Network security detection method and device
A technology of network security and detection method, applied in the field of network security, can solve the problem of no reallocation, etc., and achieve the effect of improving the utilization rate of the website
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
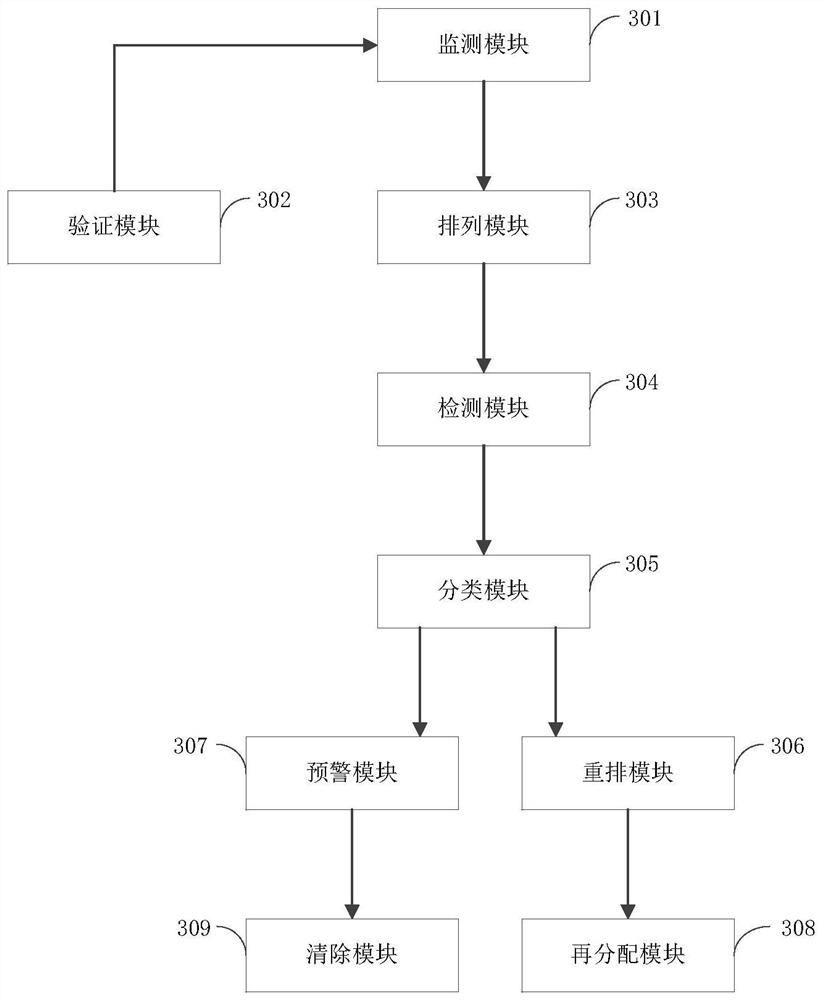
[0052] see Figure 1 to Figure 3 , the present invention provides a technical solution:
[0053] figure 1 It is a simple step of the network security detection method in the embodiment of the present invention, and the subject of execution of this process may be any device that can be used for network security detection, such as a server and a terminal. Terminals can be personal computers, mobile phones, and tablet computers, etc.; servers can be personal computers and computer clusters, etc. Here, the execution subject may be a network security detection device.
