Scheduling method and system for multiple encryption cards and medium
A scheduling method and encryption card technology, applied in the field of systems and media, multi-encryption card scheduling method, can solve the problems of frequent concurrent processing, transient function abnormality of encryption card, amplifying performance loss of encryption card, etc., so as to improve encryption and decryption performance and Effectiveness of data throughput, enhanced system robustness and data security, improved overall performance and system stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
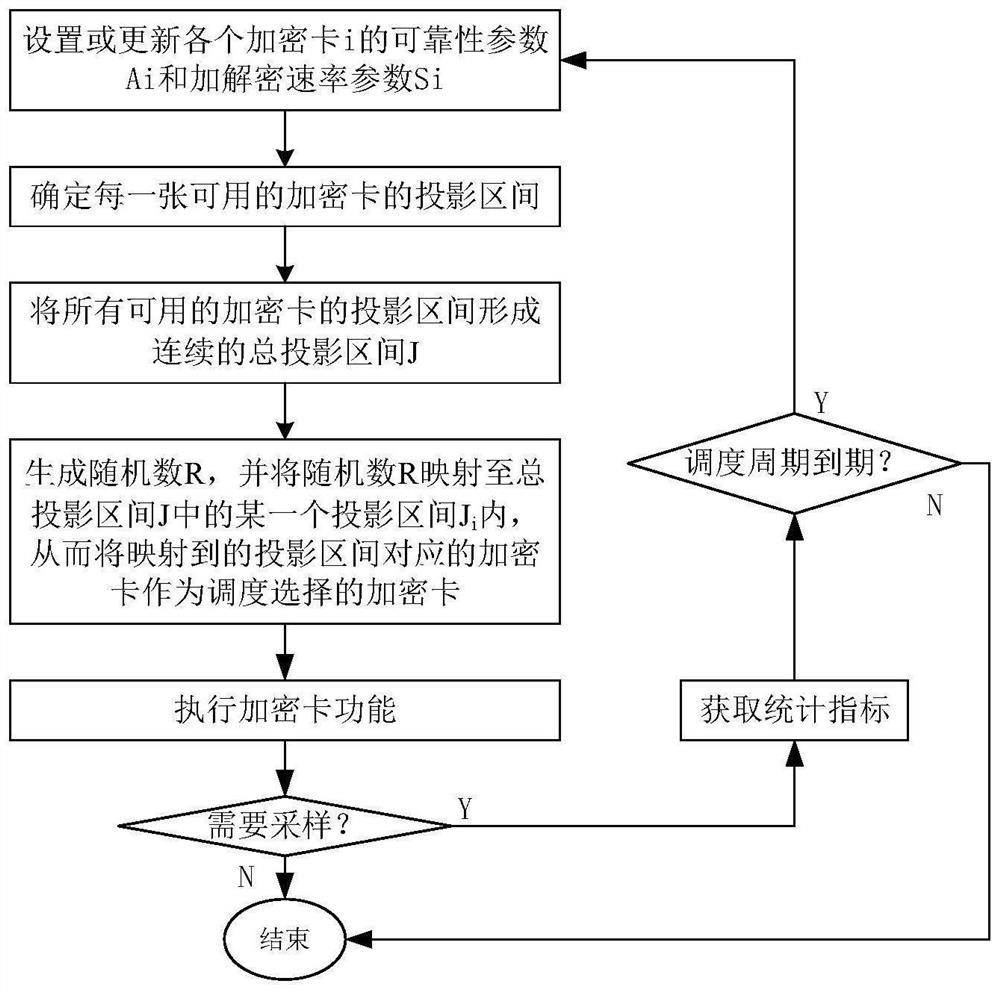
[0034] Such as figure 1 As shown, the scheduling method of multiple encryption cards in this embodiment includes the steps of scheduling multiple available encryption cards and selecting an encryption card when an encryption and decryption request is received:
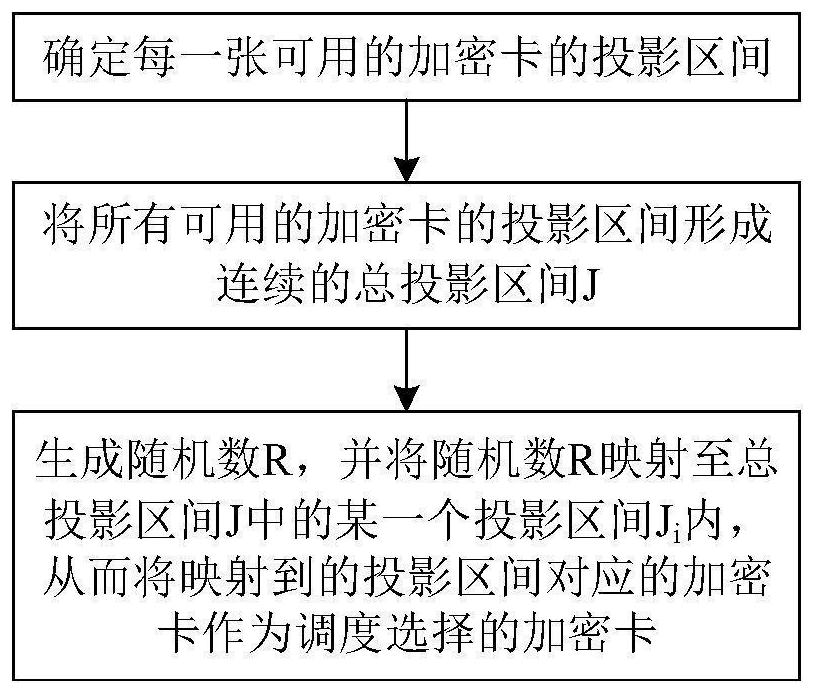
[0035] 1) Determine the projection interval of each available encryption card;
[0036] 2) Form the projection intervals of all available encryption cards into a continuous total projection interval J;
[0037] 3) Generate a random number R, and map the random number R to a certain projection interval J in the total projection interval J i , so that the encryption card corresponding to the projection interval mapped to is taken as the encryption card selected by scheduling.
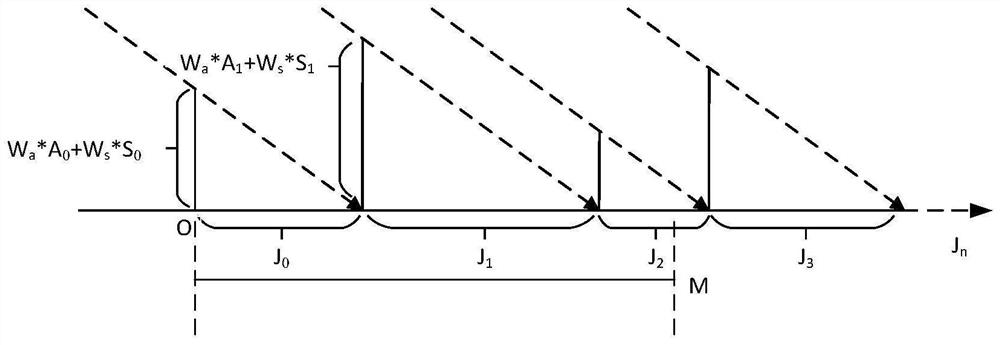
[0038] In this embodiment, the calculation function expression of the projection interval of each available encryption card is:
[0039] J i =W a *A i +W s *S i
[0040] In the above formula, W a and W sRespectively weight parameters (c...
Embodiment 2
