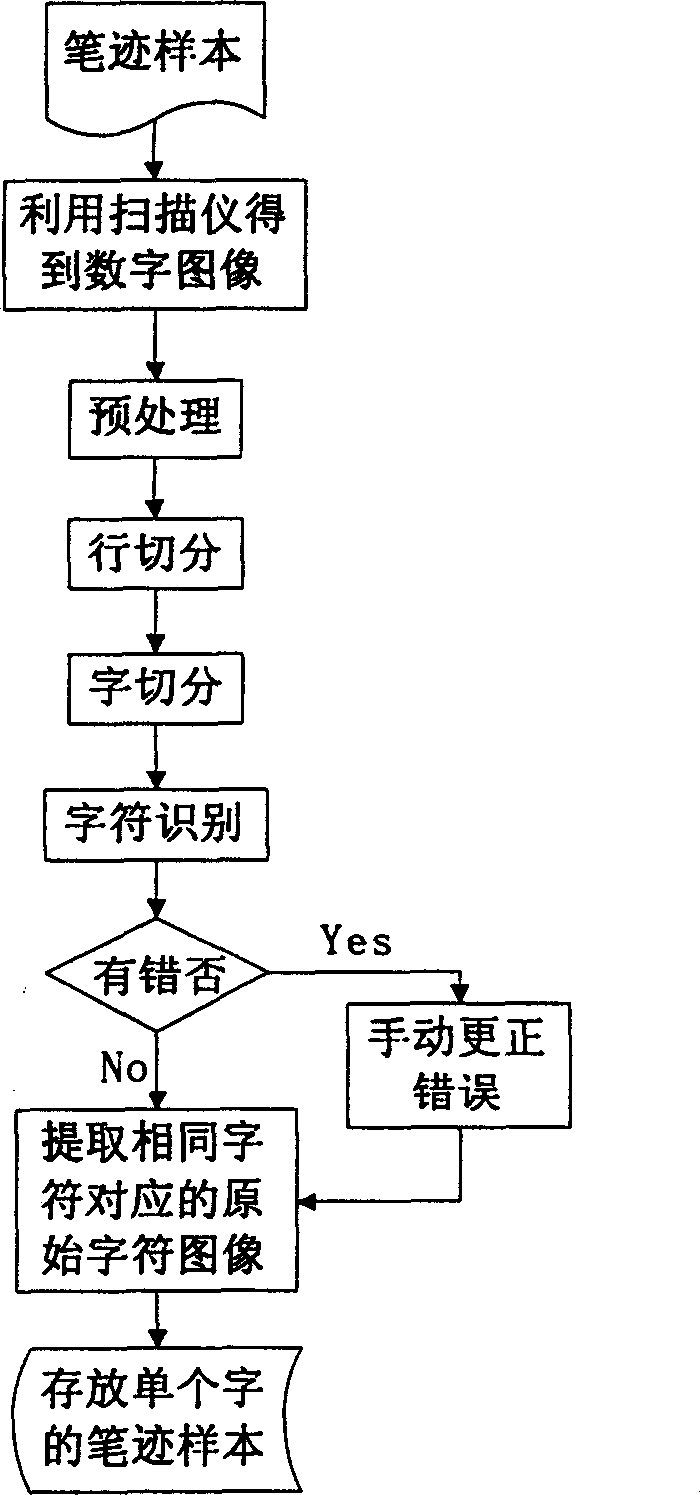
[0237] Handwriting identification system based on the present invention such as Figure 11 shown. In the experiment, 16 pages of handwriting documents written by 27 people were used, and each page contained 20 handwritings of Chinese characters. First use a scanner to input these handwriting documents into a computer, and then use OCR software to obtain handwriting samples of individual characters. Normalize each single-character handwriting sample to a size of 65×65. The division method of neutron blocks in four-direction line element feature extraction is as follows: Figure 7 way of division. Here N 1 =13, L=5, N 2 =7. according to Figure 4 The process extracts four-directional linear feature. Two methods are used for feature transformation, one is the direct LDA transformation method, 10 samples are used for training, and 6 samples are used for testing. The experimental results are shown in Table 1. The ot...
Embodiment 2
[0242] Embodiment 2: Ministry of Public Security handwriting verification (writer verification) system
[0243] The function that the handwriting verification system of the Ministry of Public Security needs to complete is to train a verification database file through a given sample, and judge whether the inspection material is written by the criminal suspect who wrote the sample, so as to provide a basis for judicial judgment. This problem is actually a two-class problem, and the difficulty lies in the fact that the training process is real-time and there are no pseudo-samples.
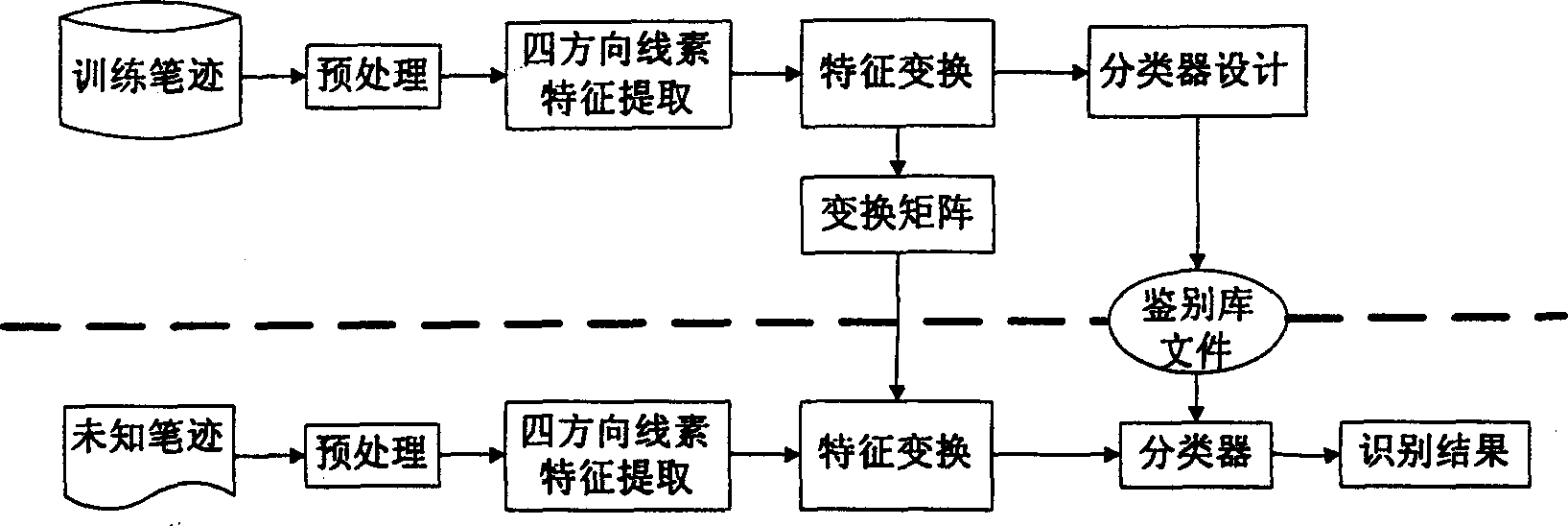
[0244] The block diagram of the whole verification system is as follows: Figure 12 shown. It mainly consists of three parts:
[0245] ●Pseudo sample generation part
[0246] This part is mainly used to generate pseudo-sample library. We use 1806 sets of first-level handwritten Chinese characters (3755 Chinese characters) samples collected by different people in the laboratory as pseudo-samples of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com