Model expansion method and device and readable storage medium
An extension method and model technology, applied in the computer field, can solve problems such as system security risks and consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
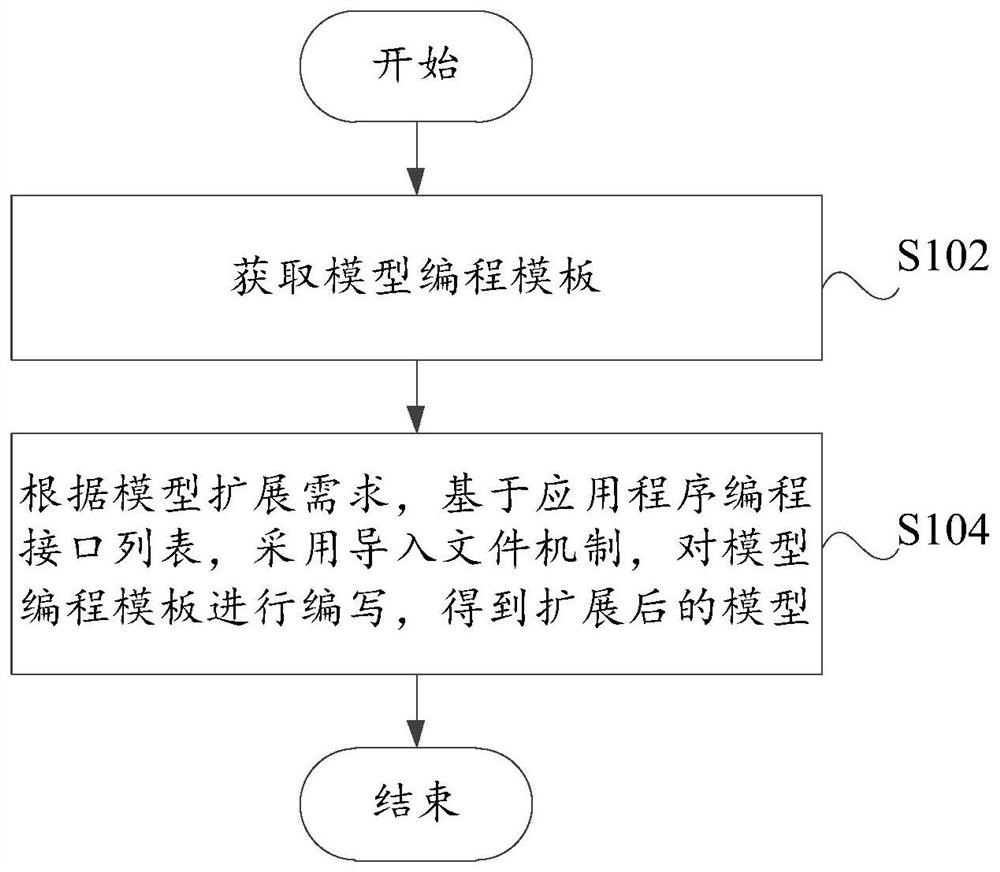
[0043] Such as figure 1 As shown, this embodiment provides a model extension method, including the following steps:
[0044] Step S102, obtaining a model programming template;
[0045] Step S104, according to the model extension requirements, based on the application programming interface list, using the import file mechanism to write the model programming template to obtain the extended model.
[0046] In this embodiment, the model programming template is written using the Groovy programming language. Based on the user's needs, multiple model programming templates can be set. The user selects the required model programming template according to the actual situation, and writes on the model programming template, which improves the The availability of programming, users do not need to master Java, Groovy Script and other programming languages.
[0047] In this embodiment, the groovy programming language can be used to provide an application programming interface list (that is...
