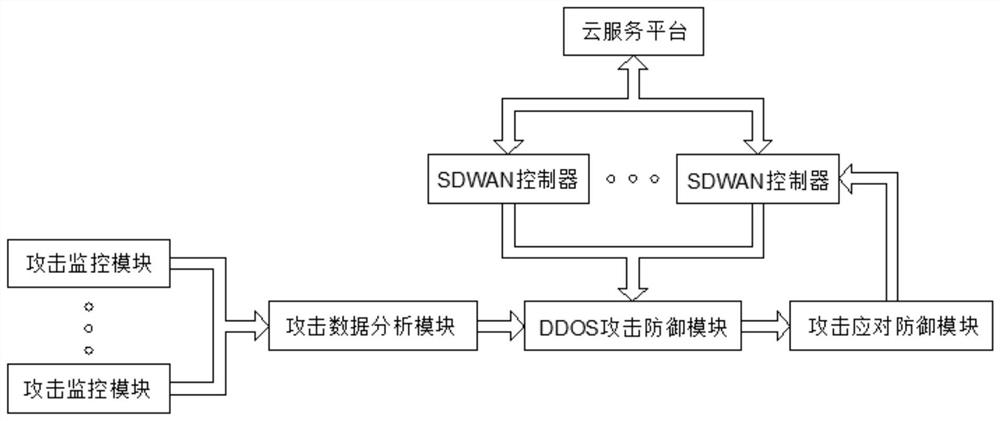
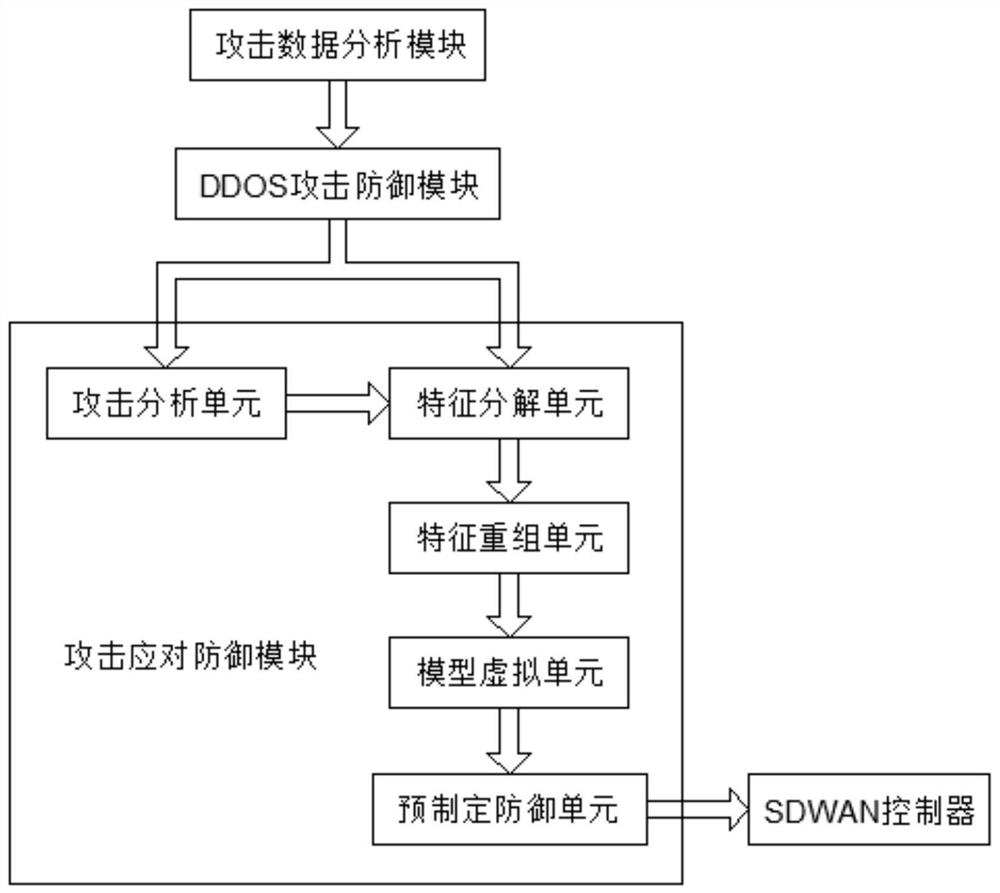
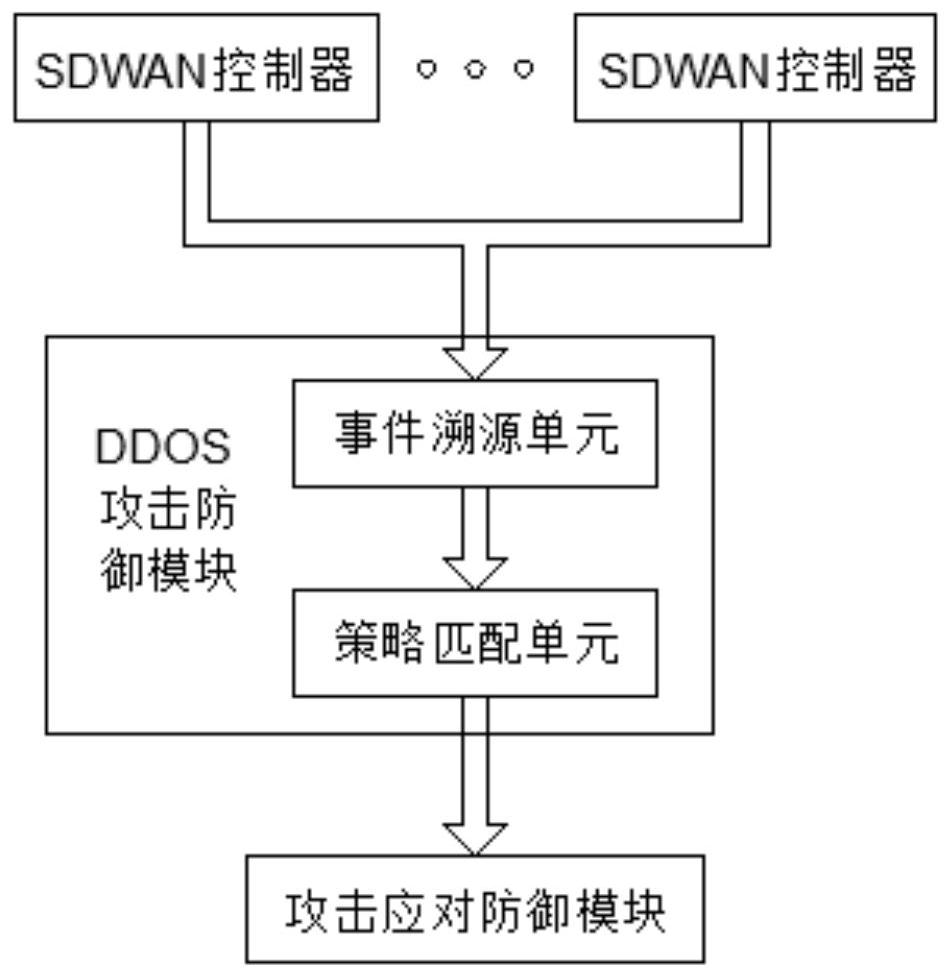
Active defense ddos system based on sdwan
An active defense and DDOS technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve the problems of untimely and time-consuming network defense, achieve high response speed and defense efficiency, and achieve fast and accurate defense effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0016] Example: There are three forms of DDOS attack, specifically SYN / ACKFlood attack, TCP full connection attack, and script brushing attack.
[0017] The SYN / ACKFlood attack is mainly by sending a large number of SYN or ACK packets with forged source IP and source port to the victim host, causing the host's cache resources to be exhausted or busy sending response packets, resulting in denial of service. A large number of SYN / ACKFlood attacks will cause Ping failure, TCP / IP stack failure, and system freezing, that is, not responding to the keyboard and mouse. Most ordinary firewalls cannot resist such attacks.
[0018] The TCP full connection attack is designed to bypass the inspection of conventional firewalls. In general, most conventional firewalls have the ability to filter DOS attacks such as TearDrop and Land. Once there are a large number of TCP connections, even if they are normal, it will cause the website The access is very slow or even inaccessible. The TCP full c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com