Identity-based recoverable message blind signature generation method
A blind signature and message technology, applied in the field of information security, can solve problems such as message transmission overhead, dispute resolution, and adverse effects of behavior tracking, so as to avoid certificate management problems, reduce communication and storage overhead, and reduce system operation and maintenance costs. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to facilitate the understanding of the technical solutions of this patent, in order to make this patent, the technical solutions and beneficial effects are clearer, and the scope of the claims is fully supported, the following is in the form of a specific case. The patented technical solution makes further, more detailed descriptions.
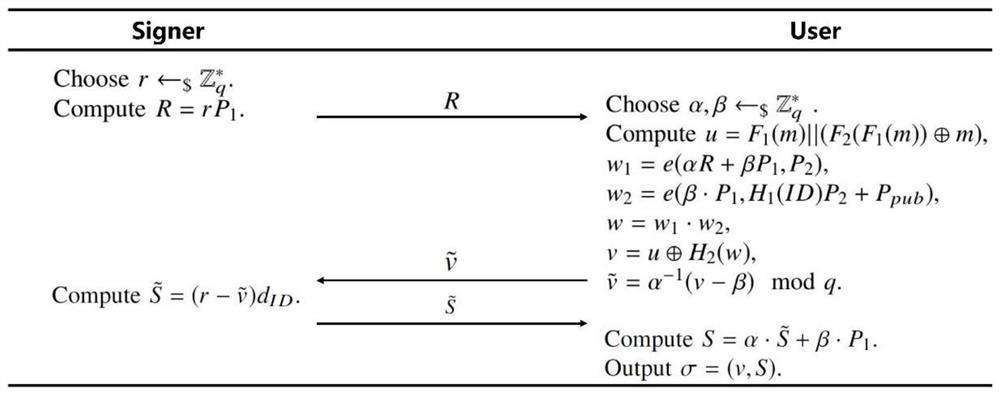
[0032] An identity-based recoverable message blind sign name generation method involves four roles of key generation center KGC, signature, users, and verifiers. First, the system parameter setting and the generation of the system master key are completed by the KGC. Second, KGC issues a private key D corresponding to each signature. ID . After that, in the signature phase, the signature is challenged by the random point R, and the user uses blind factor α, β to the message M blindly Signer again uses private key D ID Correct Signature User Drafage to get the signature σ = (v, s). During the verification process, the validator di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com