Hardware Trojan horse detection system and information data processing method based on unsupervised learning
A technology of hardware Trojan detection and unsupervised learning, applied in the direction of internal/peripheral computer component protection, etc., can solve the problems of reducing feature dimension, hardware Trojan horse does not contain state information, and it is difficult to completely distinguish Trojan horse networks, etc., to reduce feature dimension number effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
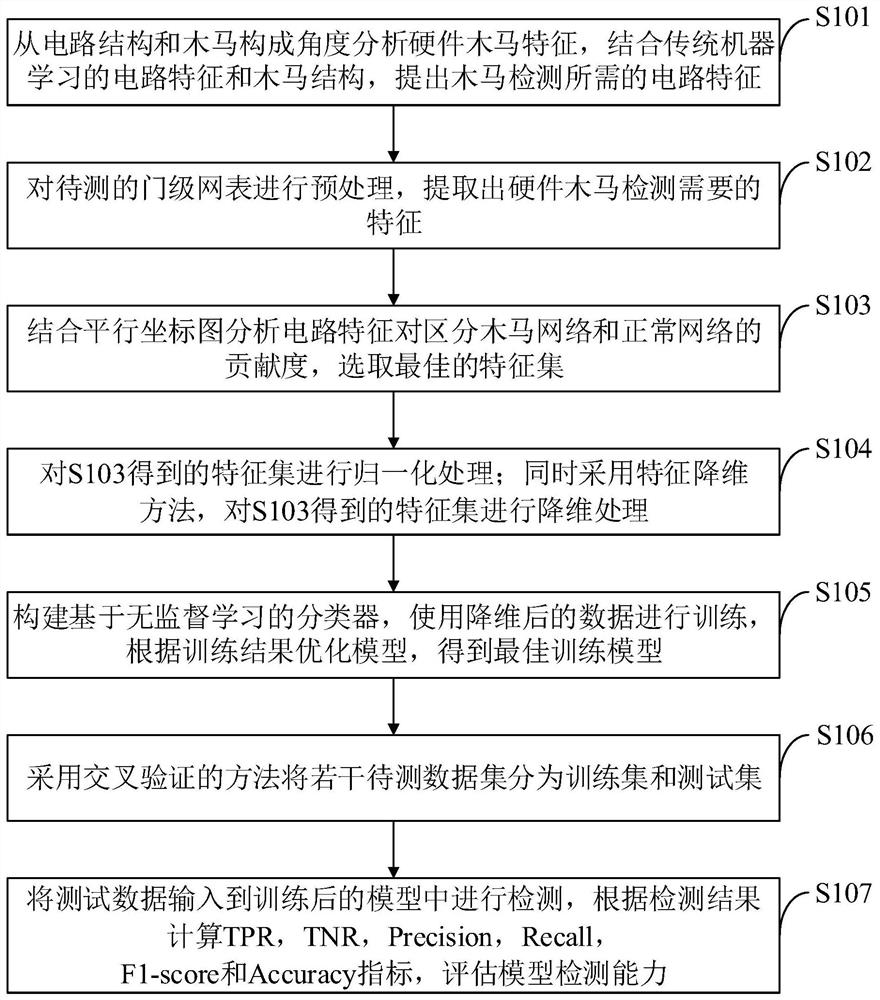
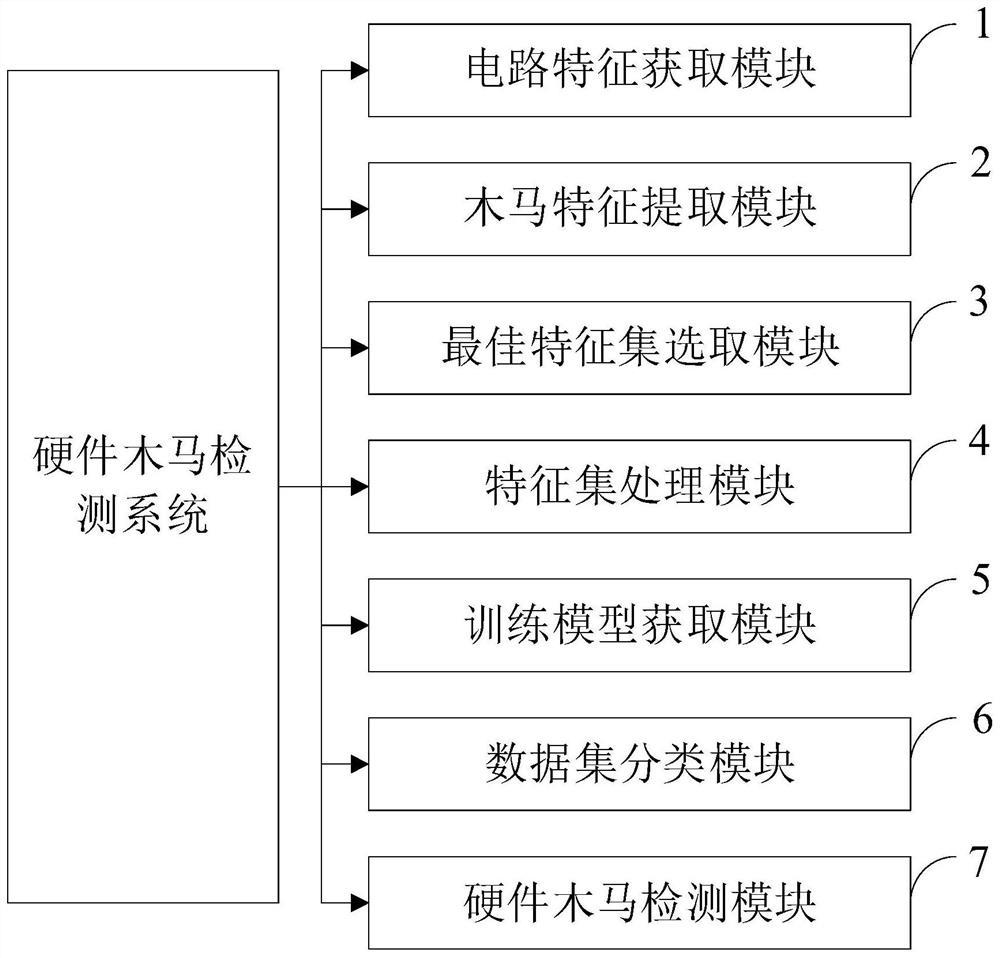
[0124] The hardware Trojan horse detection method based on machine learning provided by the embodiment of the present invention includes: analyzing the circuit structure and Trojan horse operation logic, combining the circuit characteristics of traditional machine learning, proposing the required circuit characteristics, and performing a gate-level netlist analysis of the circuit to be tested. Processing, extracting the features required for hardware Trojan detection, combining random forest, correlation matrix and parallel coordinates diagram to analyze the contribution of circuit features to distinguish normal circuits and Trojan circuits, select the best feature set, and after normalization processing, use The PCA (Principal Component Analysis) method reduces the dimensionality of the data, uses the reduced dimensionality data to train the Isolation Forest (isolation forest) classifier, obtains the best training model, and inputs the test data into the trained model for detec...
Embodiment 2
