User behavior recognition method, system and device and storage medium
A recognition method and behavior technology, applied in transmission systems, neural learning methods, biological neural network models, etc., can solve the problems that data stream encryption technology increases the difficulty of user behavior analysis, cannot directly obtain user behavior information, etc., and achieves rich supervision methods. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The embodiment of the present invention will be explained in detail below in conjunction with the accompanying drawings. The examples given are only for the purpose of illustration, and cannot be interpreted as limiting the present invention. The accompanying drawings are only for reference and description, and do not constitute the scope of patent protection of the present invention. limitations, since many changes may be made in the invention without departing from the spirit and scope of the invention.
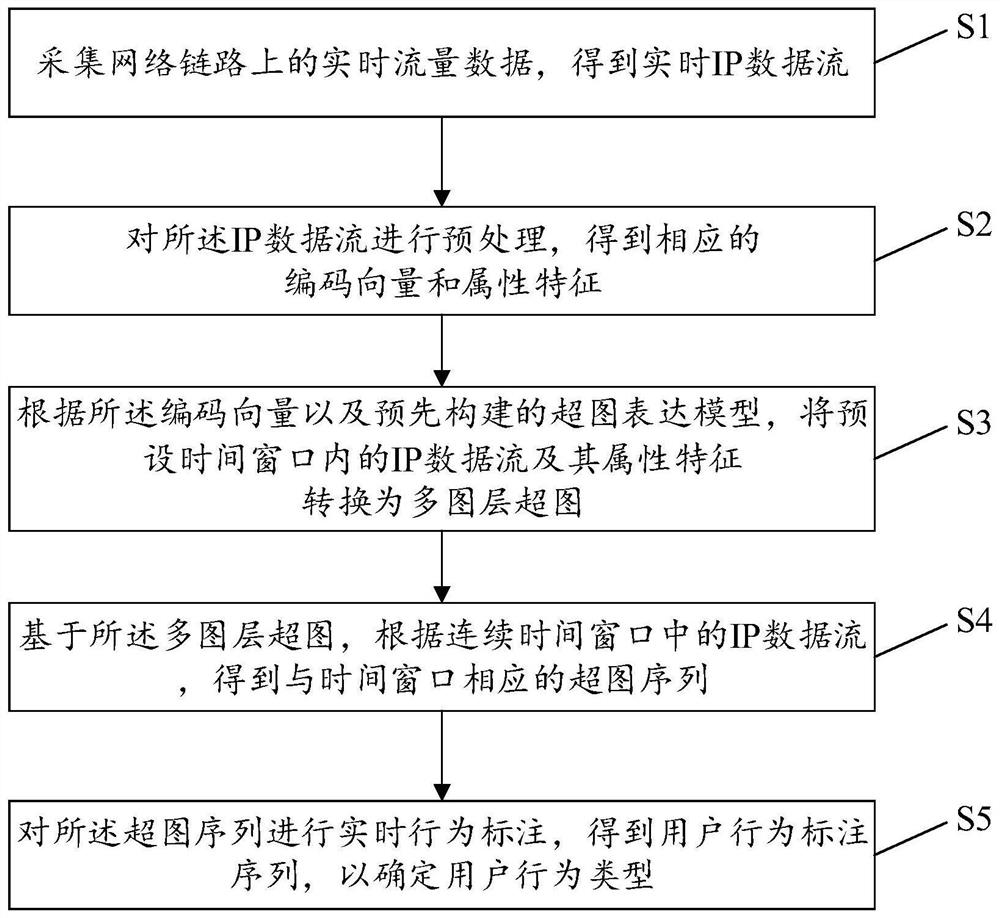
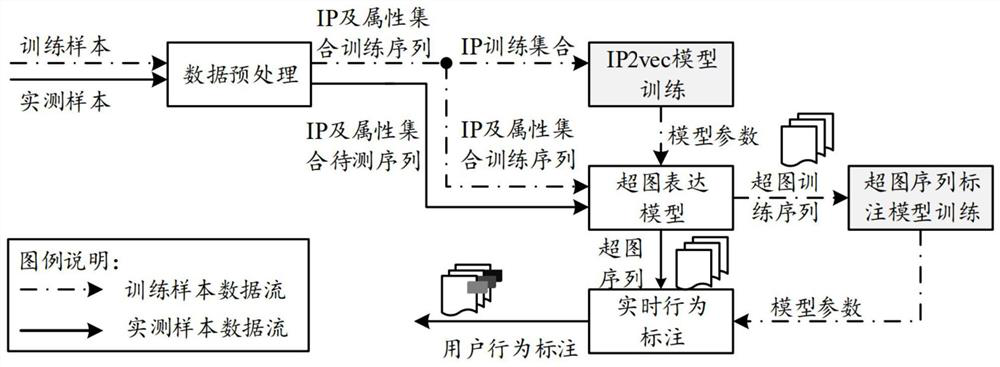
[0057] see figure 1 , figure 1 It is a user behavior identification method provided by an embodiment of the present invention, which can be applied to various types of network link-level management. The method includes:
[0058] S1. Collect real-time flow data on the network link to obtain real-time IP data flow;
[0059] In one embodiment, this embodiment collects network data flow in real time through a capture tool on a designated network link to obtain real-tim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com