A layered file encryption method and system
A file encryption and file technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as user unauthorized access and collaborative attacks, and achieve the effect of solving unauthorized access and collaborative attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
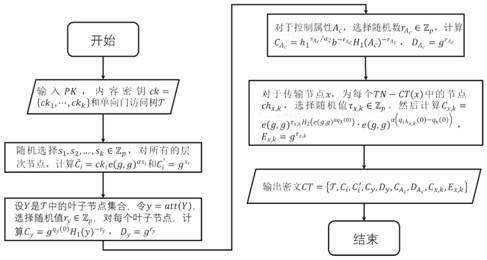
[0066] A layered file encryption method provided by the present invention is applied in such as figure 1 In the encryption system shown. This layered file encryption method includes:
[0067] According to the layered files to be encrypted and the hierarchical relationship of each layered file to be encrypted, a one-way door access tree is constructed; based on the one-way door access tree Treat the encrypted layered file ck through the system public key PK i Encrypt, obtain the encrypted ciphertext and send it to the cloud service provider for storage.
[0068] When all attributes of the data consumer attribute set satisfy part or all of the one-way door access tree, the encrypted ciphertext is decrypted by the system public key and the data consumer private key to obtain the decrypted plaintext, otherwise the decryption fails.
[0069] Wherein, the data consumer attribute set S includes but not limited to the user's occupation, title and affiliation.
[0070] Further, as ...
Embodiment 2
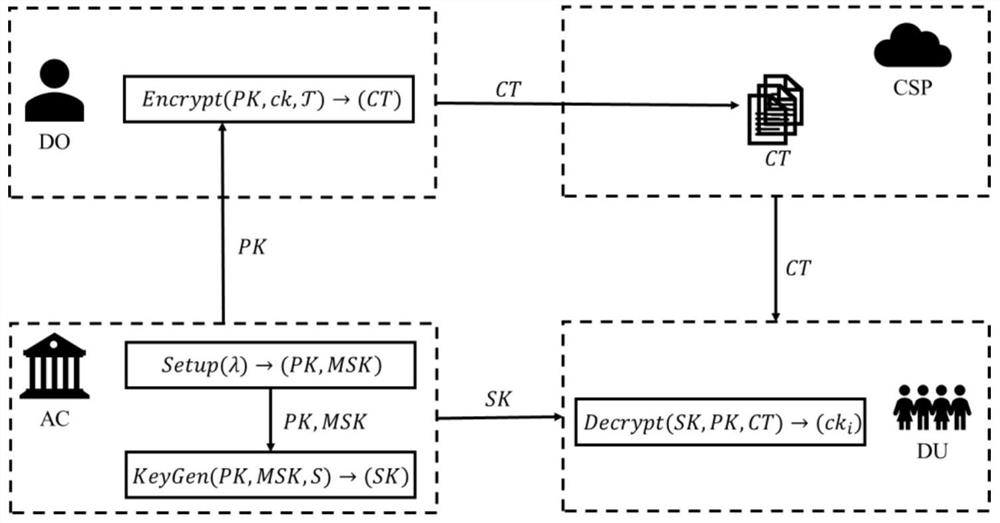
[0113] Such as figure 1 As shown, the present invention provides a layered file encryption system including an authority, a data owner, a cloud service provider, and a data consumer.
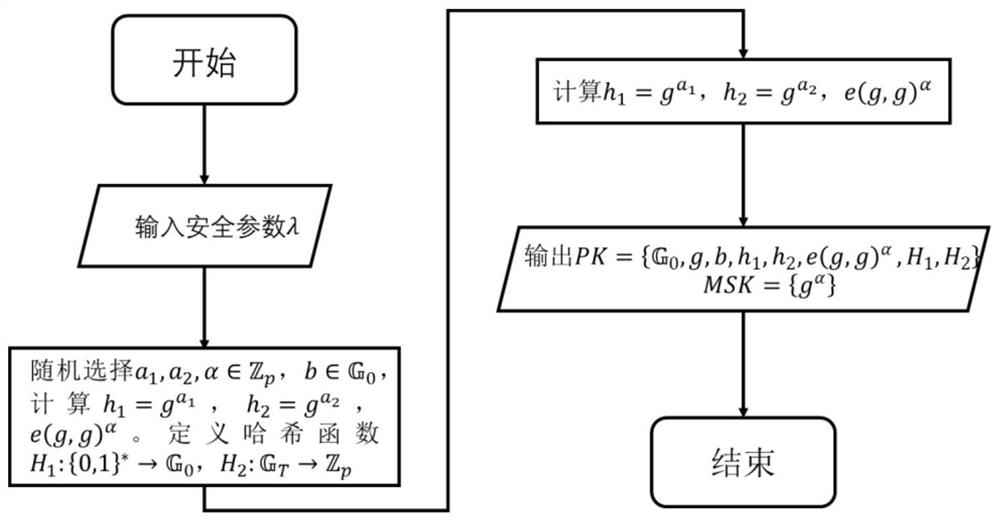
[0114] The authority (CA) is used to calculate and obtain the system public key PK and system master key MSK through the system initialization parameter λ, and obtain the data consumer identity information and the corresponding data consumer attribute set S from the data consumer; based on the system The public key PK, the system master key MSK and the data consumer attribute set S calculate the data consumer private key SK; send the system public key PK to the data owner, and send the corresponding data consumer private key according to the identity information of the data consumer The key SK is sent to the corresponding data consumer.
[0115] The data owner (CSP), used to obtain the system public key PK from the authority, and layer the file ck according to the encryption i Construct a one-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com