Anti-theft method based on dynamic construction of virtual password
An anti-theft method and password technology, applied to instruments, time registers, individual input port/output port registers, etc., can solve problems such as hacking, achieve improved security, and achieve discontinuous effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
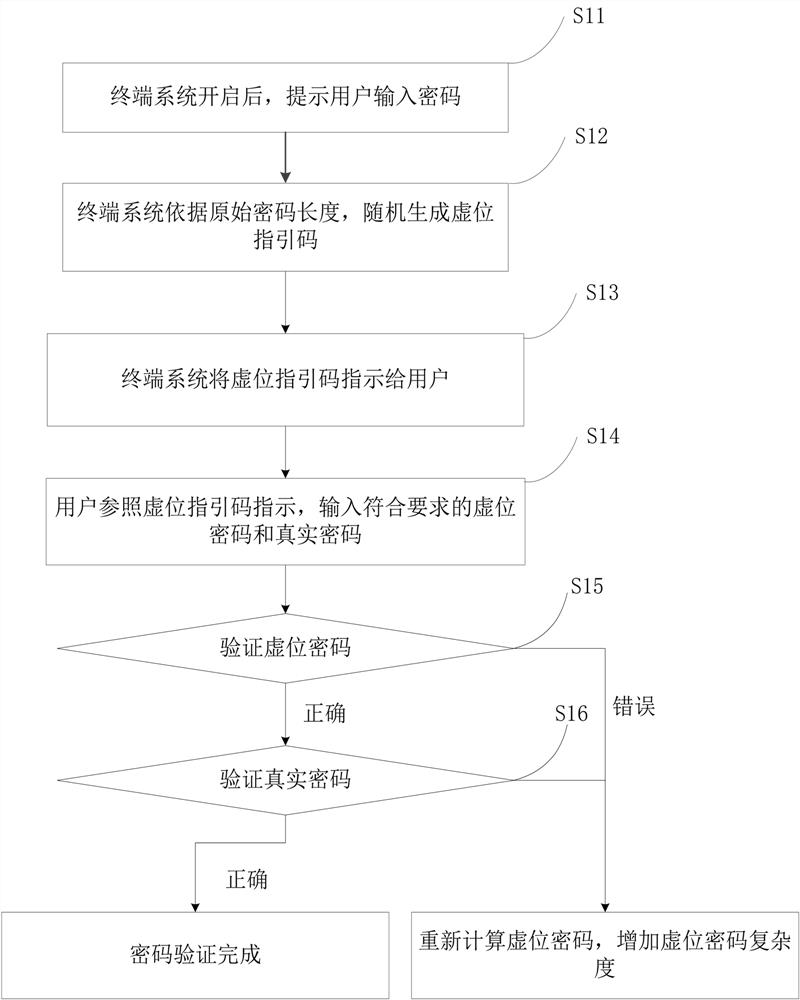
[0031] Please refer to figure 1 , figure 1 It is a schematic flow chart of an anti-theft method based on dynamically constructing a dummy password according to Embodiment 1 of the present invention, and the method includes the following steps:
[0032] In step S11, after the terminal system is turned on, the user is prompted to input a password.
[0033] Step S12, the terminal system randomly generates a dummy index code according to the length of the original password.
[0034] The dummy position of the dummy index code can be in any position of the real password number, and the dummy index code can be expressed in formats such as 1X2XX3456, 123XX4X56X, and X12345X6, where X is the dummy position, and 1 to 6 are the real password positions.
[0035] As a preference, wildcards are used for the phantom position to agree that the phantom is any character, and the wildcard is not limited to X, and legal users can obtain the wildcard from the relevant description information; he...
Embodiment 2
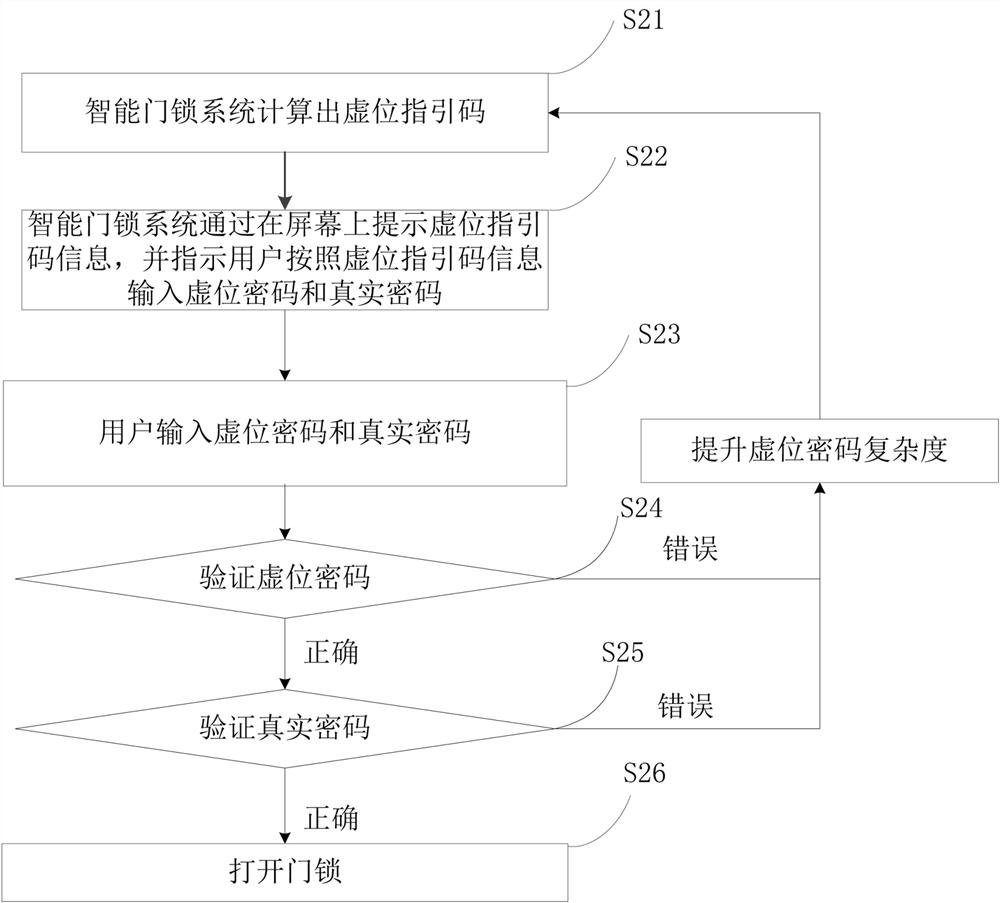
[0048] Please refer to figure 2 , figure 2 It is a schematic flow chart of the anti-theft method based on dynamically constructing a virtual password in Embodiment 2 of the present invention. The method is implemented in an intelligent door lock system, as follows:
[0049] Step S21, when the user activates the smart door lock to unlock, the smart door lock system calculates the virtual index code;
[0050] Step S22, the smart door lock system prompts the virtual position guide code information on the screen, and instructs the user to input the virtual position password and the real password according to the virtual position guide code information;
[0051] Step S23, the user inputs a virtual password and a real password;
[0052] Step S24, the smart door lock system verifies the dummy password, if the dummy password verification fails, increase the complexity of the dummy password, recalculate the dummy password, and prompt the user to input the password again;
[0053] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com