Method and system for logging in Windows operating system
An operating system and the only technology, applied in the field of information security, can solve problems such as insecurity, user names and passwords are easy to be stolen, hardware authentication devices cannot log in, and achieve the effect of expanding the scope of application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0047] This embodiment provides a method for logging into a Windows operating system, including: a binding process and a login process;
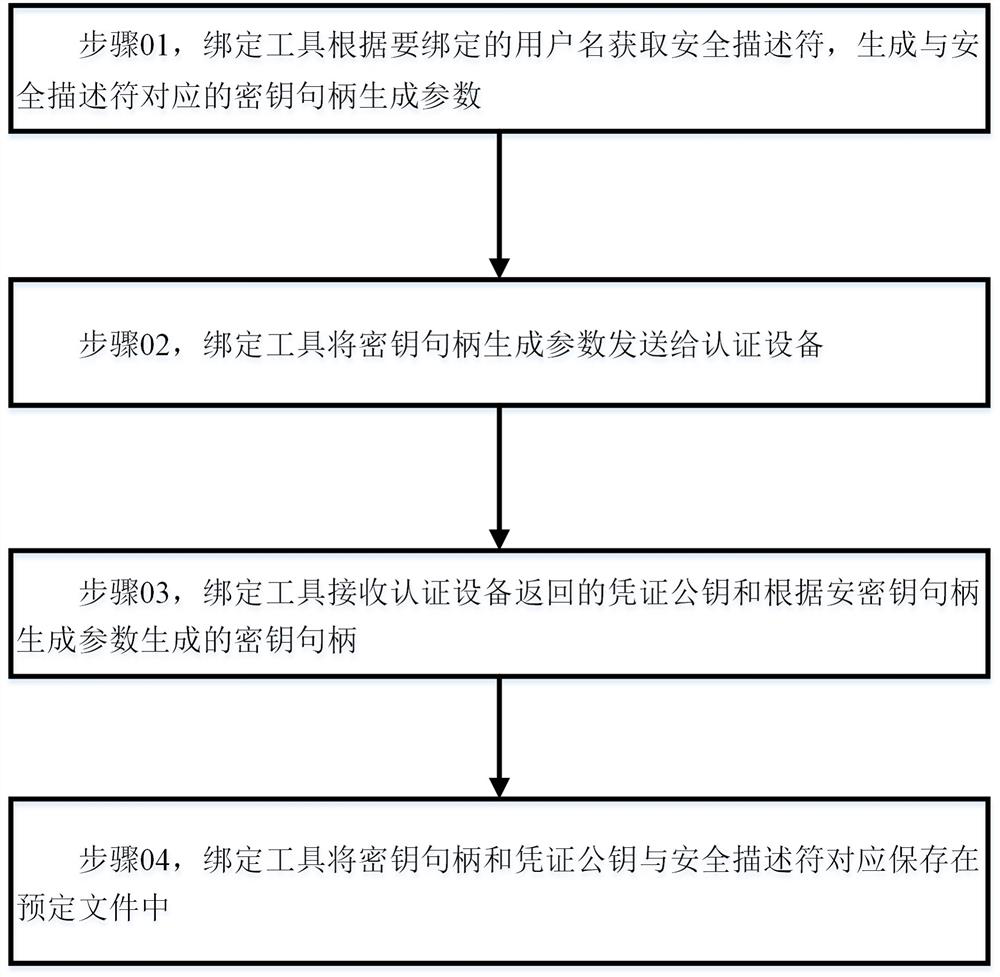
[0048] Such as figure 1 As shown, the binding process includes:
[0049] Step 01, the binding tool obtains the security descriptor according to the user name to be bound, and generates key handle generation parameters corresponding to the security descriptor;
[0050] Step 02, the binding tool sends the key handle generation parameters to the authentication device;
[0051] Step 03, the binding tool receives the credential public key returned by the authentication device and the key handle generated according to the key handle generation parameters;
[0052] Step 04, the binding tool saves the key handle, certificate public key and security descriptor correspondingly in a predetermined file;
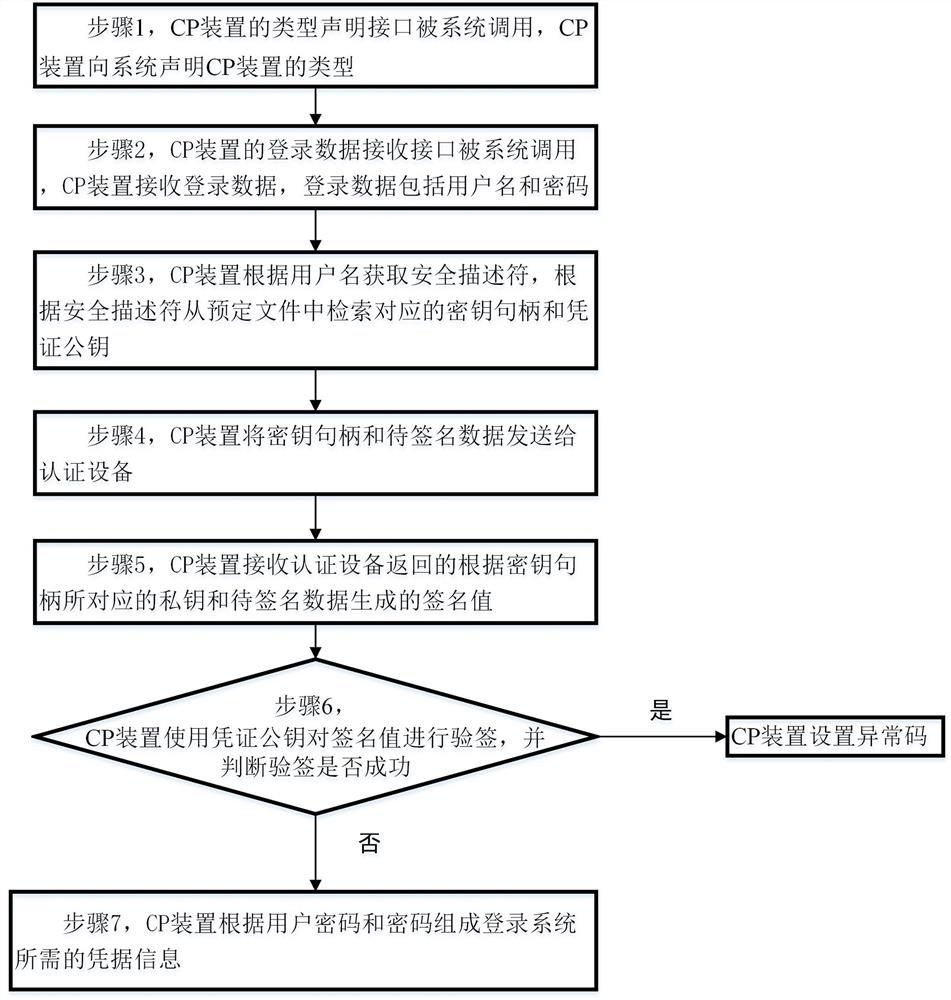
[0053] Such as figure 2 As shown, the login process includes:
[0054] Step 1, the type declaration interface of the CP device is called by the ...
