Secret communication method based on double-end deployment multi-layer time-delay reserve pool calculation
A technology of secure communication and reserve pool, which is applied in secure communication, calculation, and calculation model through chaotic signals, and can solve the problems of complex coupling mechanism, difficult and low-cost replacement, inflexible selection of encryption system and security system, etc. The effect of secure transmission, improved reliability, and fast chaotic synchronization speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The present invention is described in further detail now in conjunction with accompanying drawing.
[0051] It should be noted that terms such as "upper", "lower", "left", "right", "front", and "rear" quoted in the invention are only for clarity of description, not for Limiting the practicable scope of the present invention, and the change or adjustment of the relative relationship shall also be regarded as the practicable scope of the present invention without substantive changes in the technical content.
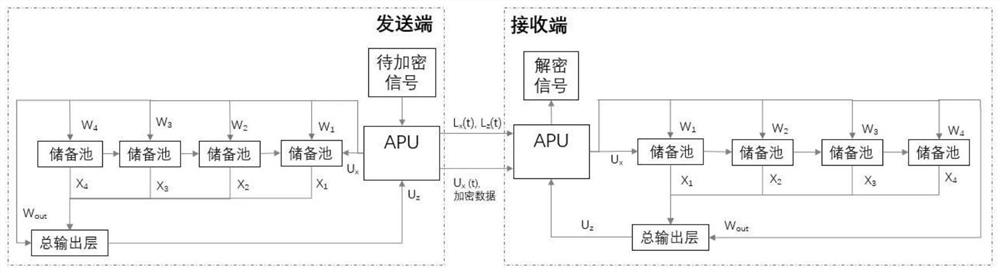
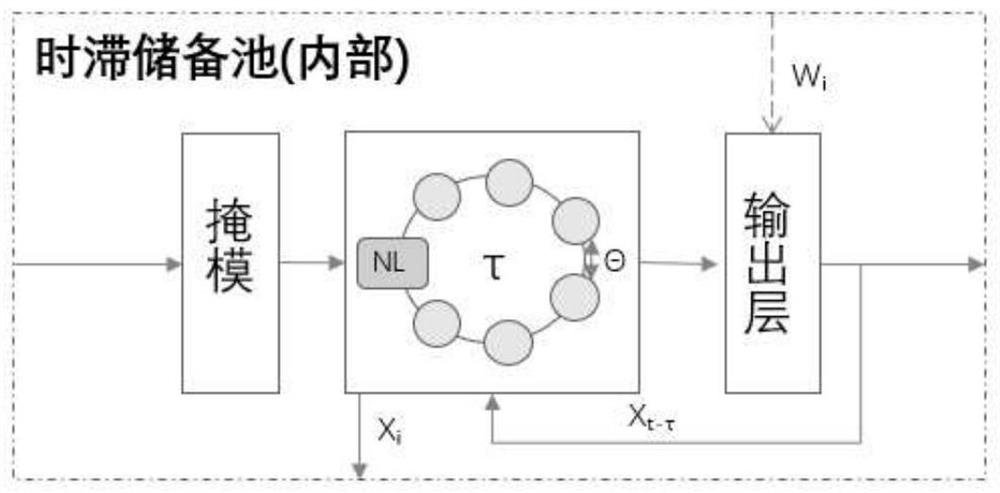
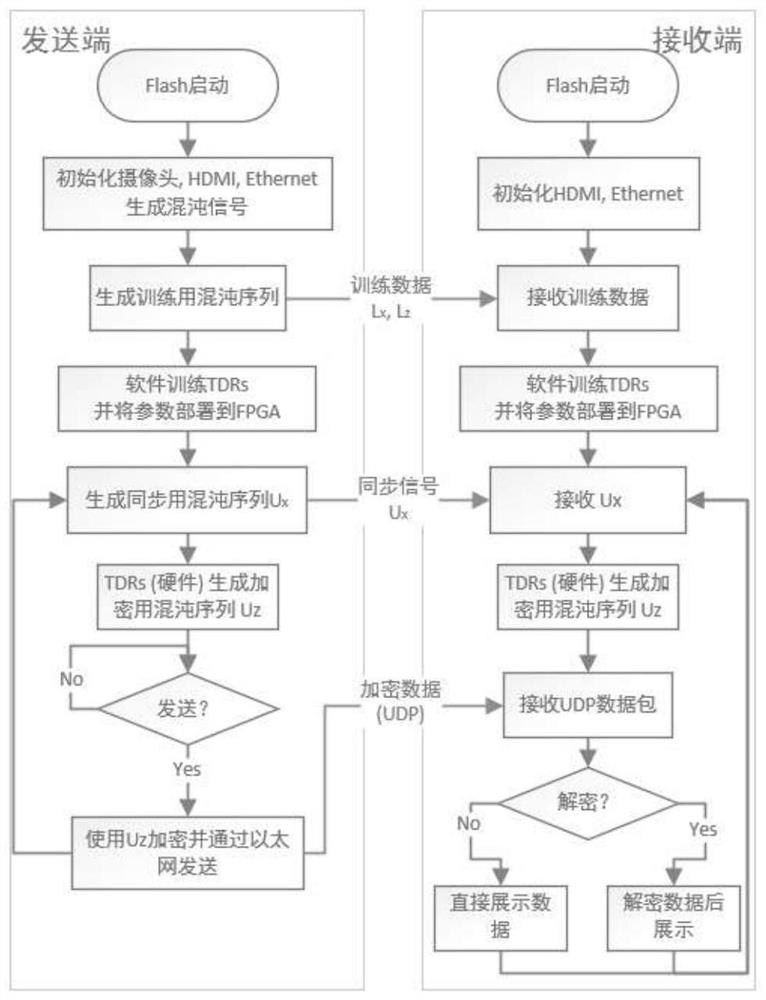
[0052] image 3 It is a flowchart of a secure communication method based on dual-terminal deployment and multi-layer delay reserve pool calculation according to an embodiment of the present invention. see figure 1 and image 3 , the secure communication method includes the following steps:
[0053] S1, use the chaotic system at the sending end to generate a multidimensional chaotic sequence, generate a training set L(t) containing three dimensions Lx(t), Ly(t) a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com