Embodiment 2
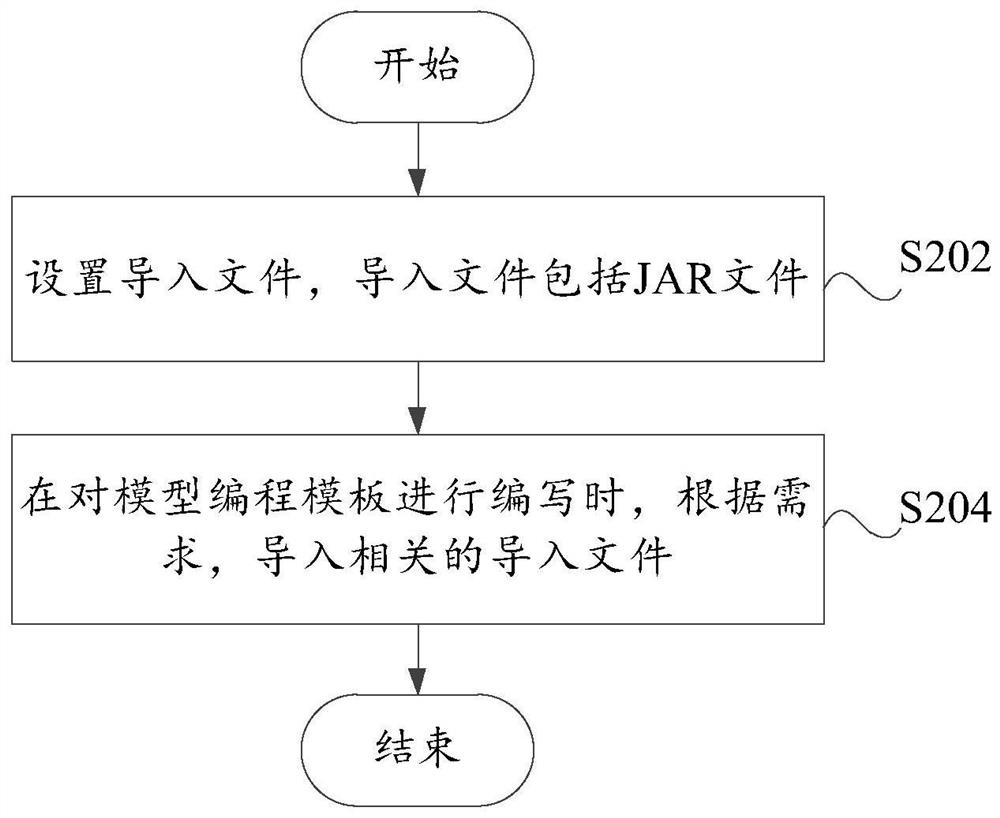
[0050] Such as figure 2 As shown, this embodiment provides a model extension method. In addition to the technical features of the above embodiments, this embodiment further includes the following technical features:
[0051] Adopting the import file mechanism involves the following steps:
[0052] Step S202, setting an import file, the import file includes a JAR file;
[0053] Step S204, when writing the model programming template, import related import files according to requirements.
[0054]In this embodiment, according to requirements, the import file can be preset. The import file can be a JAR file (i.e. JAR package, Java Archive File). This embodiment adopts the import file mechanism (i.e. the import package mechanism). When the user uses it, only The JAR file provided by the system can be used, which can remove system security implications while being convenient to use, ensure system security, and reduce system risk.
Embodiment 3
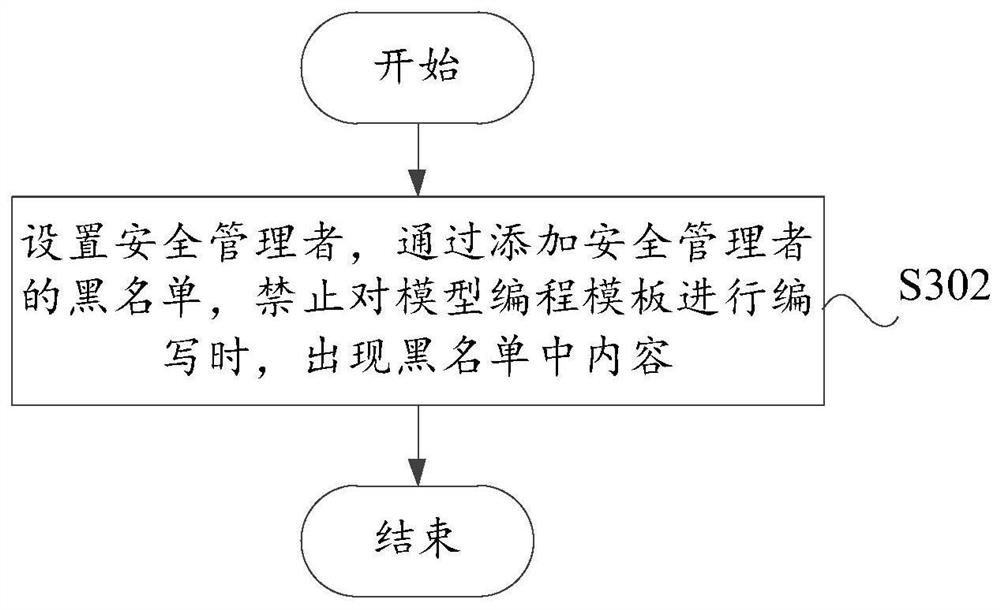
[0056] Such as image 3 As shown, this embodiment provides a model extension method. In addition to the technical features of the above embodiments, this embodiment further includes the following technical features:
[0057] The model extension method also includes the following steps:
[0058] Step S302, setting a security manager, by adding the blacklist of the security manager, prohibiting the programming template of the model from appearing in the blacklist.
[0059] This embodiment is based on the groovy programming language, and the SecureASTCustomizer security manager provided inside Groovy can be used to prohibit adding content in the blacklist when writing the model programming template. When the user is in use, this embodiment can prevent the user from using the content in the blacklist to program, effectively remove system security implications, ensure system security, and reduce system risks.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com