Personal data transaction system and method
A transaction system and transaction method technology, applied in the field of information security, can solve the problems of users losing absolute control over data, privacy leakage, etc., and achieve the effect of safe use, reduction of operation steps, and prevention of data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
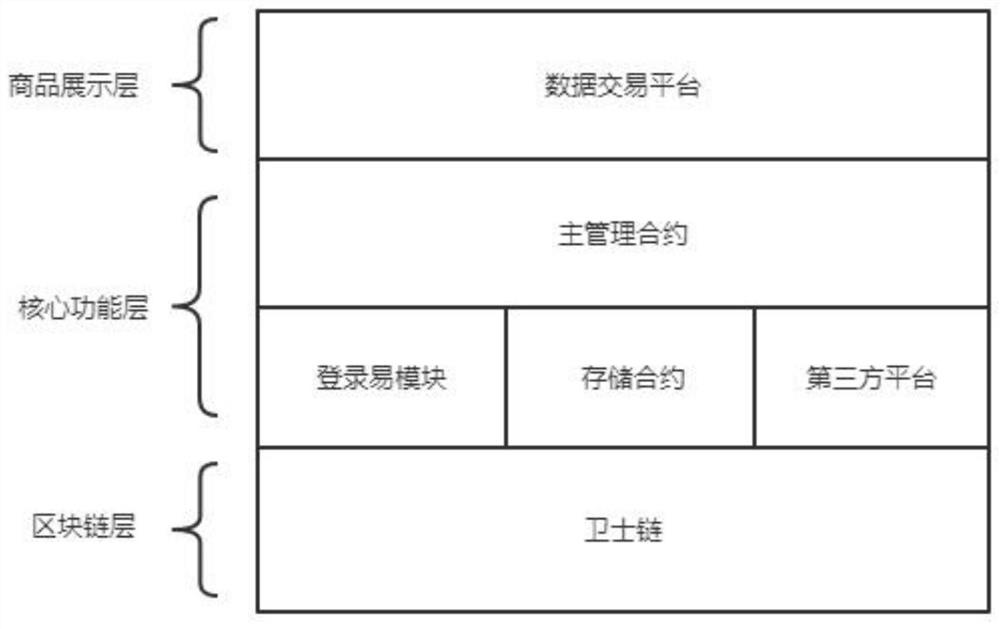
[0035] The system structure in this embodiment is divided into 3 layers, such as figure 1 As shown, from top to bottom is the data transaction layer, that is, the UI layer, which is responsible for displaying basic information on the tradable data on the chain; in the middle is the core function layer, which manages the rights of personal data through multi-layer contracts. The storage and retrieval of is also realized through this layer; the last layer is the blockchain layer. It is used to support the operation of smart contracts and the storage of data.
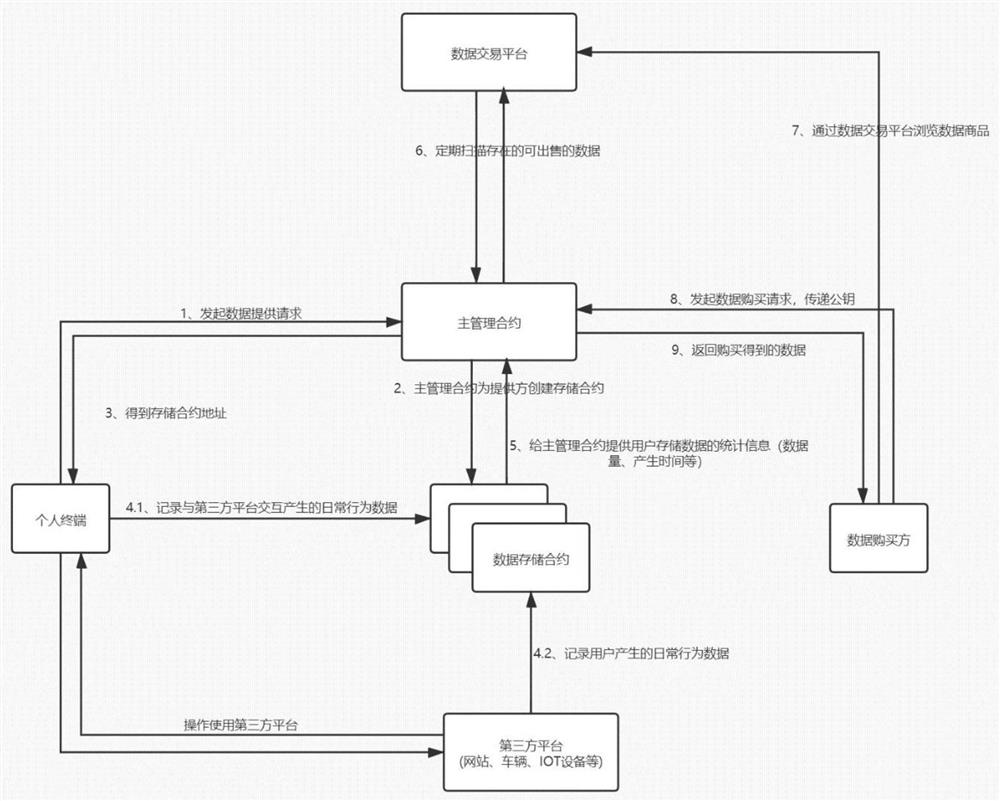
[0036] Among them, the data transaction platform is a display platform for data commodities in the personal data transaction method and system. The data transaction platform displays the basic information of personal user data in the form of commodities. Data buyers search and filter commodities that suit their needs through this platform. , get the seller's address and data attribute description of the commodity, includi...
