Hierarchical aggregation management system for multi-source heterogeneous security data
A security data, multi-source heterogeneous technology, applied in the field of data management, can solve the problems of high false positive rate and false negative rate of intrusion detection system, it is difficult to understand the security threat status of the system, and it is impossible to take response measures in time. Concealment and confidentiality ability, avoid manual extraction, avoid the effect of leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
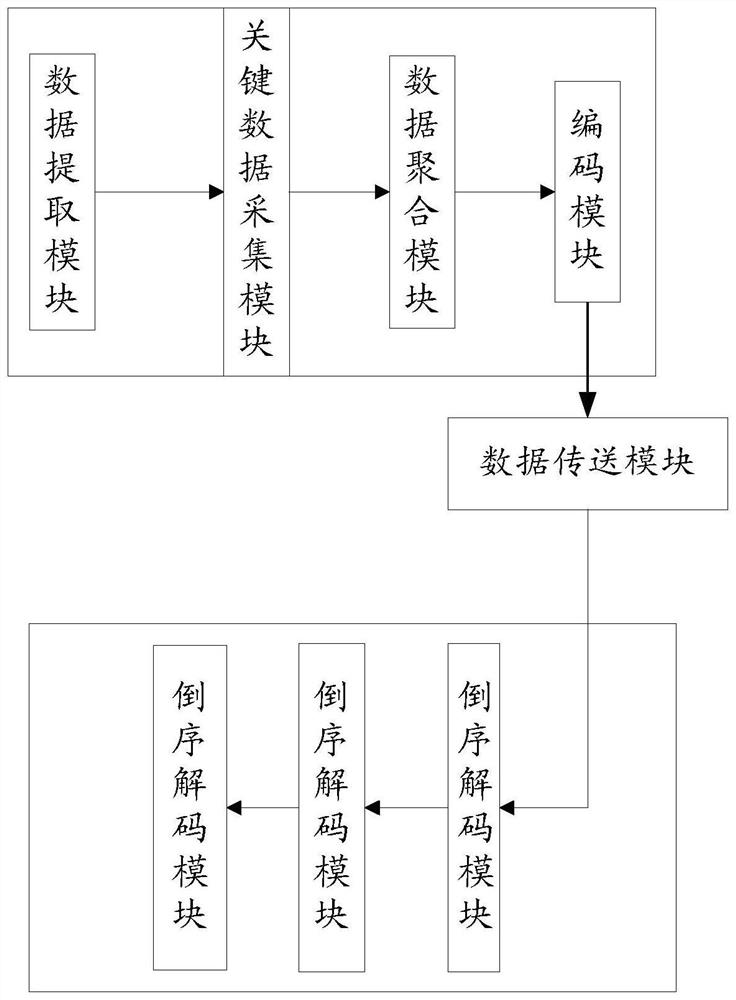
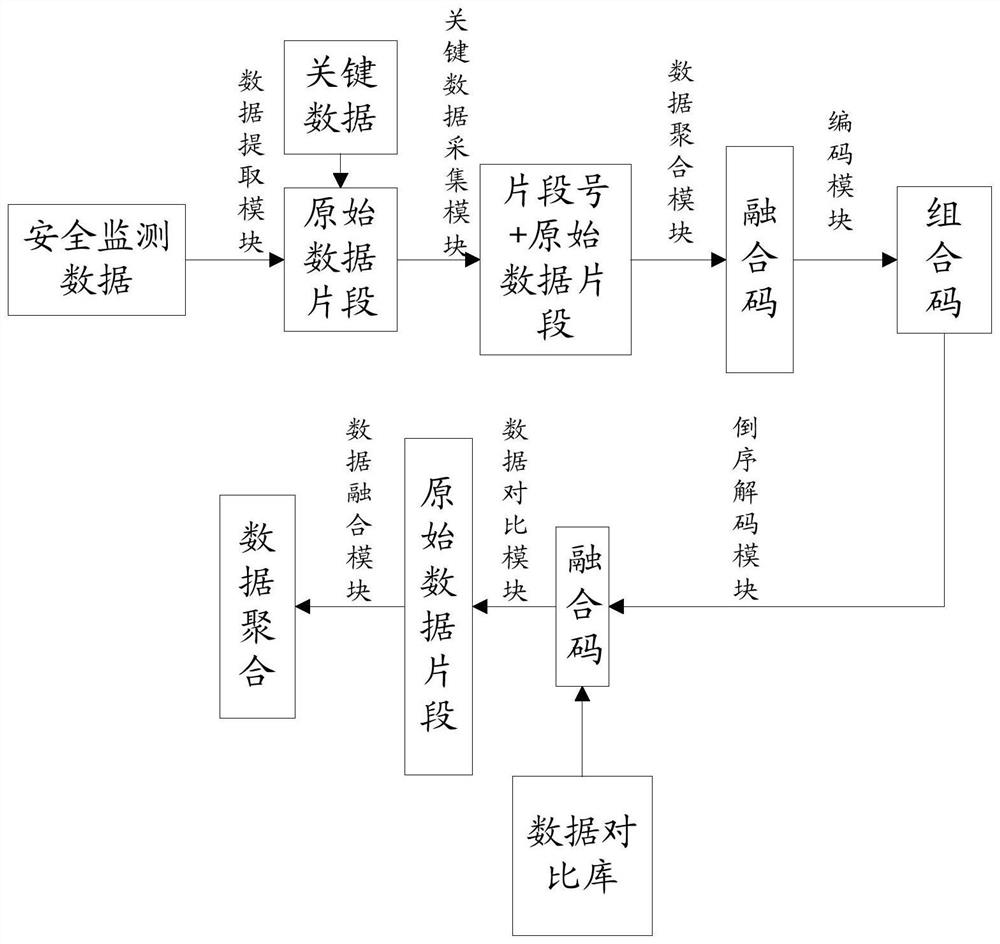
[0027] refer to figure 1 , figure 2 In this embodiment, a multi-source heterogeneous security data hierarchical aggregation management system is proposed, including: data extraction module, key data acquisition module, data aggregation module, encoding module, data transmission module, reverse decoding module, data comparison module and data fusion module.
[0028] The data extraction module is used for extracting original data fragments using safety monitoring data as a data source. The safety monitoring data refers to: safety alarm log data, network log data and system log data.
[0029] The key data acquisition module is used to identify the original data fragments, compare them according to the pre-input key data, and mark the original data fragments containing key data; for example, for the pre-input key data, each original The data fragments are compared and scanned, and when the key data appears in one of the original data fragments, the original data fragment is ma...
Embodiment 2
[0040] The multi-source heterogeneous security data hierarchical aggregation management system may also include a standardization module, through which the original data fragments are standardized and marked with data source features, so that the data extraction module can extract key data from the original data fragments The collection module performs collection, such as extracting data source feature codes, and aggregating feature codes with original data fragments, so as to facilitate later classification. When raw data is input into the system, the data extraction module can be divided according to the input scene, area, time, input method, input account number, etc., so as to distinguish and obtain multiple raw data fragments from different sources. For example, if the input scenario is input through a security topic, the feature code is security.
[0041] The original data comes from the Internet of Things; the Internet of Things is the application of the Internet of Thi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com