Secret key generation method based on channel fingerprints and auxiliary data
A technology for auxiliary data and key generation, applied in the field of information security, can solve problems such as leaking key information, and achieve the effects of ensuring communication security, improving restoration success rate and security, improving randomness and restoration reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
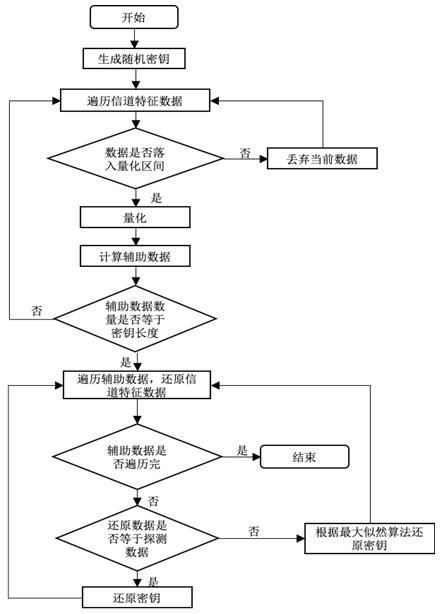
[0026] A key generation method based on channel fingerprints and auxiliary data, such as figure 1 shown, including the following steps:
[0027] (1) random key generation;
[0028] During specific implementation, a key is generated by an RNG random number generator for use in an encrypted communication system.
[0029] (2) The sender traverses the channel characteristic data to determine whether the data falls into the quantization interval;
[0030] In this embodiment, the sending end sequentially traverses the collected channel characteristic data; the quantization interval is
[0031]
[0032] In the formula, s is the number of key bits, Represents the distribution function of the channel characteristic data, p t = 1 / t.
[0033] (3) The sending end uses a zero-leakage quantization method to quantize the channel characteristic data;
[0034] During specific implementation, step (3) specifically includes whether the currently traversed channel characteristic data fa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com