Embodiment 2
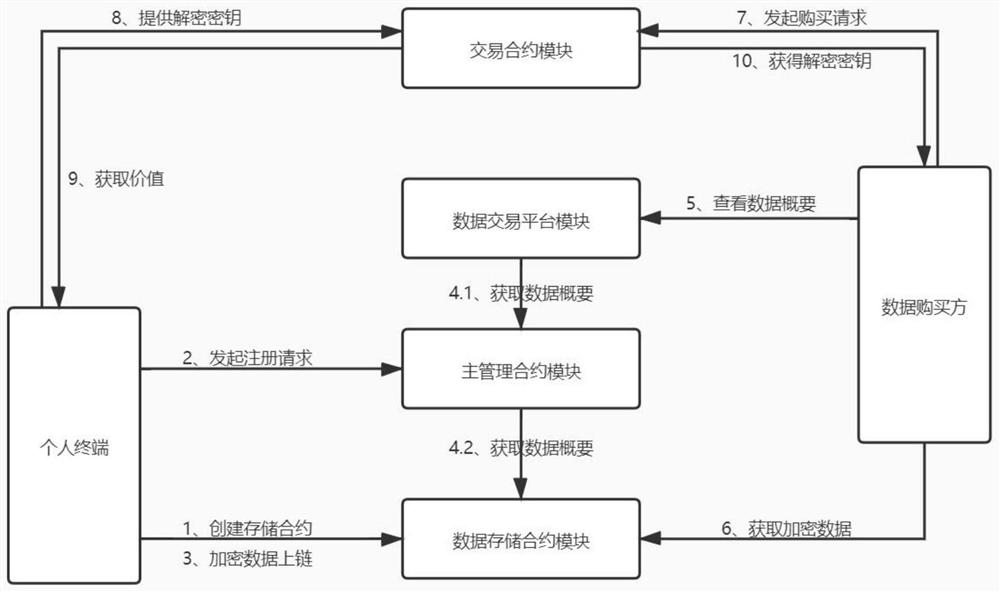
[0063] This embodiment also includes the personal terminal, data buyer, data transaction platform module, and main management contract module in Embodiment 1. In this implementation, the functions of the above modules are not described, and the transaction contract module is also included.
[0064] The difference from Embodiment 1 is that the method for realizing the above system, such as image 3 Shown:
[0065] S1. The user first creates a user management contract and a data storage contract through a personal terminal and uses a smart contract template to obtain the contract address;
[0066] S2. The user initiates a registration request by calling the main management contract on the personal terminal, and registers the personal data storage contract in the main management contract by passing in the contract address;
[0067] S3. The user uses the symmetric encryption algorithm to encrypt the personal data on the chain by calling the data storage contract module on the per...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com