Mirror image file transmission method and device, equipment and storage medium
A technology of image files and transmission methods, applied in the field of information security, can solve the problems of content leakage and tampering, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
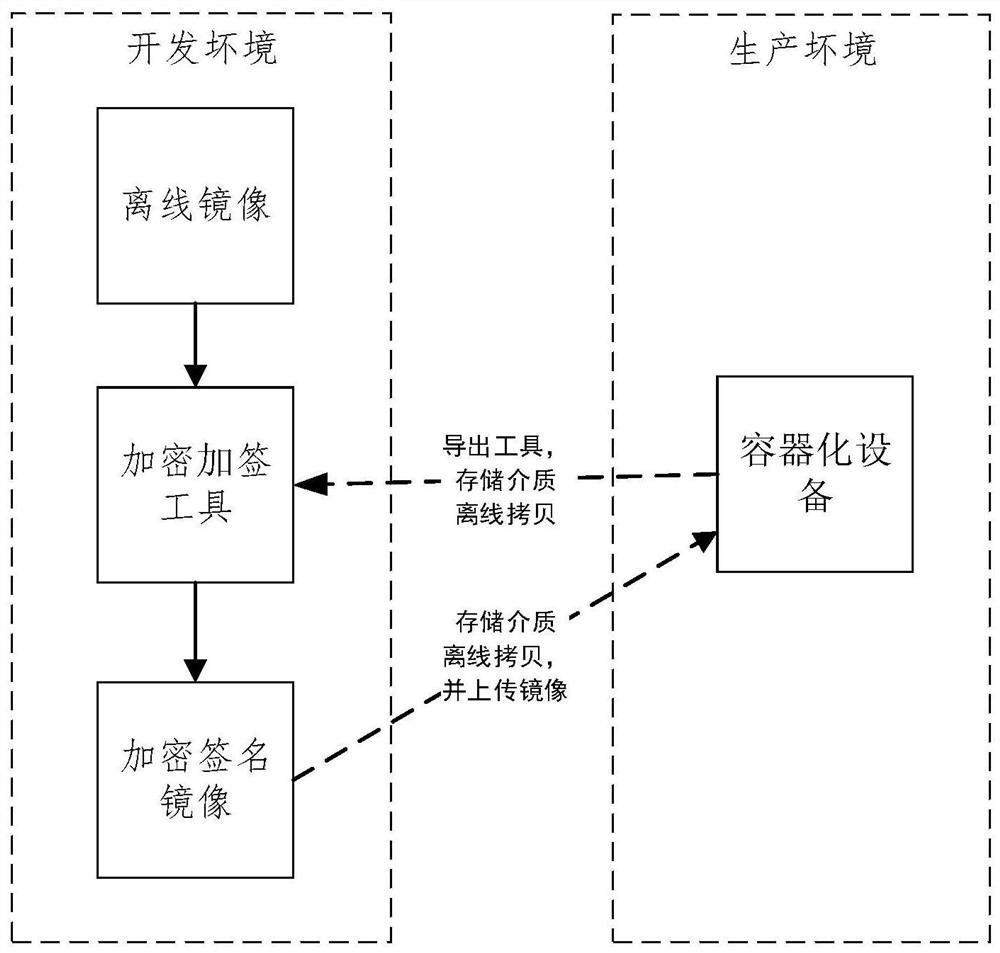
[0042] In the prior art, in some private cloud or local area network application scenarios, development and actual operation are often not in the same reachable network. The image is often sent offline to the customer through a storage medium such as a CD, and then the customer reads the offline image from the medium. Compared with traditional Internet scenarios, new risks are often introduced, that is, the content may be leaked or tampered with during the transmission process of the image. In order to overcome the above-mentioned technical problems, the present application proposes a mirror image file transmission method, which can improve the security of mirror image offline transmission.
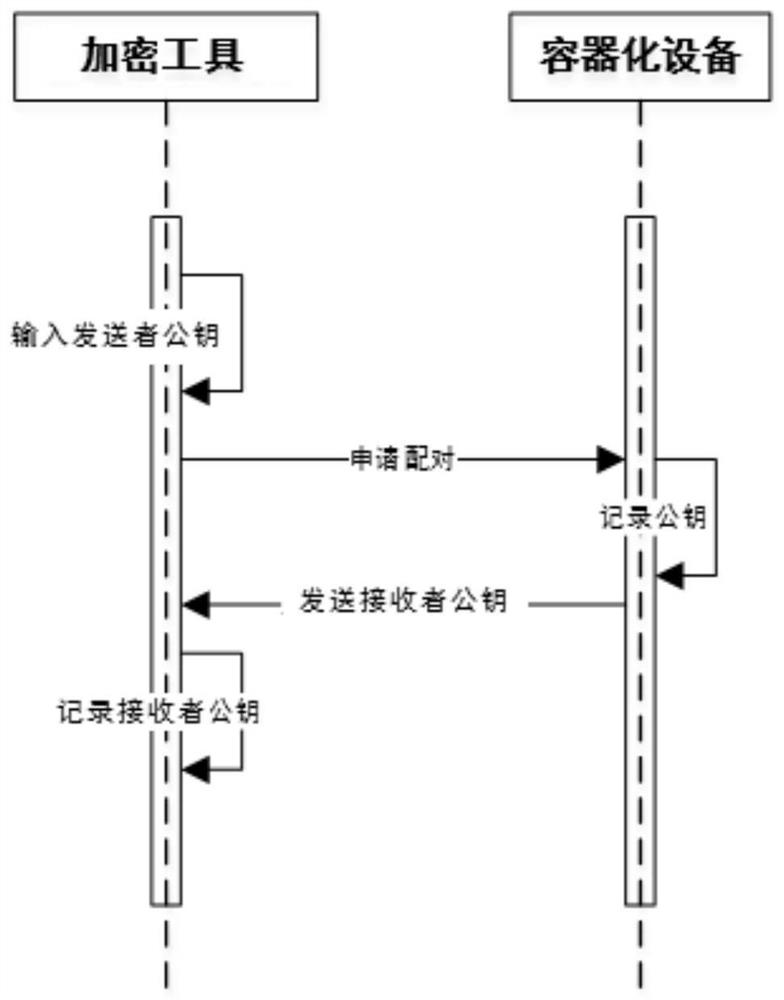
[0043] The embodiment of the present application discloses a mirror image file transmission method, see figure 1 As shown, the method may include the following steps:
[0044] Step S11: Connect the local encryption tool with the containerized device at the receiving end and perform a pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com