[0140] The purpose of the present invention is to provide a hardware Trojan detection method based on machine learning in view of the situation in the above background technology, and to solve the problems of high algorithm complexity, long detection time and low For problems such as poor accuracy, PCA (Principal Component Analysis) method is used for dimensionality reduction. While reducing the feature dimension, most of the data information is retained. Use the dimensionality-reduced data to train the Isolation Forest (isolation forest) unsupervised model, and apply training A good best model detects and localizes hardware Trojans.
[0141] To achieve the above object, the present invention adopts the following technical solutions:
[0142] Step S1: Analyze the characteristics of the hardware Trojan horse from the perspective of circuit structure, Trojan horse trigger circuit and load circuit function, combine the circuit features and Trojan horse structure of traditional ma...
Embodiment 3
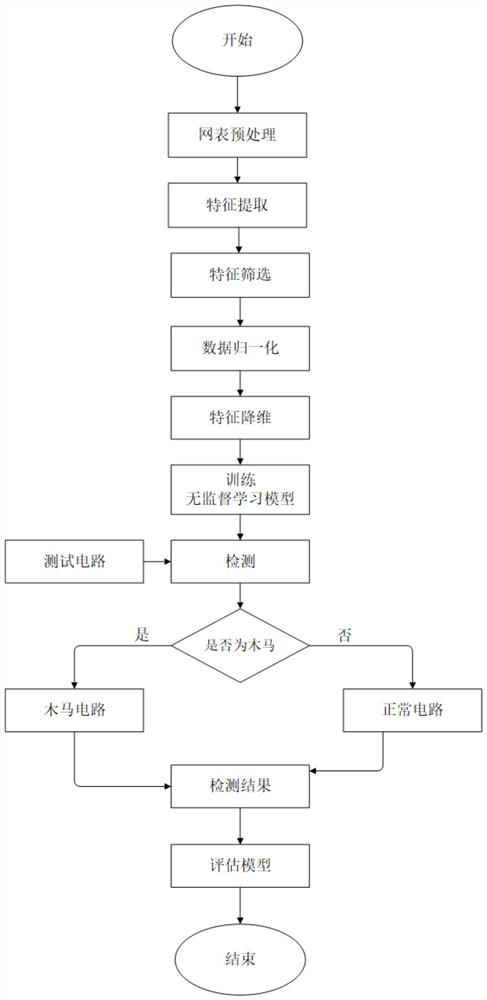
[0166] refer to figure 2 , the hardware Trojan detection system and the information data processing method based on unsupervised learning that the embodiment of the present invention provides, comprise the following steps:
[0167] Step S1: Analyze the characteristics of the hardware Trojan horse from the perspective of circuit structure, Trojan horse trigger circuit and load circuit function, analyze the difference between the Trojan horse circuit and the normal circuit, associate the characteristic of low trigger probability of the Trojan horse circuit with the static feature, and the design can efficiently detect The circuit characteristics of the hardware Trojan horse circuit.
[0168] The characteristics of the selected Trojan horse are: the number of logic gates out_logic_gate_x, in_logic_gate_x (the value of x is 1, 2, 3, 4, 5) away from the input terminal or output terminal of the net by x levels; The fan-in number of logic gates fan_in_x (the value of x is 1, 2, 3, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com