Embodiment 2
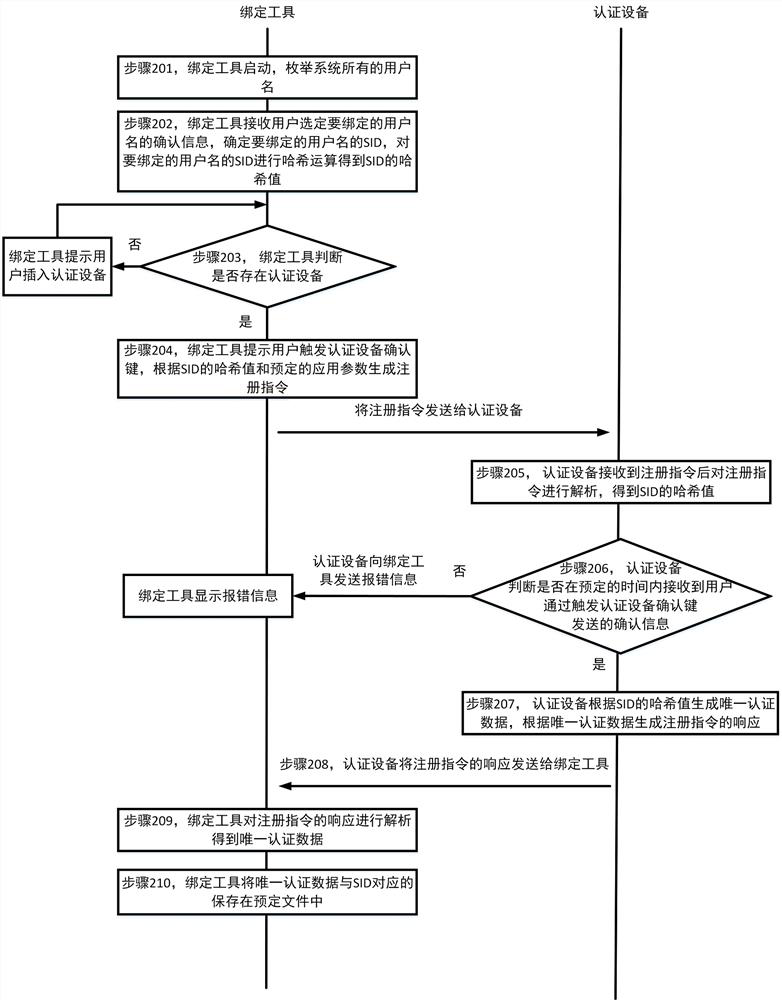
[0091] This embodiment provides a method for logging into a Windows operating system, including: a binding process and a login process, such as image 3 As shown, the binding process includes:
[0092] Step 201, the binding tool is started, and all user names in the system are enumerated;
[0093] In this embodiment, this step may specifically include the following steps:
[0094] Step a1, the binding tool starts, enumerates all user names in the system, and obtains the SIDs of all user names;
[0095] Specifically, in this embodiment, the binding tool calls the NetUserEnum function to enumerate all user names in the system, and calls the API function of the system to obtain the SIDs of all the user names.
[0096] The API function of the above call system to obtain the SID of all user names is as follows: the binding tool uses the user name and Null as input parameters to call the LookupAccountName function to obtain the size of the buffer required for the SID; calls the Lo...
Embodiment 3
[0192] This embodiment provides a method for logging into the Windows operating system, including a binding process and a login process, wherein the binding process adds the following steps after the binding process step 210 in Embodiment 2:
[0193] Step 211, the binding tool generates a unique recovery code related data according to the SID of the user name to be bound, generates a unique recovery code according to the unique recovery code related data and displays the unique recovery code, and combines the unique recovery code related data with the user name to be bound. The SID of the user name is correspondingly saved in the predetermined file;
[0194] In this embodiment, this step is specifically:
[0195] Step c1, the binding tool generates the first random number and the second random number;
[0196] Step c2, the binding tool sequentially concatenates the first random number, the SID and the second random number to generate unique recovery code related data;
[019...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com