Method for efficiently and non-inductively establishing security baseline of terminal file system
A file system and security baseline technology, applied in the field of information security, can solve problems such as high resource occupation, low baseline establishment efficiency, uncontrollable learning process, etc., and achieve the effect of reducing impact, shortening content length and computing time, and excellent experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
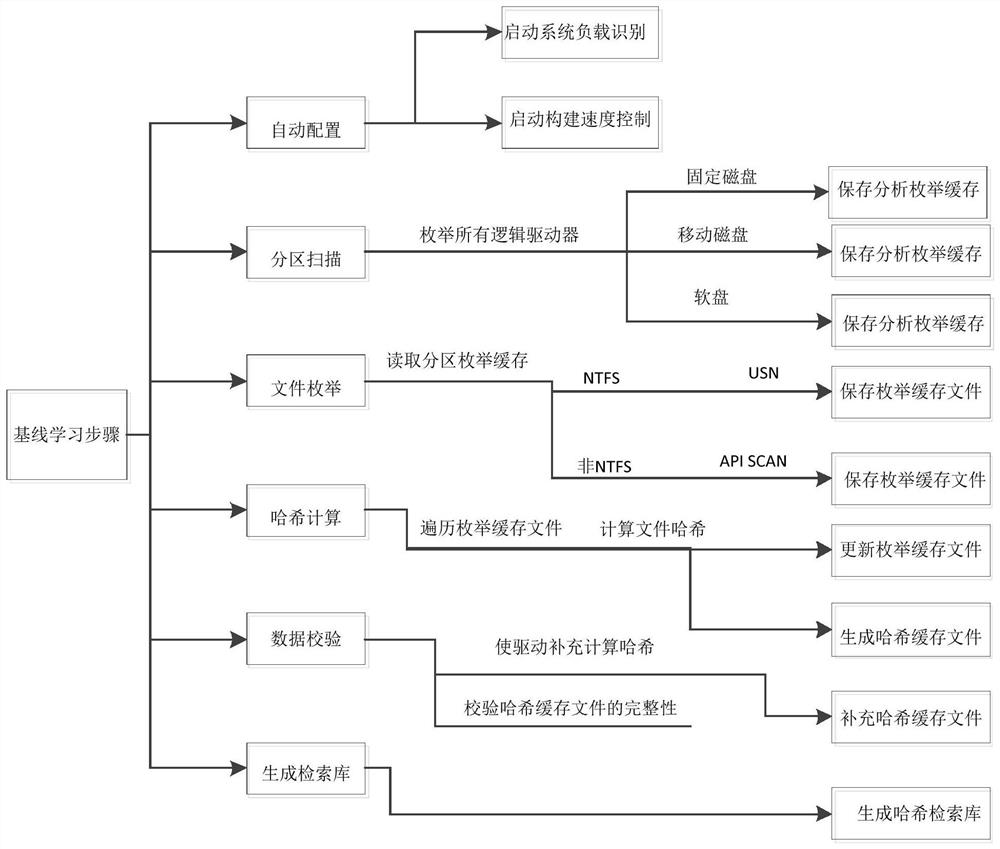
[0028] This embodiment discloses an efficient and non-inductive method for establishing a security baseline of a terminal file system. The method is as follows:
[0029] Through the USN log of the NTFS file system, the file traversal of the volume device is realized;
[0030] The CRC64 algorithm is used to replace the traditional MD5 digest algorithm to calculate the file hash value. The calculation content of the file hash value is calculated using the file four-element group, and the calculation process is no longer affected by the file size;
[0031] After the calculation is completed, the file is traversed and learned, and the learning process is designed in layers. Each step of the learning process has a corresponding caching mechanism and is marked to support learning from any progress position of any step after the learning process is interrupted;
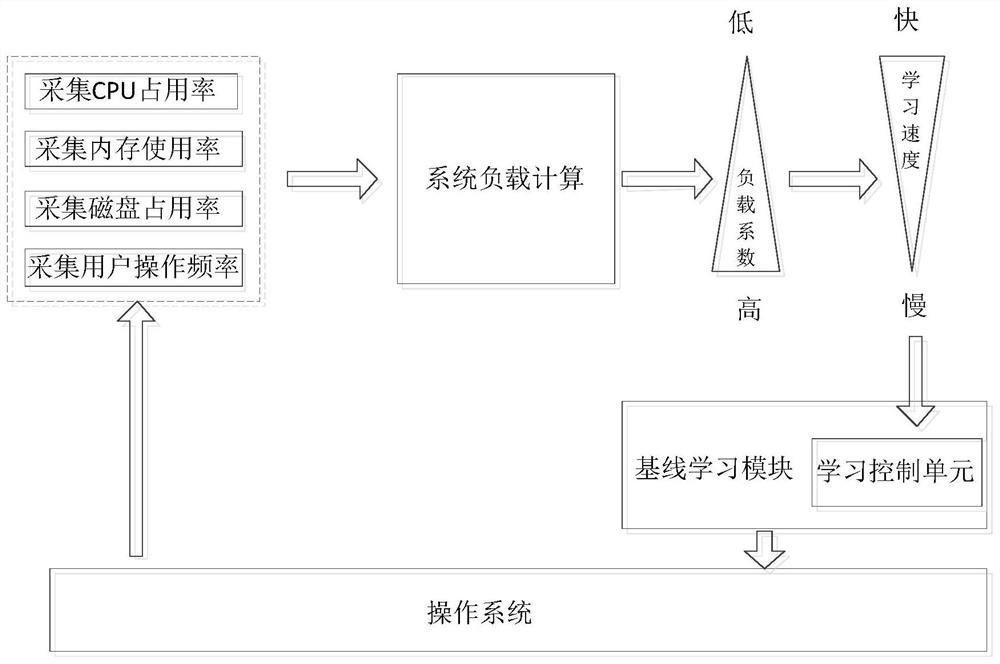
[0032] Carry out multi-dimensional identification for system resources, dynamically adjust the rhythm of the learning proc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com