A flash memory data protection and restoration method
A data protection and data technology, applied in the input/output process of data processing, electrical digital data processing, internal/peripheral computer component protection, etc., can solve hidden dangers buried in flash memory, data loss, incomplete protection of flash memory data and Repair methods and other problems to achieve the effect of convenient operation, avoiding data loss, and convenient sorting and auditing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
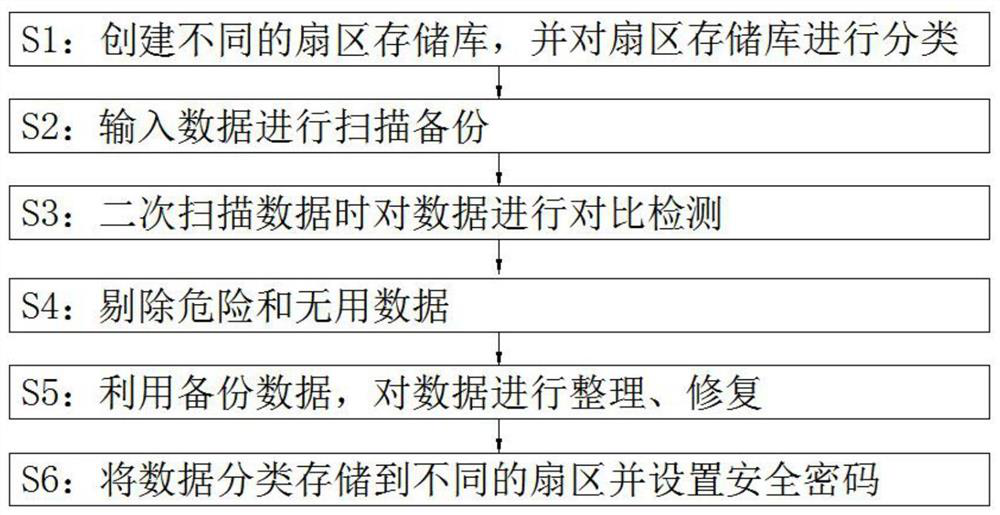
[0027] refer to figure 1 , a method for flash memory data protection and repair, comprising the following steps:
[0028] S1: Create different sector repositories and classify the sector repositories;
[0029] S2: input data for scanning and backup;
[0030] S3: compare and detect the data when scanning the data for the second time;
[0031] S4: Eliminate dangerous and useless data;
[0032] S5: Use the backup data to organize and repair the data;
[0033] S6: classify and store data into different sectors and set a security password.
[0034] In this embodiment, the sector storage library is classified in S1, classified according to time, memory size, and data type, and keywords, data virus templates, and regular data templates are pre-stored in the data input computer calculation.
[0035] In this embodiment, S2 inputs the data into the computer, reads the data when inputting the data, and backs up the read data according to the initial state.
[0036] In this embodime...
Embodiment 2
[0042] refer to figure 1 , a method for flash memory data protection and repair, comprising the following steps:
[0043] S1: Create different sector repositories and classify the sector repositories;
[0044] S2: input data for scanning and backup;
[0045] S3: compare and detect the data when scanning the data for the second time;
[0046] S4: Eliminate dangerous and useless data;
[0047] S5: Use the backup data to organize and repair the data;
[0048] S6: classify and store data into different sectors and set a security password.
[0049] In this embodiment, the sector storage library is classified in S1, classified according to time, memory size, and data type, and keywords, data virus templates, and conventional data templates are pre-stored in the data input computer calculation, and blank memory It is proposed that scanning can be avoided and data reading speed can be improved.
[0050] In this embodiment, S2 inputs the data into the computer, reads the data whe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com