UEFI firmware vulnerability static detection method and device based on taint analysis
A taint analysis and vulnerability technology, applied in computer security devices, instruments, computing, etc., can solve the problems of inability to obtain vulnerability information, isomerization, semantic information recovery technology cannot directly apply UEFI firmware vulnerability detection and analysis, etc., to achieve scalability sex high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] In order to make the above-mentioned features and advantages of the present invention more comprehensible, the following specific embodiments are described in detail in conjunction with the accompanying drawings.
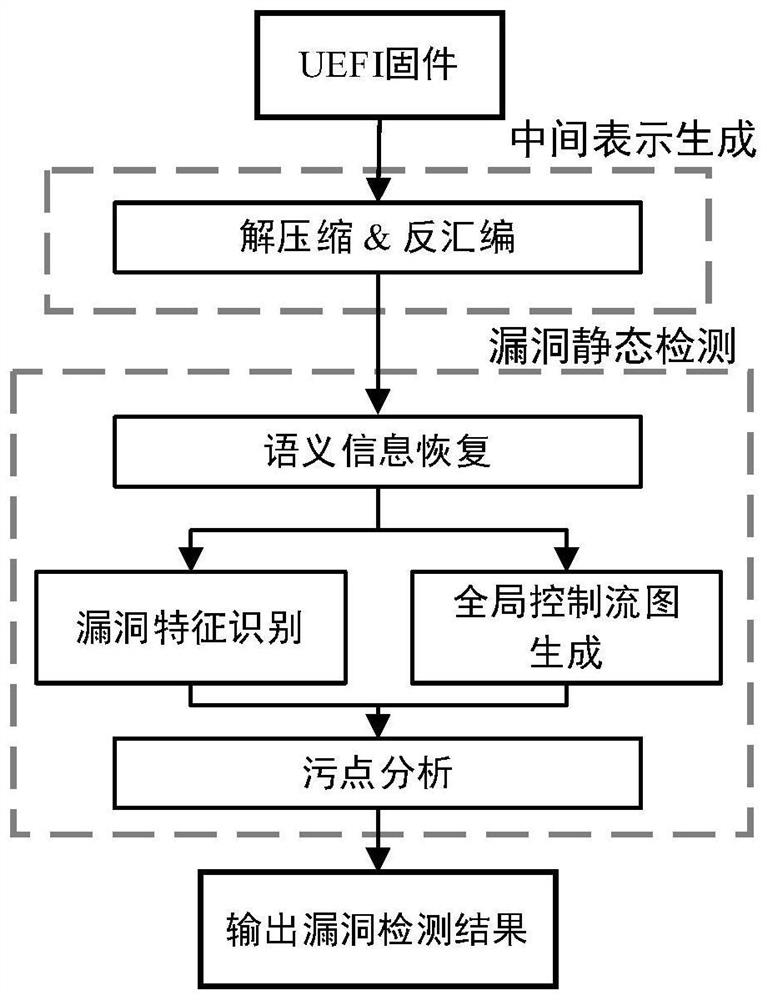
[0050] The embodiment of the present invention discloses a UEFI firmware vulnerability detection method and device based on taint analysis. By accurately restoring the semantic information and cross-process and cross-function data flow in UEFI firmware, the static taint analysis for UEFI firmware is realized, and according to the mark Vulnerability code feature information, to achieve accurate and efficient vulnerability detection in large-scale UEFI firmware scenarios. This method is divided into two stages: intermediate representation generation and vulnerability static detection, such as figure 1 shown. Among them, the intermediate representation generation stage is mainly to complete the preprocessing work such as extraction and disassembly of UEFI firmw...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com