Password cracking effect evaluation method and device, electronic equipment and storage medium
A password and evaluation value technology, applied in the field of password cracking, can solve problems such as information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0030] In order to achieve a reasonable evaluation of the effect of password cracking, a method for evaluating the effect of password cracking is provided in the embodiment of the present application.
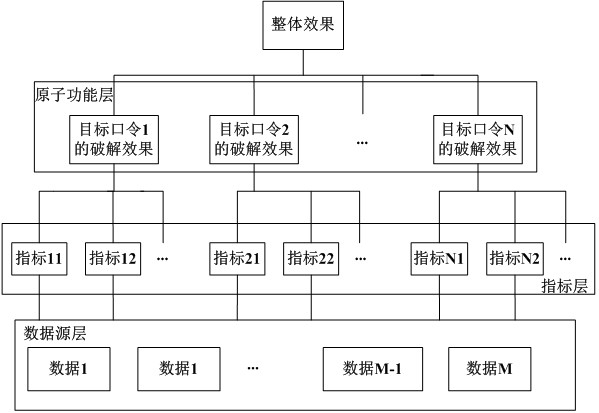
[0031] In order to realize the effect evaluation of password cracking, an evaluation system is provided in the embodiment of this application, which can be found in figure 1 As shown, it includes data source layer, index layer and atomic function layer. Through the data of the data source layer, the determination of each index of the index layer is realized, and then the effect evaluation of the atomic function layer is realized based on the index layer, and finally the overall effect evaluation of the entire password cracking process is realized based on the effect evaluation of the atomic function layer.
[0032] exist figure 1 Based on the evaluation system shown, see figure 2 as shown, figure 2 It is a schematic flow chart of the password cracking effect evaluation met...
Embodiment 2
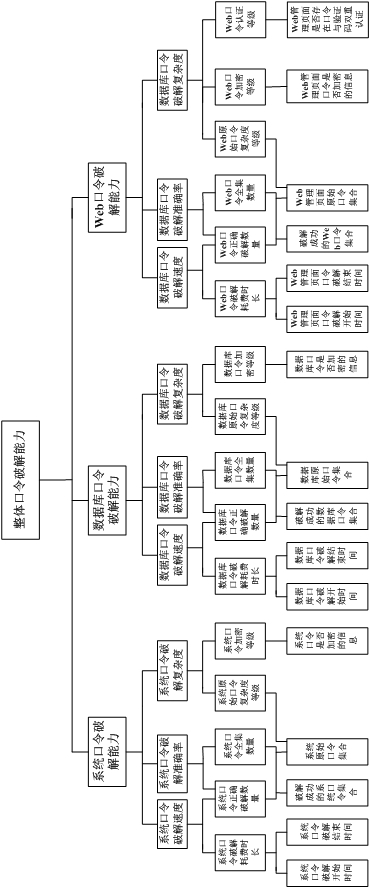
[0074] Based on the first embodiment, this embodiment takes a specific password cracking evaluation system and the process of using the password cracking evaluation system to evaluate the effect of password cracking as an example to further illustrate this application.
[0075] In this embodiment, the password cracking evaluation system can be found in image 3 shown.
[0076] When evaluating the password cracking effect for a password cracking process of a password cracking program, first follow the image 3 The data specified in the data source layer shown in the figure obtains the target system password cracking start time, the target system password cracking end time, the target system original password set), whether the system password is encrypted, the target database password cracking start time, the target database password cracking end time, the target database original password set, the target database password cracking result at the end of the cracking (the success...
Embodiment 3
[0115] Based on the same inventive concept, the embodiment of the present application also provides a password cracking effect evaluation device 100 . see Figure 4 as shown, Figure 4 shows the use of figure 2 As for the password cracking effect evaluation device of the shown method, it should be understood that the specific functions of the device 100 can refer to the above description, and to avoid repetition, the detailed description is appropriately omitted here. The device 100 includes at least one software function module that can be stored in a memory in the form of software or firmware or solidified in an operating system of the device 100 . specifically:
[0116] see Figure 4 As shown, the device 100 includes: an acquisition module 101 , a calculation module 102 and an evaluation module 103 . in:
[0117] The obtaining module 101 is used to obtain password cracking data generated when the password cracking program cracks each target password this time;
[01...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com