APT attack detection method, terminal equipment and storage medium
An attack detection and detection technology, applied in the field of malicious attack detection, can solve the problems of long duration, low APT attack efficiency, and only focus on border defense, etc., to achieve the effect of simplifying the scale
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
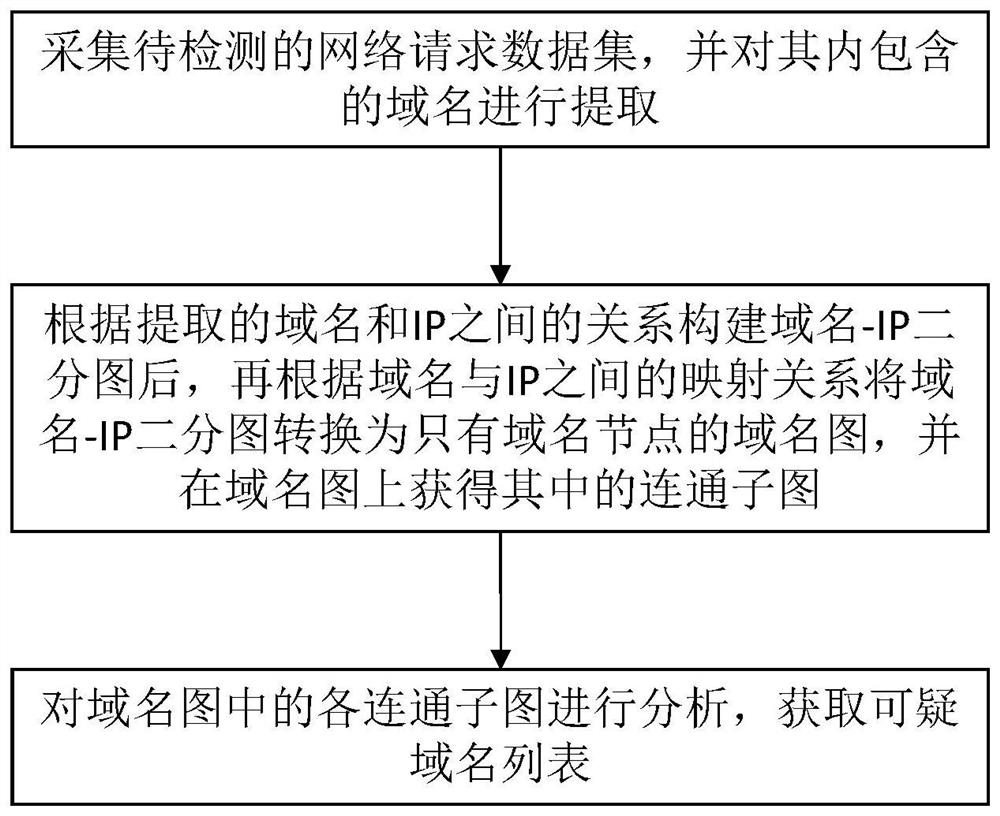
[0038] The embodiment of the present invention provides a method for detecting APT attacks, such as figure 1 As shown, it is a flow chart of the APT attack detection method described in the embodiment of the present invention, and the method includes the following steps:
[0039] S1: Collect the network request data set to be detected, and extract the domain name contained in it.
[0040] The data to be detected used in this embodiment is continuous DNS request information and response data. A DNS request record contains the following information: request time, request host name, request domain name, DNS type and additional information.
[0041] Since the data size of the network request data set is usually large, it is 30GB in this embodiment, which contains a total of 250 million DNS request data (specifically 257535071), including a total of 70,000 domain names (specifically 73136), and the response fails The error domain name 4408. Since it is very difficult to process ...
Embodiment 2
[0080] The present invention also provides an APT attack detection terminal device, including a memory, a processor, and a computer program stored in the memory and operable on the processor, and the present invention is realized when the processor executes the computer program Steps in the above method embodiment of Embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com