Attack defense device and method based on mimicry defense, equipment and medium
An executive and heterogeneous technology, applied in transmission systems, electrical components, etc., can solve problems affecting system stability, reducing the superiority of heterogeneous redundancy, and unavailability, so as to improve reliability and availability, and reduce restart cleaning , enhance the overall security effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
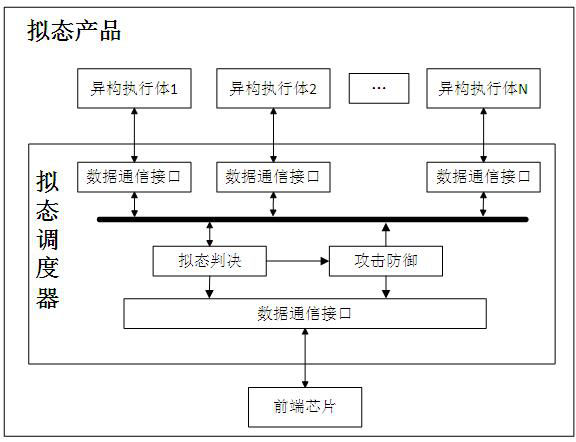
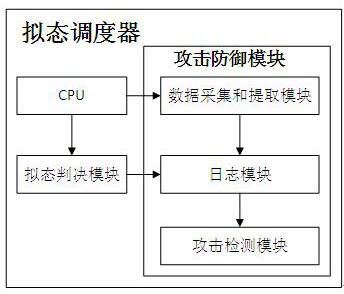
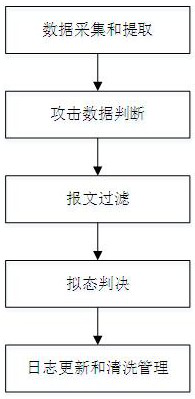
[0088] In this embodiment, a mimetic defense-based attack defense device of the present invention is a mimetic switch, the front-end chip is a switching chip, and a mimetic defense-based attack defense method of the present invention is applied to the mimetic switch, as shown in the attached Figure 4 As shown, the specific process is as follows:
[0089] Step 1: The mimic scheduler in the mimic switch collects the message data sent from the switch chip.
[0090] Step 2: The mimic scheduler extracts key parameters in the message data.
[0091] Depending on the protocol in the message data, the key parameters extracted are also different. In this embodiment, among the message data sent by the switching chip, the protocol is the STP protocol, the OSPF protocol, the RIP protocol, and the TCP protocol.
[0092] For the STP protocol, extract the BPDU message type, flag bit, root bridge ID, root path cost, sender ID, port ID, message lifetime, maximum lifetime, Hello Time, and MAC...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com