[0054] The steps of a network security detection method are as follows:
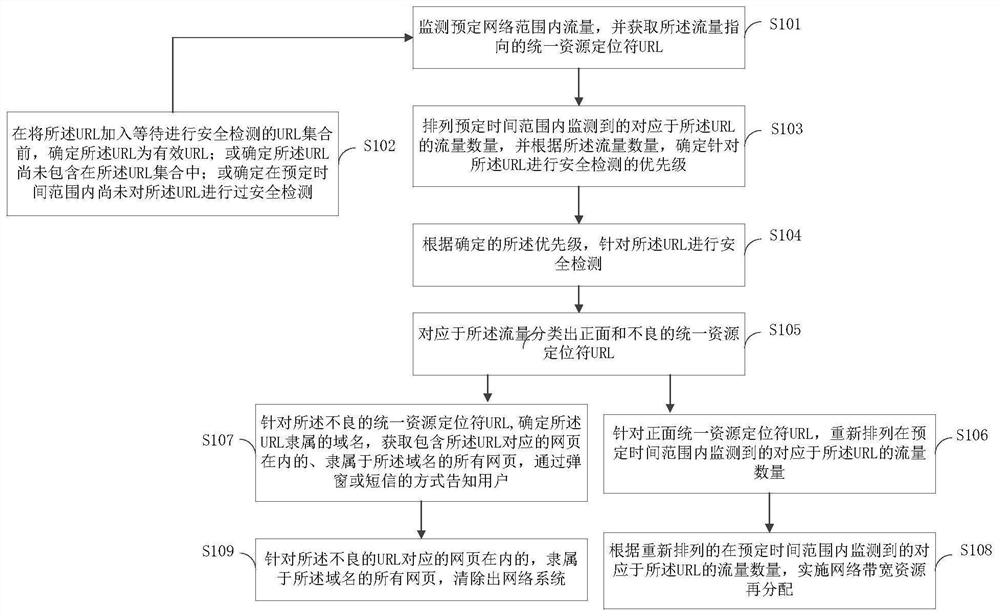
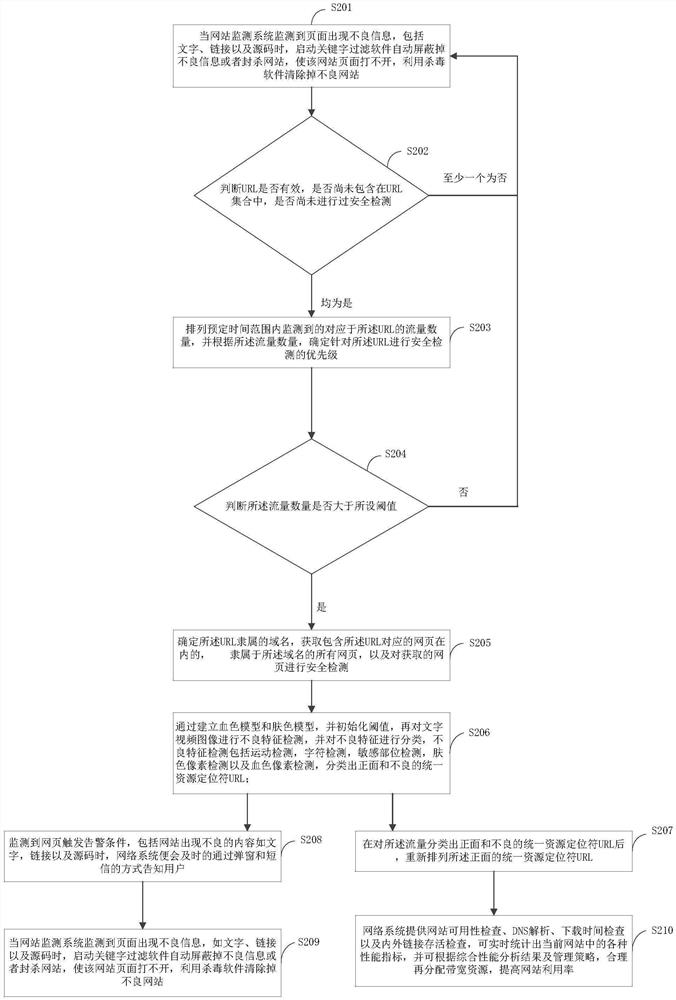
[0055] S101. Monitor traffic within a predetermined network range, and obtain the Uniform Resource Locator URL pointed to by the traffic;
[0056] The predetermined network range refers to part or all of the wide area network or local area network. There may be one or more websites within the predetermined network range. Each website may h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com