[0050] This embodiment is basically the same as Embodiment 1, and its main differences are as follows: image 3 As shown, on the basis of Embodiment 1, this embodiment adds the reliability parameter A of each encryption card i to be automatically updated based on the set period i and based on the set period to automatically update the encryption and decryption rate parameter S of each encryption card i i A step of. The reliability parameter A is recalculated every cycle according to the statistical increment i And the encryption and decryption rate parameter S i , the statistical feedback with smaller granularity can reflect the operation status of encryption cards in real time, and then automatically adjust and optimize the scheduling of encryption cards, which can maximize the reliability of system encryption and decryption, and make full use of the processing of multi-encryption card deployment performance. It should be noted that the reliability parameter A of each enc...
Embodiment 3
[0085] This embodiment is basically the same as Embodiment 2, and its main difference is: when collecting the statistical indicators of each encryption card i in the current period in this embodiment, it also includes first performing a feedback check on the operation error of the encryption card that is in error. If the error is not eliminated, mark the encryption card with the error as unusable. Through the above method, the feedback check for the error in the operation of the encryption card is added, which not only avoids the repeated scheduling of the faulty encryption card, but also prevents If the failure occurs, the encryption card is removed, which further ensures the reliability and processing performance of the system.
[0086] In addition, this embodiment also provides a scheduling system for multiple encryption cards, including computer equipment with multiple encryption cards, the computer equipment includes interconnected microprocessors and memory, and the micro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com