Data burying point configuration method, storage medium and equipment
A configuration method and data technology, applied in the direction of hardware monitoring, etc., can solve problems such as differences in custom field formats, incomplete records, and incomplete implementation of buried point development technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention clearer, the technical solutions in the embodiments of the present invention will be clearly and completely described below in conjunction with the drawings in the embodiments of the present invention. Obviously, the described embodiments It is a part of embodiments of the present invention, but not all embodiments.
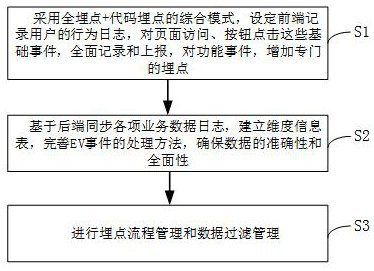
[0064] Such as figure 1 As shown, the method for configuring data buried points described in this embodiment uses a computer device to perform the following steps,
[0065] S1. Adopt the comprehensive mode of full burying + code burying, set the front end to record user behavior logs, comprehensively record and report basic events such as page access, and add special burying events for some functional events.
[0066] First configure the code burying point, that is, write the reporting logic directly into the business code. Code burying points are...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com