Source tracing method of same source code
A technology of source code and open source code, applied in the direction of instrument, program/content distribution protection, platform integrity maintenance, etc., can solve problems such as long retrieval time and inability to solve project inclusion relationship, so as to improve detection speed and accurately open source projects Accurate effect with version and vulnerability detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
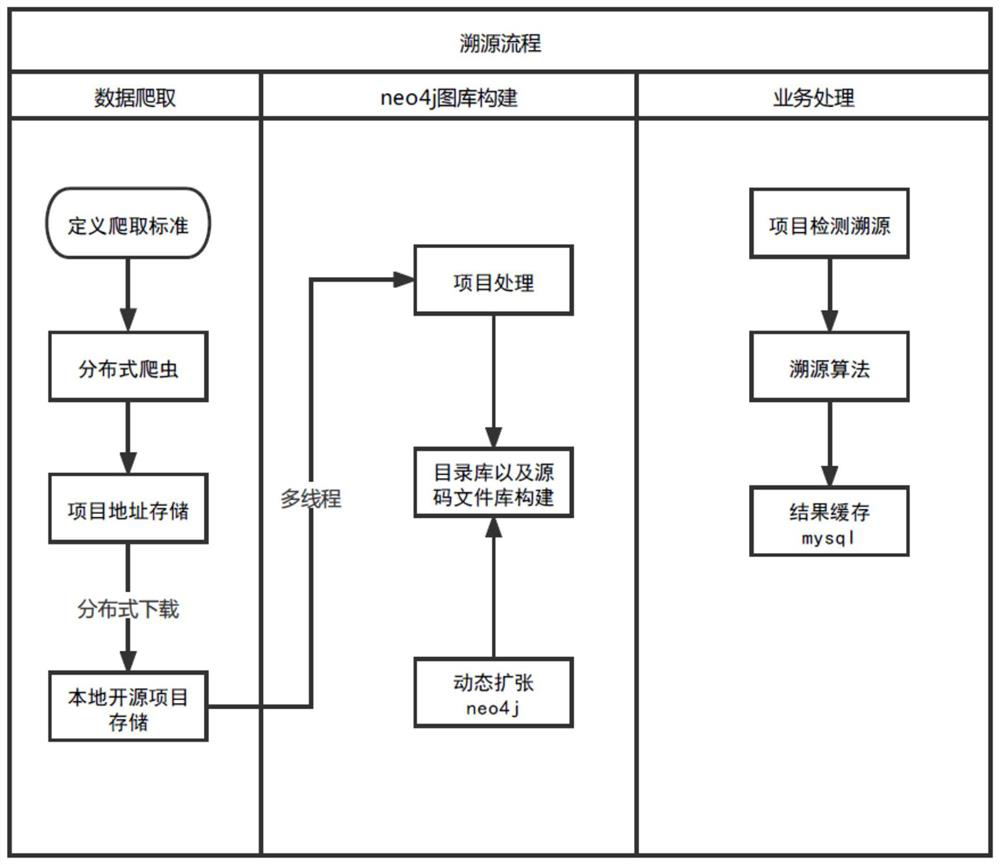
[0035] Such as figure 1 The traceability method of homologous code, is characterized in that comprising the following steps:
[0036] Step 1: Establish a standardized vulnerability knowledge base through crawlers, obtain open source codes that meet the specifications, and store the open source code results after preprocessing. Specifically, the process employed includes the following steps:
[0037] a. Crawl open source codes that meet specifications in source code hosting platforms and communities through web crawlers. The source code hosting platforms and communities include github, gitee, and linux, and the specifications include determining star ratings and branch nu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com