Big data analysis-combined digital service vulnerability detection method and server
A vulnerability detection and big data technology, applied in the direction of electrical digital data processing, instruments, character and pattern recognition, etc., can solve the problems of missed detection and false detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
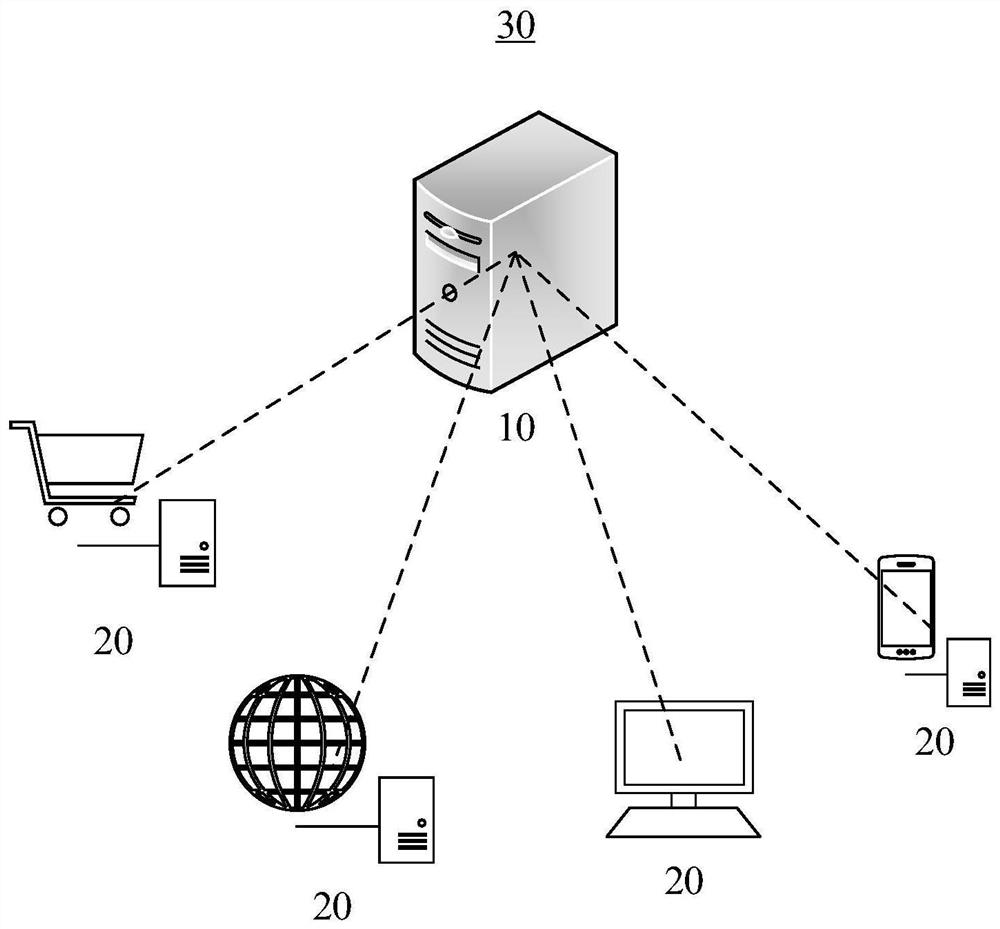
Image
Examples
Embodiment 1
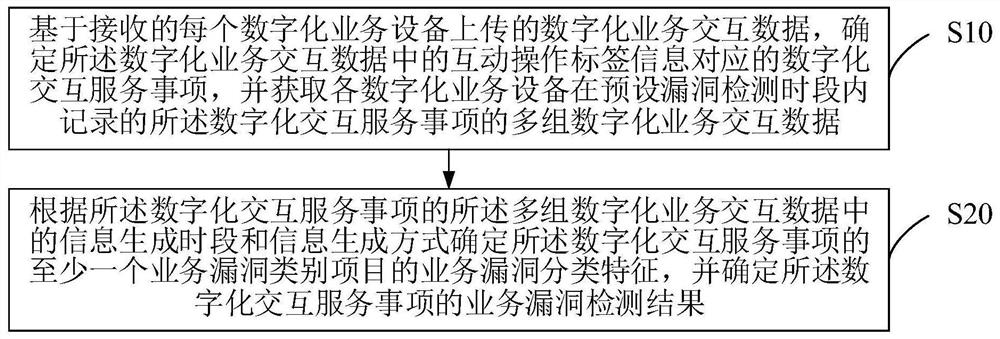
[0083] Embodiment 1, for each digital interactive service item, obtain the digitalized business interaction data of the digitalized interactive service item recorded by each digitalized business device in the second loophole detection period, and determine the digitalized interactive service item according to the acquired digitalized business interaction data In the business interaction error log in the preset offline business interaction scenario, update the first business status of the digital interactive service item according to the business interaction error log of the digital interactive service item in the preset offline business interaction scenario Business vulnerability classification characteristics of category items.
[0084] In Embodiment 1, the second loophole detection period can be adjusted according to the actual situation. For example, the second loophole detection period can be determined according to the received offline service trigger identifier. On this b...
Embodiment 2
[0085] Embodiment 2, for each digital interactive service item, obtain the business assistant detection record of the digital interactive service item in the third loophole detection period, and update the second business status category of the digital interactive service item according to the acquired business assistant detection record The business vulnerability classification feature of the item; wherein, the business vulnerability detection result of the digital interactive service item is based on the business vulnerability classification feature of the at least one business vulnerability category item and the first business status category item and the second business The business vulnerability classification characteristics of at least one of the status category items are jointly determined.
[0086] In Embodiment 2, the third loophole detection period can be determined according to the activation period of the business assistant software, and the business assistant dete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com