Parallel searchable encryption method for resisting internal keyword guessing attack
An encryption method and keyword technology, applied in the field of cryptography, can solve problems such as waste of computing resources, limited application range, matching of multiple keywords, and inapplicability of fuzzy matching, so as to achieve optimal search efficiency and improve search efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
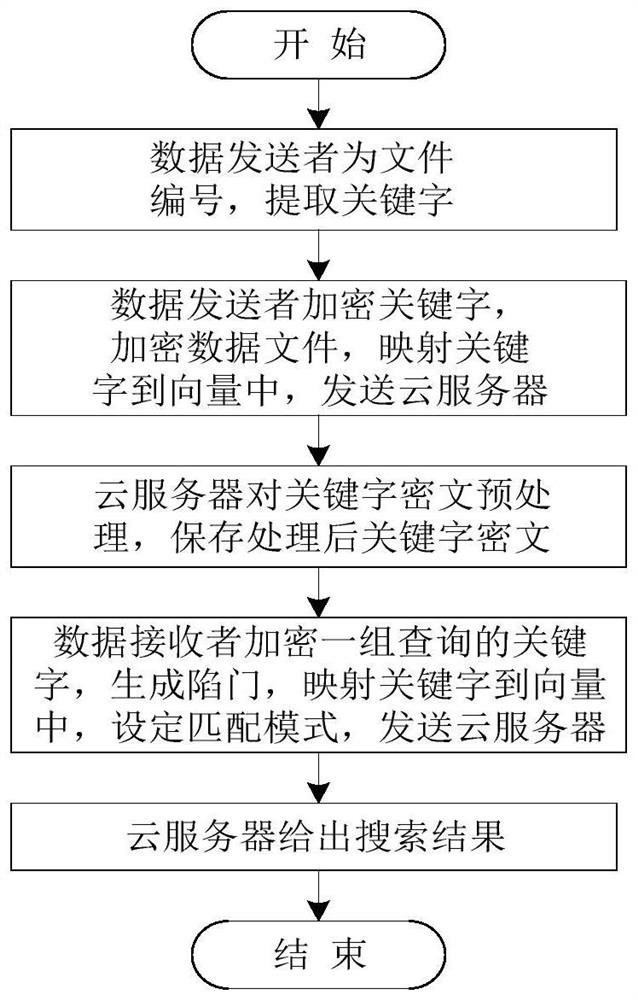
[0052] The present invention will be further described in detail below with reference to the accompanying drawings and examples.
[0053] As shown in the figure, parallel searchable encryption methods resistant to internal keyword guessing attacks are:
[0054] Step (1) establish three-party parameters, including public parameters and private parameters; the details are as follows:
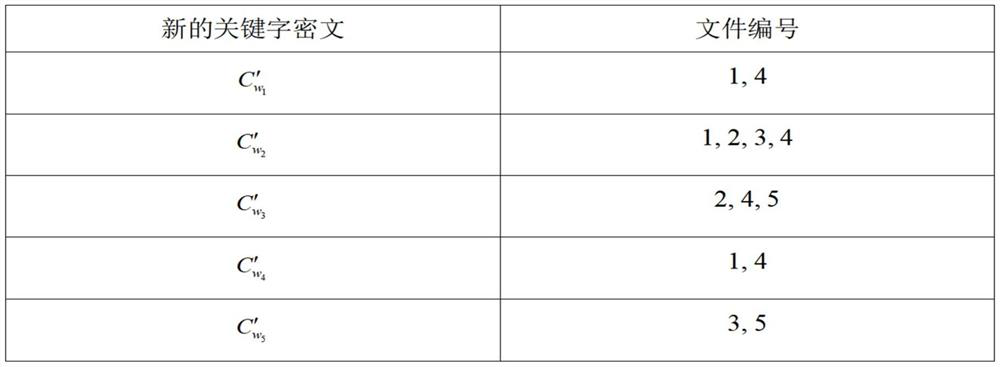
[0055] Initialize the public parameters according to the set security parameter k Choose two multiplicative cyclic groups G according to k 1 and G 2 , the prime number u is the order of the two multiplicative cyclic groups, and g is G 1 the generator of ; A bilinear mapping function G representing an elliptic curve 1 ×G 1 →G 2 , H represents the collision-resistant hash function v h×1 →G 1 , → indicates that the function maps the definition domain of the independent variable to the value domain, v h×1 Represents an h-dimensional vector, and h is set to 3-4 times the number of keywords....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com